Hidden device with arp-scan
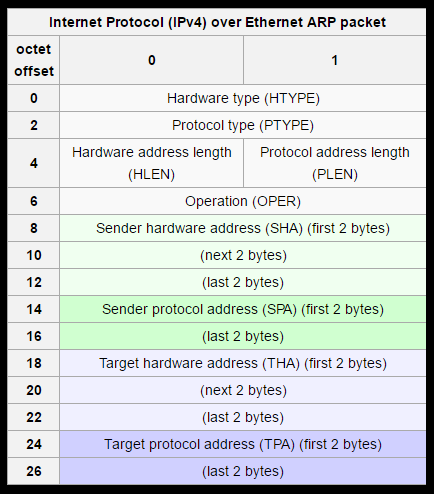
ARP (Address Resolution Protocol) use to map IP network address to the hardware address. Address Resolution Protocol use a message format contains one ARP request or response. The simple use ARP protocol is to map a network address like any IPV4 to a physical address like MAC address (Ethernet address). The APR will works on IPV4 , In IPV6 the APR functionality provided by NDP (Neighbor Discovery Protocol). The size of message depend upon upper layer and lower layer address size, and the payload of ARP packet consist four parameters first on is Hardware address, second one is protocol address, third is sender host and last one is receiver host.
arp-scan
To use ARP protocol we will use ARP scan Tool, is open source and very efficient tool to Scan ARP packets to show every active IPV4 device on your subnet. The device cannot hide form ARP even if they have firewalls (not like Ping). The APR works on Local subnet. If you want to scan device which is outside your subnet, you can use ping Scan (like Nmap, Ping Sweep tool, NetScanner, or other). The arp-scan supports different platform like Linux, Unix.
Install arp-scan in Linux (Ubuntu, Debian or other)
apt-get install arp-scan
In Kali Linux arp-scan comes pre-installed.
Use arp-scan to find hidden devices
arp-scan works with Ethernet (802.3) and Wireless network (802.11), and it also work with token ring and FDDI (Not tested). It currently not support PPP or SLIP (serial link) due to the ARP is not support them.
Discovering all host on local network
sudo arp-scan --interface=eth0 --localnet
–interfacce=eth0 defines the interface use for scanning
–localnet to scan all possible IP address connected to interface
Interface name varies according to different Operating System. like eth0 is denoted to Ethernet and Wlan0 denoted to Wireless network.
vipin@kali:~# arp-scan --interface=wlan0 --localnet Interface: wlan0, datalink type: EN10MB (Ethernet) Starting arp-scan 1.9 with 256 hosts (http://www.nta-monitor.com/tools/arp-scan/) 10.0.1.3 0c:1a:a0:c2:94:c0 Dell Inc 10.0.1.54 0b:0c:29:34:f9:6a VMware, Inc. 10.0.1.67 d4:85:64:63:b7:48 Hewlett-Packard Company 10.0.1.72 0b:0c:29:6d:92:b5 VMware, Inc. 10.0.1.24 c2:e9:84:0e:c1:12 (Unknown) 10.0.1.125 23:80:23:ac:dd:c2 (Unknown) 10.0.1.145 0b:50:56:b1:80:db VMware, Inc. 10.0.1.156 0b:50:56:b1:dc:a7 VMware, Inc. 10.0.1.179 19:a9:05:4b:61:58 Hewlett-Packard Company 10.0.1.189 ab:95:9a:69:f7:6c (Unknown) 10.0.1.191 1e:a8:82:10:66:4a (Unknown) 10.0.1.213 0b:50:56:b1:fd:63 VMware, Inc. 10.0.1.213 0b:50:56:b1:2b:18 VMware, Inc. (DUP: 2) 10.0.1.213 0b:50:56:b1:f3:b4 VMware, Inc. (DUP: 3) 10.0.1.213 0b:50:56:b1:f3:2c VMware, Inc. (DUP: 4) 10.0.1.213 0b:50:56:b1:8f:5b VMware, Inc. (DUP: 5) 10.0.1.240 0b:22:55:cb:59:85 CISCO SYSTEMS, INC. 10.0.1.242 3c:a8:2a:0f:d3:d2 (Unknown) 10.0.1.241 0b:25:84:69:6f:c1 CISCO SYSTEMS, INC. 10.0.1.243 3c:a8:2a:0e:c5:78 (Unknown) 10.0.1.244 0b:0c:29:4e:54:33 VMware, Inc. 10.0.1.250 0b:1b:54:97:68:8c CISCO SYSTEMS, INC. 10.0.1.252 0b:21:d8:70:e4:4b CISCO SYSTEMS, INC. 10.0.1.253 0b:19:55:9d:60:c1 CISCO SYSTEMS, INC. 10.0.1.145 bc:ea:fa:6f:ec:d2 (Unknown) 10.0.1.77 98:fc:11:ab:65:b9 Cisco-Linksys, LLC 10.0.1.178 48:5a:3f:12:d9:df WISOL 10.0.1.167 f0:25:b7:3e:a1:b1 (Unknown) 10.0.1.182 60:57:18:71:c5:a5 Intel Corporate 29 packets received by filter, 0 packets dropped by kernel Ending arp-scan 1.9: 256 hosts scanned in 2.259 seconds (113.32 hosts/sec). 29 responded vipint@kali:~#
on above result, it descovered 29 live node apart from local machine
arp-scan with custom IP range
root@kali:~# arp-scan --interface=wlan0 10.0.1.0/124 (or) vipin@ubuntu:~$ sudo arp-scan --interface=wlan0 10.0.1.0/124
ARP protocol not provides methods for any kind of authentication ARP replies on a network, APR reply come from system other than the one with required layer 2 address.