Finally Hackers Dumped Stolen Ashley Madison Data Onto Dark Web
Ashley Madison, the largest cheating website with the tag line " Life is short. Have an affair " was hacked by the group of hackers called itself The Impact Team . And...
What is Ransomware and How it works?
Attackers use ransomware to get ransom from its victims. In other words, ransomware is a malicious program or software to block user access on their own system or encrypt...
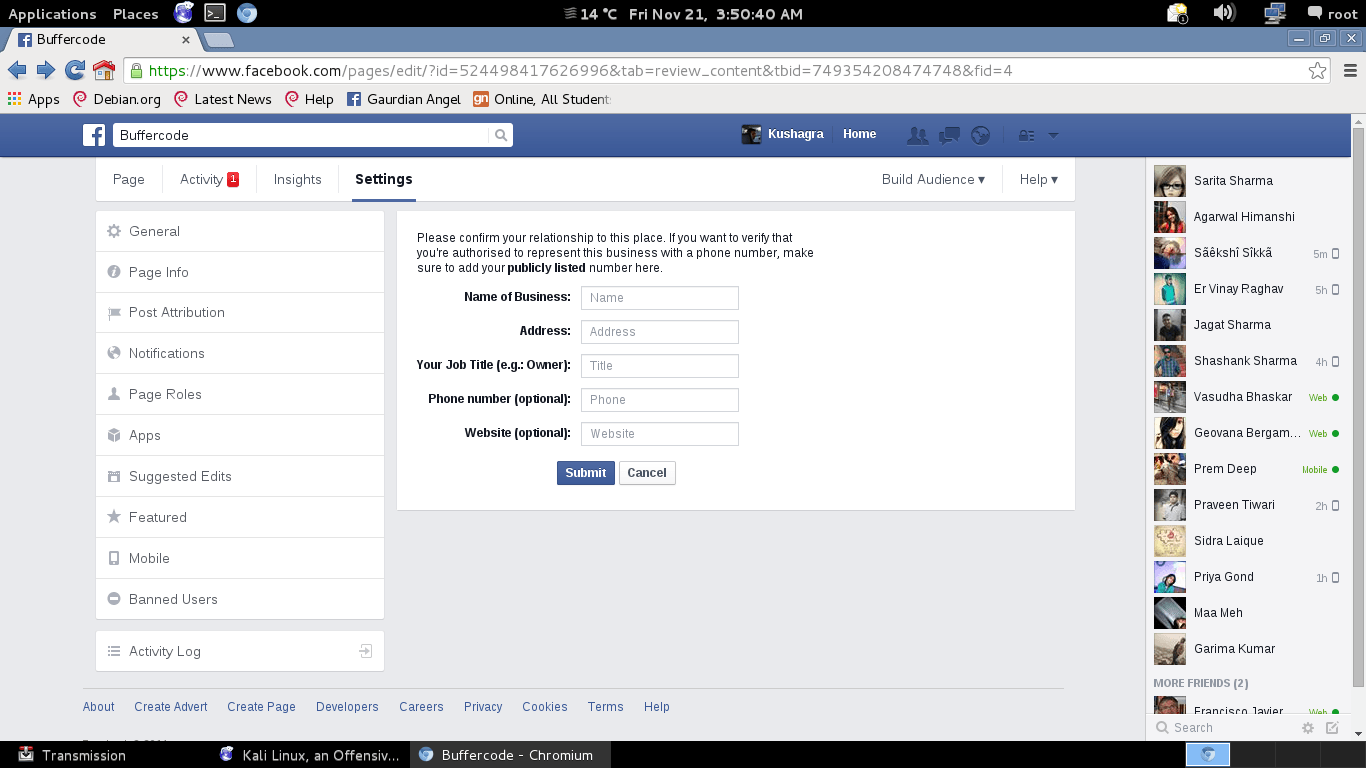
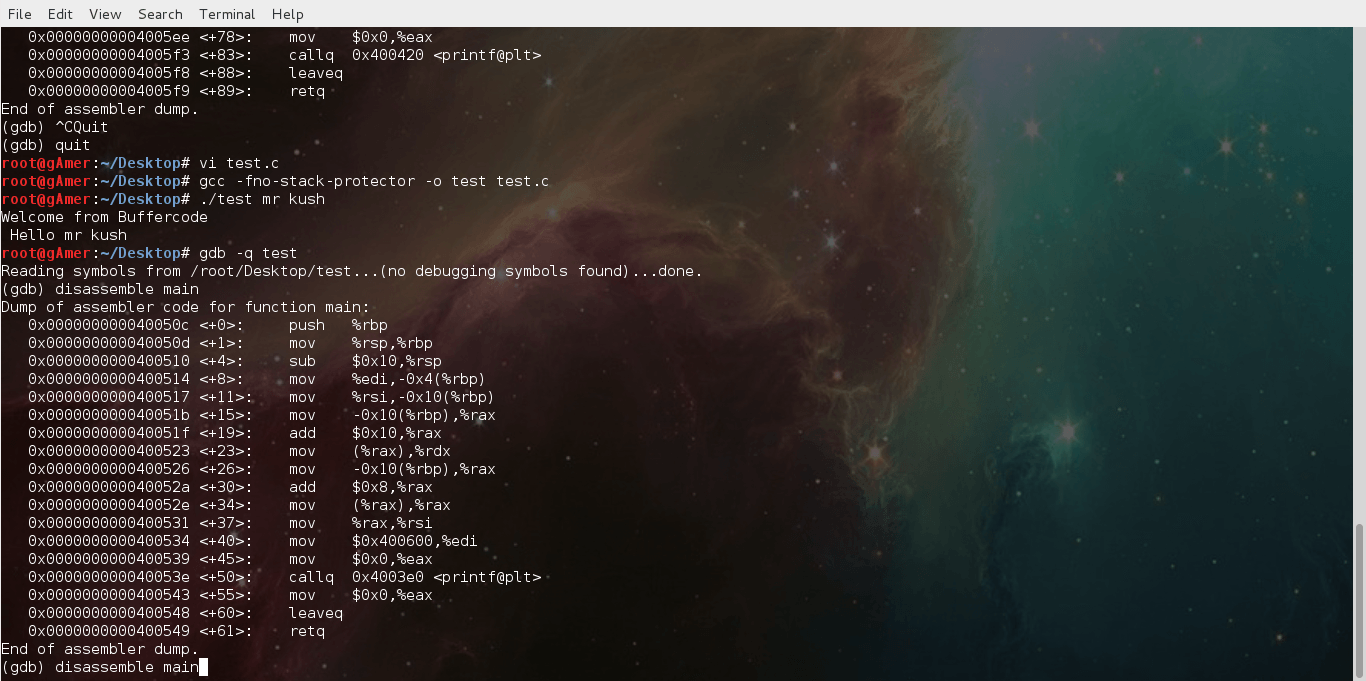
Facebook verification page has bug found by team Buffercode
Note: I already send report for this bug , I hope Team Facebook will change their algorithm for this page.
New Bug has found by team Buffercode in Facebook
It's always...
Security Flaw found in WhatsApp : 200 million users are at Risk
Security Flaw found in WhatsApp: 200 million users are at Risk
You will be shocked to know that about 200 million users of the world’s most famous instant messaging service...
How to hack windows password
How to hack windows password
Change your password if you Forget it
Hello friends today we learn how to change your password if your account or change windows password is locked/you forget your password.At that...
Managing the Safety and Security of Sensitive Documents
The digital era has made it effortless and more efficient to conduct business than ever before, be it in a local space or on a largely worldwide scale. In...
US Intelligence Chief Hacked by a teen
The email of US Intelligence Chief Hacked!
The same teenager who hacked the AOL email of CIA Director John Brennan back in October last year has now hacked into personal...
Hackers Attacked Microsoft Outlook Web App to steal Login Credentials
Hackers Attacked Microsoft Outlook Web App to steal Login Credentials
Researchers have recently founded a hazardous Backdoor in Microsoft’s Outlook Web Application, which allows the hackers to steal e-mail and...
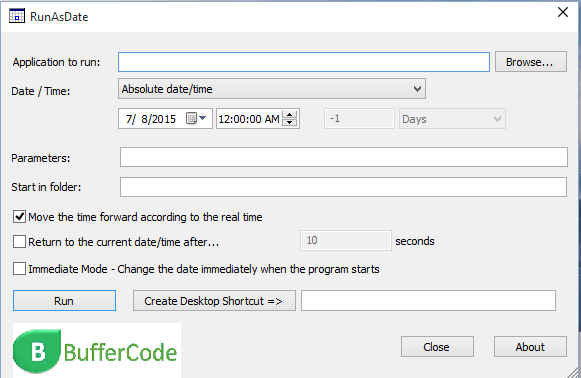
Trick to hack trial version software using RunAsDate utility tool
Here we will discuss a trick about how to hack trial version software in Windows based operating system. It is not exactly hacking of software instead you can call...
Learn hacking for free on buffercode
Start from 15/Nov/2014 see here Basics Linux exploits
To learn hacking is art , and to do hacking is also an art . Similarly friends to teach hacking is an...
$ 500,000 Reward For Impact Team Information :Ashley Madison Hack Has Become A Reason...
In our previous article Finally Hackers Dumped Stolen Ashley Madison Data Onto Dark Web we told you why the group of hackers dumped Ashley Madison's Data on dark web which includes...
How to surf web anonymously ??
Continue with our previous post How to surf web anonymously ......
Today i am going to tell you one of the best solution to surf web anonymously...
In my personal point...
TalkTalk Cyber-attack: Another teenager arrested in London
Another teenager arrested in London.
This time the British police arrested a 16 year old boy from Feltham in West London in case of TalkTalk data breach.
On Monday, Metropolitan Police...
Attackers are using facebook messenger to spread Locky Ransomware
Any Facebook message with an image file (.svg format) send by your friend can be a Locky Ransomware file, so just avoid clicking it.
What is Locky Ransomware?
Locky is ransomware released...
Apple refused to unlock the iPhone on the enforcement of U.S Federal Judge
Once again the tech giant Apple has proved that how much they are concerned about the privacy of its users, and they will never break the users’ security for...
Stone tether smallest tracking device finds your lost items
Stone tether smallest tracking device:
Technology has made life easier if you fail to remember something. A new device is becoming to discover your lost items. Its name is stone...
The Trojanized Adware: It can automatically install apps to your Android Device
What sort of apps do you install on your Android Smartphone?
I hope the trusted ones. Now, what if someone installs a malicious app on your smartphone without your permission?
It...
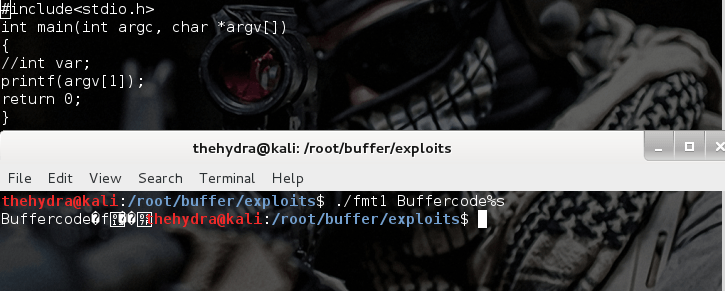
Format string exploits
Format string exploits became public in late 2000. It is easy to find errors in format string in comparison of buffer overflows. Once errors are spotted, they are usually...
Basic Linux exploits: Function Calling Procedure
Note: Hacking is not a joke so please keep patience and learn it step by step.
Note: Before reading this post you must read :
Learn hacking...
StageFright 2.0 Fixed: Google released an OTA for Nexus Devices.
StageFright 2.0 Fixed
Few days back, the researchers warned google of the new Stage Fright Bug. This bug affected more than a billion devices that are running on Android OS.
This...
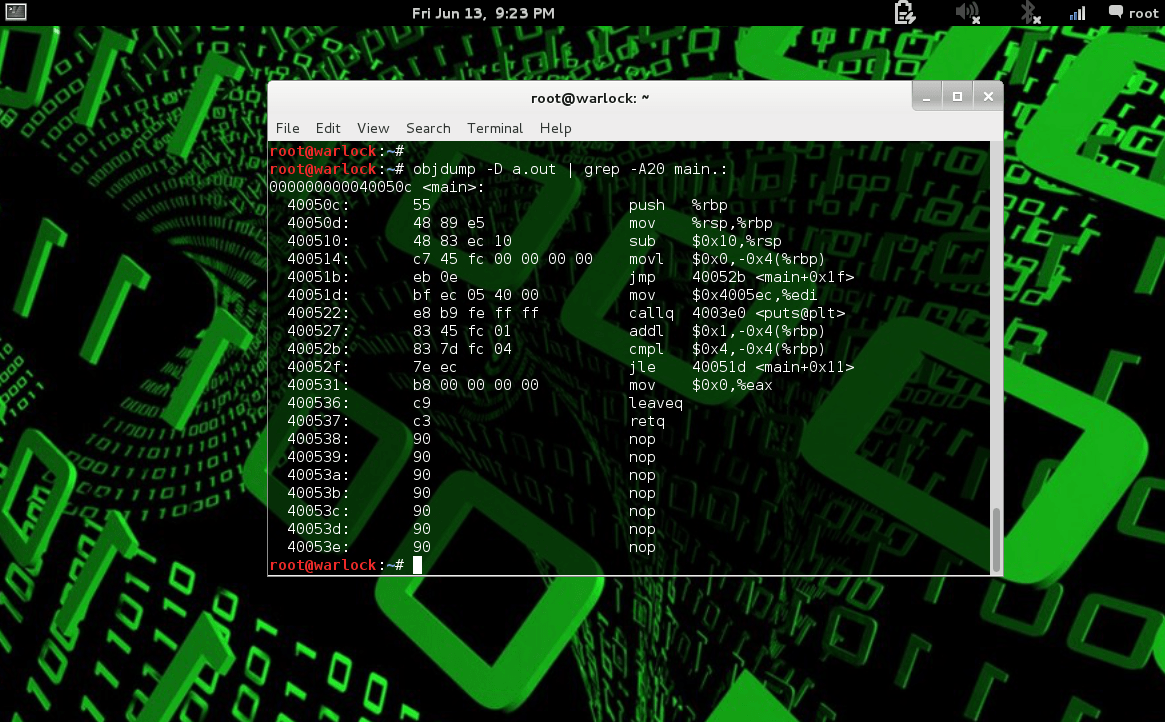
How to use Debugger tool objdump in Linux
Debugger Tool Objdump in Linux
Debugger Tool objdump: C feel more familiar and C compiler exist in every operating system .Basically Linux is a free operating system that every has...
Android Banking Trojan Hiding In Apps Under Different Names: Targeting over 420 apps worldwide
Beware if you recently have installed any funny video application from Google Play Store as it may contain android banking Trojan.
Most of the people love to watch funny videos...
How to surf internet Anonymously
Hello friends this post is about how to hide your machine IP for surfing internet Anonymously. To read this may bore you but keep patience because it is important....
How to make sure a file is safe or threat? | How to do...
Today, we will discuss how to find, a file is safe or a threat for your system?
Or we can say, how to do malware and threat analysis?
Watch Video on...
What is Encryption and Decryption , and how it make our message anonymous??
Friends in our previous post How to surf internet Anonymously we tell you why to surf internet anonymously and number of ways to do that. Our aim is to make...
Kali Linux Rolling Edition updated with the latest patches
The most popular Kali Linux was released on 2015 at DefCon 23 in Las Vegas. Kali is successor of Backtrack based on Debian Jessie,distribution, includes many popular penetration...