Exploit Development Process:Moving towards Real world Hacking
Now that we have covered basics of exploit , you are ready to look at real world examples like metasploit . As you all know - vulnerabilities in real...
What is Ransomware and How it works?
Attackers use ransomware to get ransom from its victims. In other words, ransomware is a malicious program or software to block user access on their own system or encrypt...
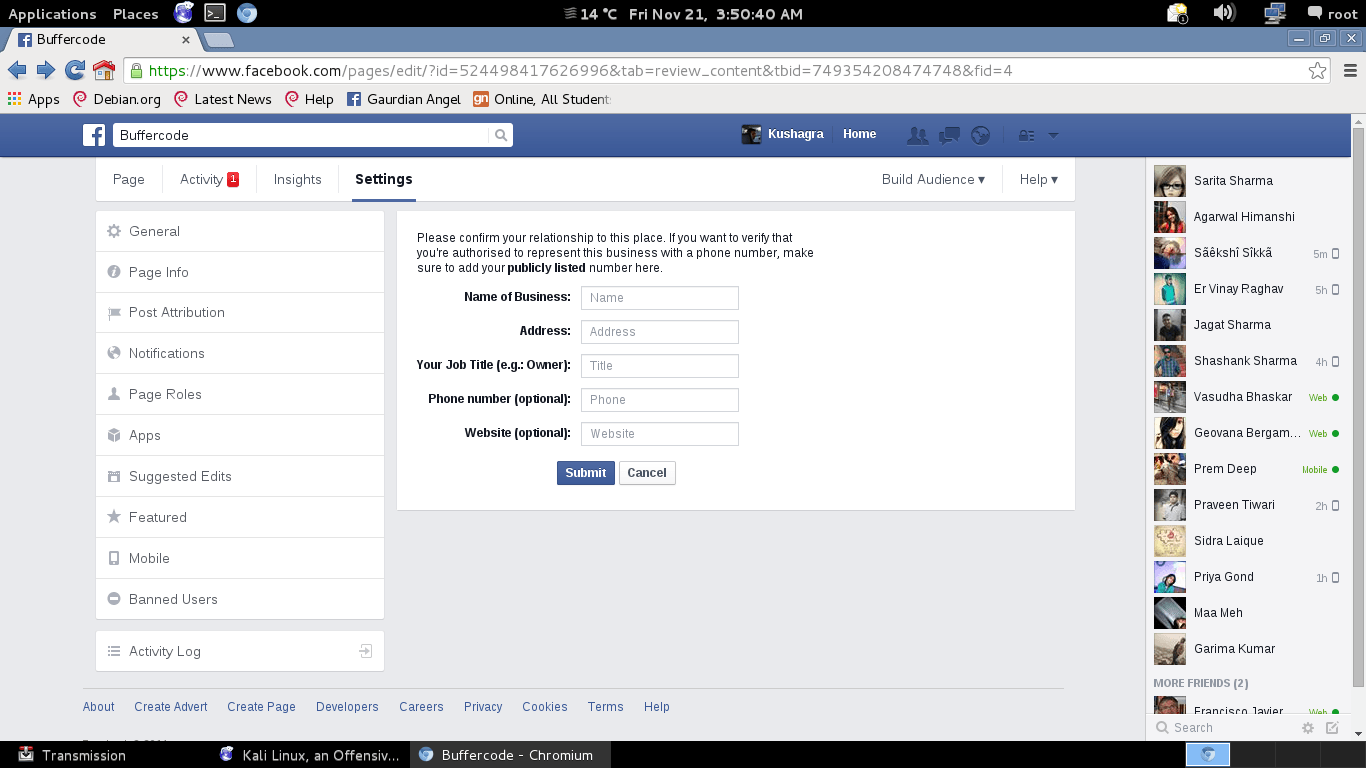
Facebook verification page has bug found by team Buffercode
Note: I already send report for this bug , I hope Team Facebook will change their algorithm for this page.
New Bug has found by team Buffercode in Facebook
It's always...
Kali Linux Rolling Edition updated with the latest patches
The most popular Kali Linux was released on 2015 at DefCon 23 in Las Vegas. Kali is successor of Backtrack based on Debian Jessie,distribution, includes many popular penetration...
An Almost Impossible To Detect Phishing Attack Using Punycode
In our previous article How to secure you account from phishing page, we discussed about how to create and detect whether a page is a phishing page or original...
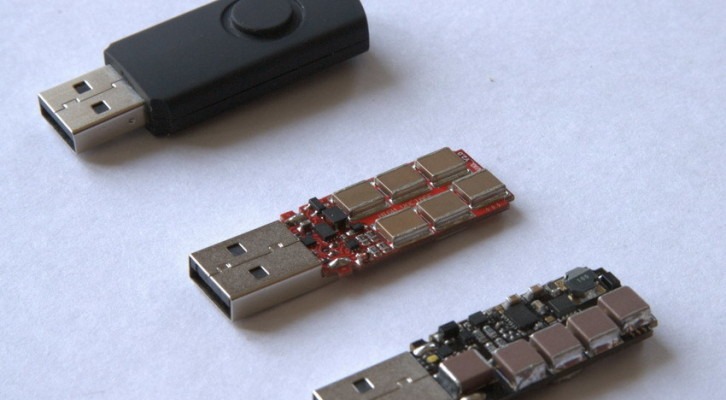
USB Killer 2.0 : It can destroy your system in just some seconds
Do you remember Killer USB? It is about the new version of Killer USB, this time with tremendous powers.
Let’s talk a bit about the previous version of Killer USB,...
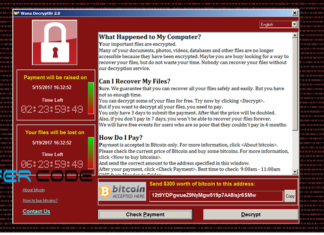
WannaCry ransomware attack: Largest Ransomware Attack In The History
By now, we are sure that you have heard something about wannacry ransomware. There may be a lot of questions in your mind such as What is wannacry ?...
Hackers Attacked Microsoft Outlook Web App to steal Login Credentials
Hackers Attacked Microsoft Outlook Web App to steal Login Credentials
Researchers have recently founded a hazardous Backdoor in Microsoft’s Outlook Web Application, which allows the hackers to steal e-mail and...
What is Sandboxing and How it works?
In this article, we will discuss sandboxing, how it works and list of free sandboxing environments, etc. Hybrid analysis, Malware analysis, and Threat analysis, they all use the same technology...
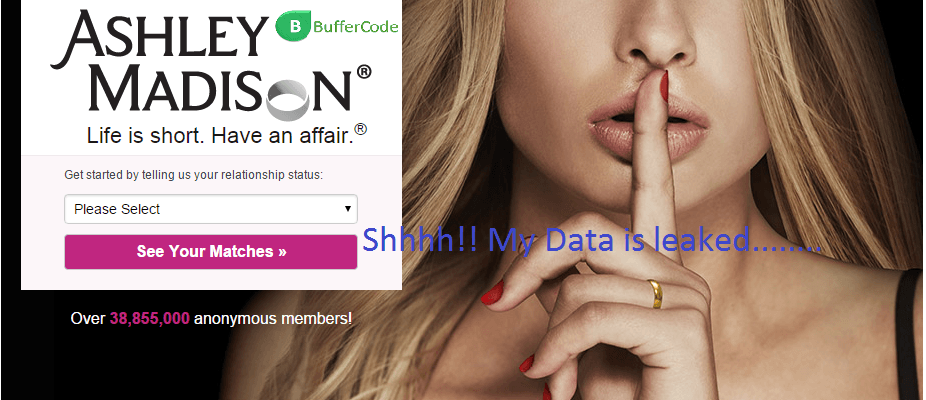
Shocking secrets about Ashley Madison: Women were actually not using the website
The hacked data of Ashley Madison website is been a reason for many criminal activities since it’s data is dumped on to the dark web (also known as deep...
Phishing malware crashes ICICI bank
#Phshing Malware crashes ICICI bank .... https://t.co/a8vTOVvuob
— Buffercode (@buffercoding) February 25, 2016
Official @ICICIBank_Care reply to tweet :
@buffercoding Hi, ICICI Bank has a robust & multi-level security system for all its banking...
Finally Hackers Dumped Stolen Ashley Madison Data Onto Dark Web
Ashley Madison, the largest cheating website with the tag line " Life is short. Have an affair " was hacked by the group of hackers called itself The Impact Team . And...
Demonbot is on rising | A New Botnet
As security is getting stronger so hackers are getting more stronger. Once a loophole is closed by Operating systems or any vendors then hackers find out another way to breach...
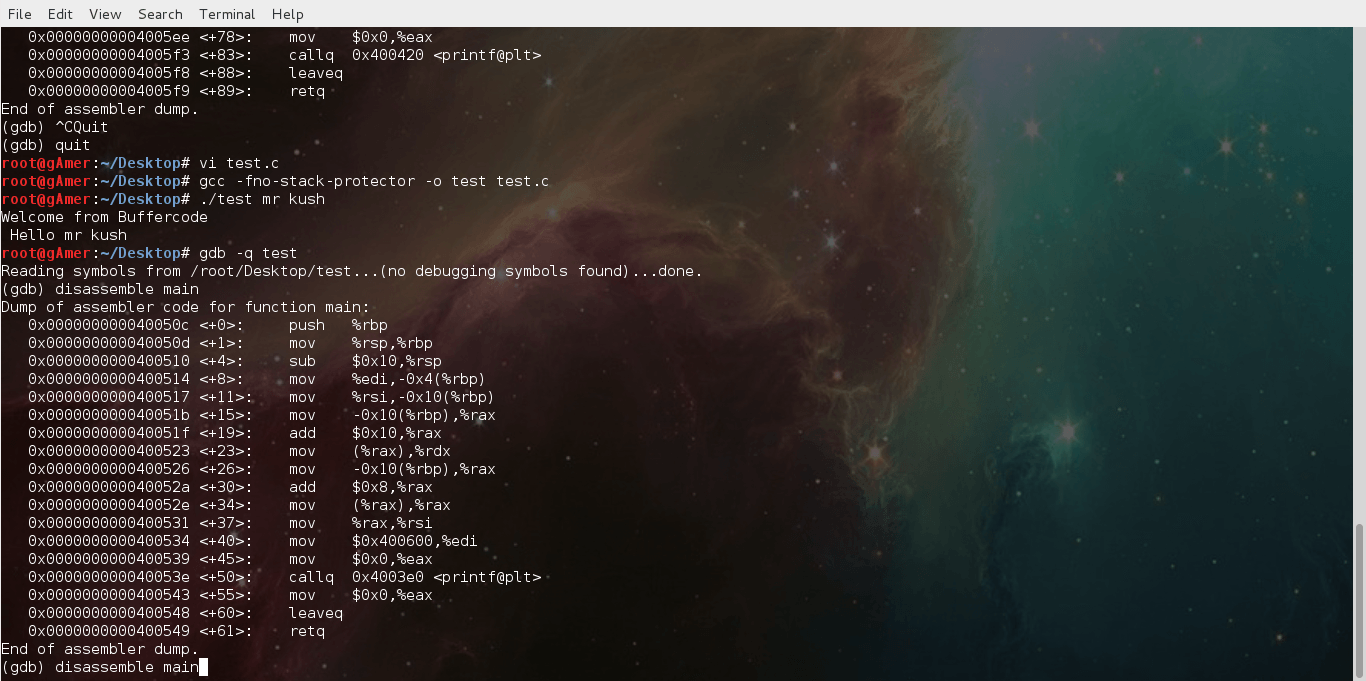
Next step towards exploit : finding the return address
Hey friends , I think it's the time to take next step towards exploit after reading our all previous posts . In this tutorial you will learn about :...
Top Free Vpn Provides 2016
A VPN (Virtual Private Network) extends your private network across a public network, such as a company internal network. There are several numbers of system that enables you to...
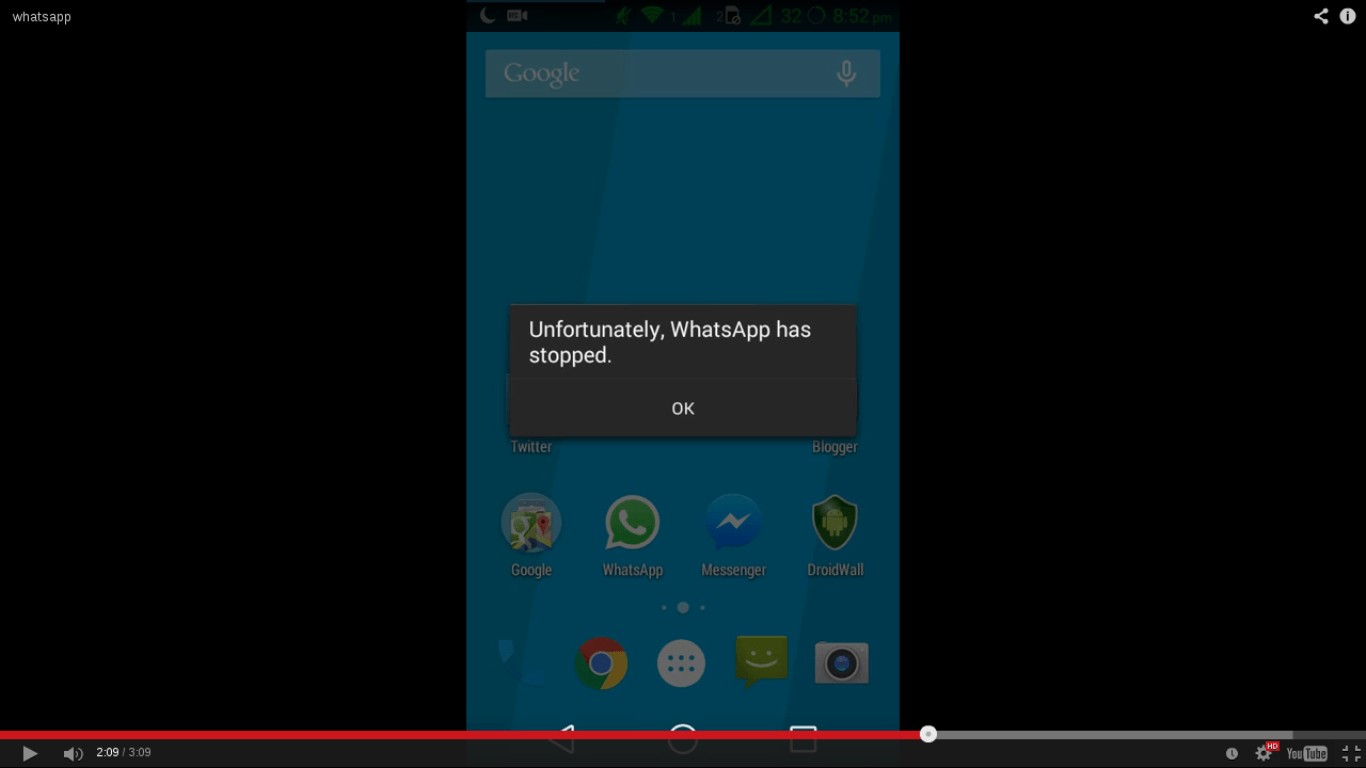
Security Flaw found in WhatsApp : 200 million users are at Risk
Security Flaw found in WhatsApp: 200 million users are at Risk
You will be shocked to know that about 200 million users of the world’s most famous instant messaging service...
Basic Linux exploits: Function Calling Procedure
Note: Hacking is not a joke so please keep patience and learn it step by step.
Note: Before reading this post you must read :
Learn hacking...
Is Dropbox safe against Ransomware and Hacks?
Imagine backing up your sensitive data on Dropbox and one fine morning, finding out that your password has been leaked or you are locked out of your account and...
WikiLeaks to publish the content from CIA’s Director Email
You must have visited the website of WikiLeaks, the non-profit and transparency organisation to read about the leaks and top secrets of this world.
And now Julian Assange, the founder...
Now facebook introduced new “Facebook groups app” on 18 November
Facebook groups app for facebook lovers:
Peoples use facebook to keep contact with friends and family who may live far from them or not. To keep in contact with friends...
PlayStation Hacked! Hackers managed to run Linux on PS4 gaming Console
PlayStation Hacked!
This might be the craziest thing done in the world of gaming, when some hackers hacked Sony’s PlayStation gaming console to run Linux.
This console hacking goes by the...
WordPress XML-RPC: Brute Force Amplification Attack
It is always interesting to hear about the bugs in world’s most famous systems, this time it is WordPress. Yes the world’s most famous content management system is vulnerable...
Radio Wave Hack: It allows the hacker to control your phone from 16 feet...
Every day we get to know about a different hack and every hack has its own dependencies and capabilities.
Now, this is crazy. Security researchers have discovered a new hack...
Bitport Review : Download torrents to your cloud and play them online
Bitport.io review :Most of the people here use torrent to download movies, games , series , software and much more. But there is a question is it safe to...
Malware Attack on Facebook effect more than 110,000 users
Malware attack on Facebook
On Friday malware attack on Facebook is reported. Malware attack on Facebook infected more than 110,000 users. There are some pornography links on Facebook. When user click...
Mac Malware: Time to test Apple’s Security
Last quarter shows an interestingly spike in malware activity that targeted Mac users only. New samples in the 1st 3 months of this year are nearly equal to the...