Home Search
kali - search results
If you're not happy with the results, please do another search
How to Install Honeypot on Kali Linux
In this article we will show how to install Honeypot in Kali Linux. The Pentbox is Security suite that can be use for penetration testing...
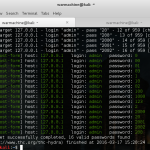
How To Crack Web Form Passwords Using Hydra With Burpsuite In Kali Linux
In our previous article How To Crack Password Using Hydra In Kali Linux , we have discussed about THC Hydra- A tool for Online Password attacks. In...
How To Crack Password Using Hydra In Kali Linux
Weak password is still a big problem in the world of security. User need to set a strong password to restrict the access of data...
Kali Linux Rolling Edition updated with the latest patches
The most popular Kali Linux was released on 2015 at DefCon 23 in Las Vegas. Kali is successor of Backtrack based on Debian ...
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
The most popular Kali Linux was released on last week at DefCon 23 in Las...
Step-by-Step Guide to Install Kali 2.0 Linux in VMware workstation 11
The New Kali 2.0 codename as Kali Sana, is an open-source penetration testing platform having pre-installed hundreds of Hacking ,Reverse Engineering, Forensics and Penetration...
Managing Kali Linux Services
Managing Kali Linux Services
Kali Linux is a specialized Linux distribution aimed to test Network. The default Kali installation comes with several services preinstall like...
Important things to do after installing Kali Linux
There are small set of important softwares that are required after installation of Kali Linux. Linux operating system is not too much user friendly...
Complete Guidance to Install Kali linux in Dual Boot Mode without any Problem
Before start Complete Guidance to Install Kali linux in Dual Boot Mode without any Problem remember it's slogan:-
The Quiter you become ,the more you...
Find Hidden Device with arp-Scan
Hidden device with arp-scan
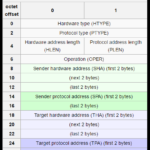
ARP (Address Resolution Protocol) use to map IP network address to the hardware address. Address Resolution Protocol use a message format...
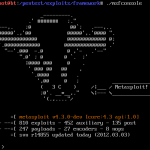
Explore and Search Exploit in Metasploit
Metasploit having a big name, when we talking about security. Metasploit was written in Perl as a portable network tool, In 2007 the Metasploit...
Program to Implement Stacks using structures in C/C++ Programming
In previous post Stacks in programming and Basic Exploits : Stack Operations, we explained the functioning of stacks. Later our users ask for its...
Windows 10 may have hidden linux subsystem
If you remember, in the end of last year every one was impressed from the announcement by Microsoft "Microsoft loves Linux". Microsoft also added...
Intex Aqua Glam is designed specially for female crowd!!
Intex Aqua Glam is designed specially for female crowd!!
Intex has finally launched his new Aqua Glam Smartphone in indian terrorities. The cellphone is the...
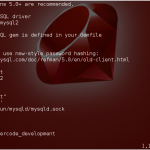
ROR Tutorial : Rails with Mysql Configuration
Many of our users get error in establishing connection with mysql or some other configuration for mysql, so I decided to make this tutorial...
Ruby On Rails Tutorials : Creating new project in Rails
Pr-request for Ruby on Rails tutorials
Install linux Operating-System from here .
Install RVM , Ruby and Rails...
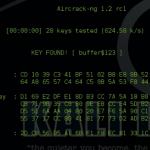
Hack WPA2 Encrypted Wi-Fi Networks using Aircrack-ng
Hack WPA2 Encrypted Wi-Fi Networks using Aircrack-ng | Kali-Linux
Hello friend ,In this article I will demonstrate how to crack or hack some one's WiFi...
Step by Step procedure to install RVM , Ruby and Rails on your linux...
RVM , Ruby , Rails and You
This tutorial is specially for RVM, Ruby , Rails and You . It's really difficult to setup development...
Ethical Hacking
Note: Hacking is not a joke so please keep patience and learn it step by step.
LEARN HACKING
Install Kali linux in Dual Boot
...
Explore into the Metasploit ( a Ultimate Hackers Tool)
Metasploit is a complete and a Ultimate Security tool that provides information about Computer Security Vulnerabilities and also use in penetration testing .It was...
Exploit Development Process:Moving towards Real world Hacking
Now that we have covered basics of exploit , you are ready to look at real world examples like metasploit . As you all...
Micromax YU Yureka will receive Lollipop 5.0 soon!
Howdy friends, Today i hear that brand YU that is tide up with micromax is going to provide android update
for Micromax YU Yureka it...
How to secure your account from phishing attacks on Internet
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Creating Phishing page to know the safety cautions
on Internet
To know...
Top Penetration Testing Application for Android Mobiles
Android is a Linux based small operating which runs on mobile. Most of the user in the world are using Android because of its...
Top Linux distribution 2013 for different Purpose
Top Linux distribution 2013:
In Linux lots of varieties are there if you want to install a free operating system that is Linux other than...
How to use backtrack
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Before you start
Before we start playing with safty tools follow...