This year, in the month of January , three Apple OSx zero day flaws were revealed by Google .First vulnerability was – OS X Yosemite had flaw to pass arbitrary value to the network. Second vulnerability was about OS X’s low-level I/OKit kernel framework and third was also related to OS X’s low-level I/OKit kernel framework. You can check them here.
Today a researcher at Malwarebytes, while testing a new adware installer, discovered that his sudoers file had been modified. Oh!! sudoers file, it means user/app can get root permission ?
Sudoers file are hidden Unix/Linux files that determines, who is allowed to get root permission. It is typically located at /etc/sudoers. You can learn more about it on wikipedia from here .
OSX Sudoers Flaw : Password-free behaviour
Basically you can’t access sudoers file without root permission but if one get either root access or will able to modify this file by any other method, in this case modification in file allowed the app to gain root access.
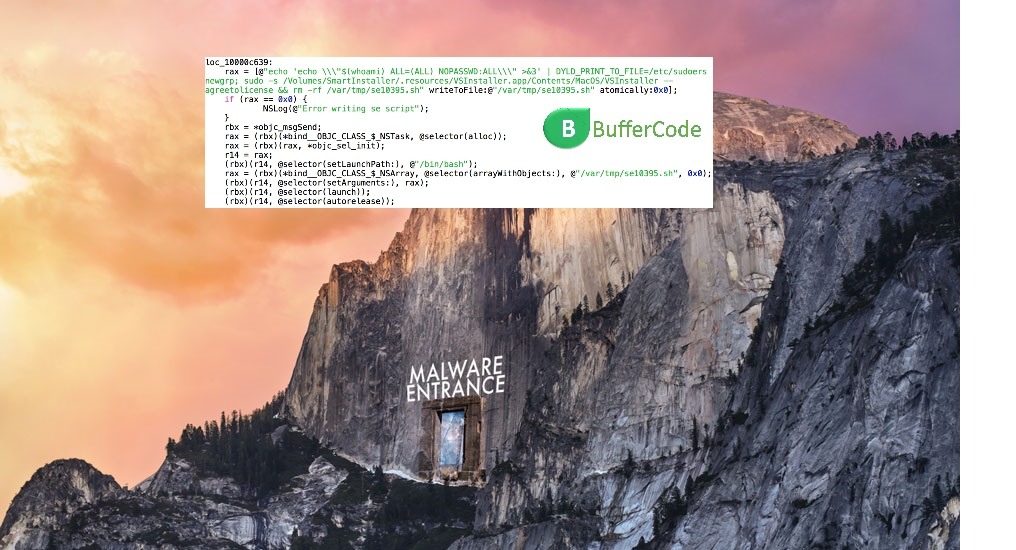
OSX Sudoers Flaw : If you will analyses the code given here , you will find a script that exploits the DYLD_PRINT_TO_FILE vulnerability , which will be executed and deleting itself when it finished.
Then the script uses password-free behavior for VsInstaller app, which is a searching tool. These kind of attacks were seen in windows but now Windows O.S increases their security. The Bad News is that OSx and Linux are the most vulnerable system of 2015.
Twitter handler @beist alerted Apple sometime before Essor discovered the Bug. But unfortunately Apple yet has not fixed this bug. The worst thing is that there is no good way to protect yourself from it, but here is guide or say tip on how to avoid these kind of installers.
Source: Malwarebytes
Have something to add in OSX Sudoers Flaw article ?? share it in comments .
Follow us on Facebook, Google Plus and Twitter.
Tags: OSX Sudoers Flaw, Mac’s Password-free behaviour, OSX vulnerability