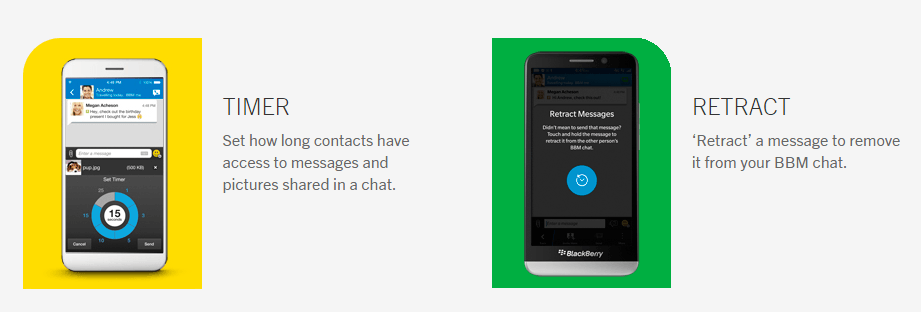
BBM BlackBerry now features timer just like Snapchat
Here is a good news for all BBM ( BlackBerry Messenger) Lovers, new Privacy features update which is live by BBM BlackBerry Application for all Android, ios or windows device....
IOS 9 Content Blockers: 1Blocker and Blocker
Apple will now support ad blocking. The new operating system iOS9 launching on Wednesday is dignified to change the interaction of users with the web on mobile and iPad....
SQL INJECTION BY VARIOUS WAYS
SQL INJECTION BY VARIOUS WAYS INTRODUCTION TO SQL INJECTION
The most easiest way to hack an site is hacking it by SQL injection. SQL Injection based on the vulnerabilities of an...
What is Encryption and Decryption , and how it make our message anonymous??
Friends in our previous post How to surf internet Anonymously we tell you why to surf internet anonymously and number of ways to do that. Our aim is to make...
9 Million Google play users infected by Adware (Android Virus)
Adware (Android virus)
Adware is a type of malware that automatically shows advertisement, banner or pop up on user's mobile or computer. Adware or we can say these type android...
Loki Got an upgrade – Loki Botnet new varient Detected
Loki Botnet (Malware) works in the same way as Marvel's Villen cum hero works (Trick the user and steal the information). Loki botnet, A bot (malware) which was detected...
Russia Got Targeted By Rotexy Trojan
Due to the hipe of trojan activity, Kaspersky decided to do a deep analysis of the evolution of popular malware family. And they found one most interesting (Rotexy) trojan...
How to use backtrack
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Before you start
Before we start playing with safty tools follow the following steps :-
Download btr5...
ISIS Hacker Arrested In Malaysia: US Military Data Hacked By ISIS Hacker
A Kosovo citizen is arrested by Malaysian Authorities in the charges of computer hacking and providing the personal data of U.S. Military members to the Islamic State terrorist group...
Google is going to mandate the Full Disk Encryption by default for devices with...
Last year when Google launched Android Lollipop 5.0, Google wanted to make the full disk encryption mandatory, but due to some reasons the idea didn’t work.
But this time with...
The Data You Keep In Your Mobile Is Not Secure: Pre-Installed Spywares in Smartphones
If you think that the data you keep in your phone is confidential then you must read this. A report claims that some smartphones are coming with the pre-installed...
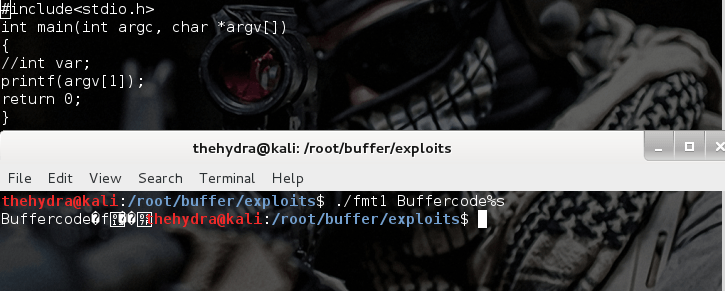
Format string exploits
Format string exploits became public in late 2000. It is easy to find errors in format string in comparison of buffer overflows. Once errors are spotted, they are usually...
Managing the Safety and Security of Sensitive Documents
The digital era has made it effortless and more efficient to conduct business than ever before, be it in a local space or on a largely worldwide scale. In...
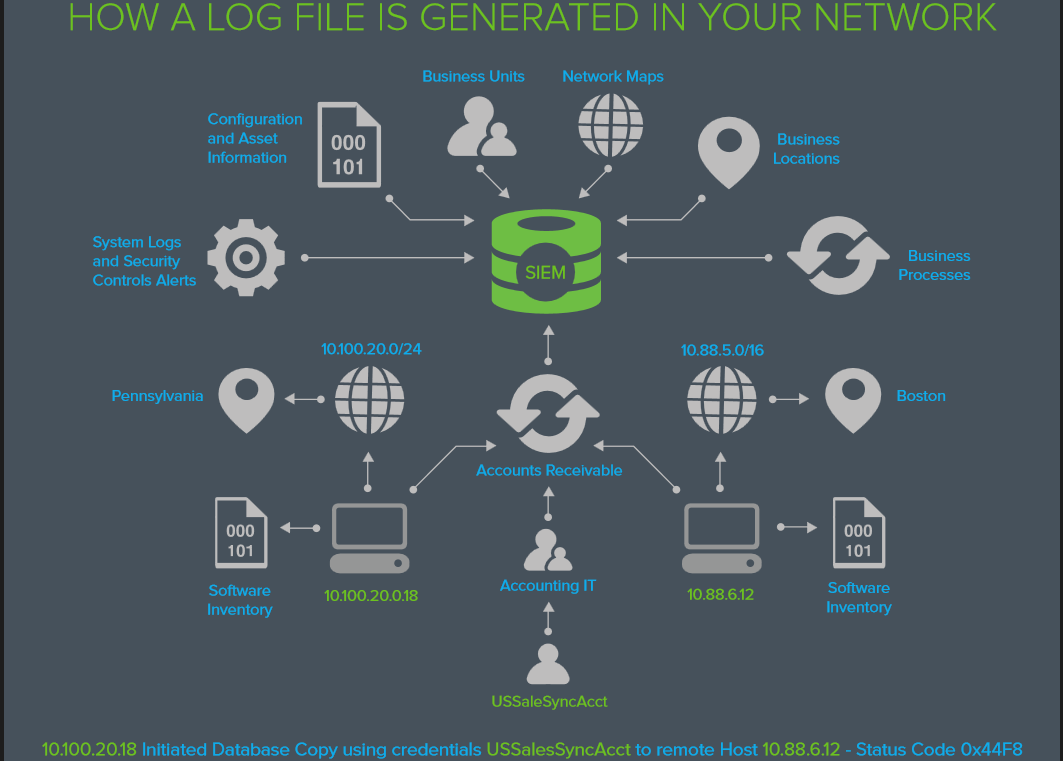
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
What’s in the LOG?
The information you need to answer
Who’s attacking us today? and
How did...
Vulnerability in PayPal user authentication system
It's always a matter of attraction when money is in the frame of attack. So It's time to get into the users PayPal account.. Paypal provides online / ebay...
How to Choose a Router for Your Business
If you think that choosing a router for your business is an easy task, you have no idea how wrong you are. It is not like choosing a standard...
CIA Director’s hacked email: Pak uses militants to counter India’s Influence in Afghanistan
Last week WikiLeaks started publishing the documents from the CIA Director’s hacked email revealing some top secrets. A set of document of released by WikiLeaks says that Pakistan uses...
IOS 9.0.2 fixes the Lock screen ByPass Bug
IOS 9.0.2 fixes the Lock screen Bypass Bug
After the launch of its latest version of iOS, Apple has rolled out two minor updates for its operating system (iOS9.0.1 and...
Let’s Encrypt: Free SSL Certificate Install by 1 Million websites
Let’s Encrypt published 1 million free Transport Layer Security SSL Certificates to webmasters who want to secure their connection between their users and domains and has achieved a vast...
How to hack windows password
How to hack windows password
Change your password if you Forget it
Hello friends today we learn how to change your password if your account or change windows password is locked/you forget your password.At that...
The Trojanized Adware: It can automatically install apps to your Android Device
What sort of apps do you install on your Android Smartphone?
I hope the trusted ones. Now, what if someone installs a malicious app on your smartphone without your permission?
It...
Android Banking Trojan Hiding In Apps Under Different Names: Targeting over 420 apps worldwide
Beware if you recently have installed any funny video application from Google Play Store as it may contain android banking Trojan.
Most of the people love to watch funny videos...
ProxyHam : Anonymously Access Wi-Fi from 2.5-Miles Away
Here we will discuss How to Anonymously Access Wi-Fi from 2.5 miles away using Dubbed Proxyham. It's always the matter of discuss when anonymity is in the frame. In...
CamScanner: Google store removed the app as it contains malware
Camscanner is scanner application available in google play and app store. Recently, it is found as a front for disseminating malware on gadgets and has been expelled by Google...
Stage fright Bug 2.0: All Android Devices are Vulnerable to the Bugs
Once again the Stage fright vulnerability is back, two new Android Stage fright vulnerabilities are recently disclosed.
This time with some new tricks, an attacker can hack the Android Phone...
Attackers are using facebook messenger to spread Locky Ransomware
Any Facebook message with an image file (.svg format) send by your friend can be a Locky Ransomware file, so just avoid clicking it.
What is Locky Ransomware?
Locky is ransomware released...