Home Search
- search results
If you're not happy with the results, please do another search
Russia Got Targeted By Rotexy Trojan
Due to the hipe of trojan activity, Kaspersky decided to do a deep analysis of the evolution of popular malware family. And they found...
Loki Got an upgrade – Loki Botnet new varient Detected
Loki Botnet (Malware) works in the same way as Marvel's Villen cum hero works (Trick the user and steal the information). Loki botnet, A...
SMISHING on Android devices | Android Malware (TimpDoor)
Timpdoor is the recent Android malware that has been discovered by McAfee mobile researcher's team that turns mobile into a backdoor. This Android malware is...
Demonbot is on rising | A New Botnet
As security is getting stronger so hackers are getting more stronger. Once a loophole is closed by Operating systems or any vendors then hackers find...
PUBG live Streaming using Mobile phone
Let's start PUBG streaming on facebook using the mobile phone. Yes, you read it correctly. Well, how many times you have seen this post...
Queen charge with Miners attack | COC
Queen charge with Miners is not a new strategy, that you are going to know now. But you have seen many time that queen...
Benefits of Social Media for Business
Today many organisations are struggling to eliminate the use of smartphones and other devices to access their social media pages or accounts. Also, there...
How to buy best Gaming Headset
Looking For Best Headset for Gaming and Music that will provide a better gaming experience as well as music?
Here is everything you need to know about Best Budget Gaming Headset before buying a new one.
Virtualization in Mac | How to create Virtual machine in Virtual Box?
Virtual Machine
Virtual machines are machines or systems that do not physically exist but gives the feel of working on a physical machine or system....
How To Download YouTube Video on Android Phone or Tablet
Today, YouTube is the largest video sharing websites in the digital world. Per day millions of people sharing millions of new videos on various...
What is Sandboxing and How it works?
In this article, we will discuss sandboxing, how it works and list of free sandboxing environments, etc. Hybrid analysis, Malware analysis, and Threat analysis,...
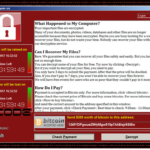
WannaCry ransomware attack: Largest Ransomware Attack In The History
By now, we are sure that you have heard something about wannacry ransomware. There may be a lot of questions in your mind such...
What is Ransomware and How it works?
Attackers use ransomware to get ransom from its victims. In other words, ransomware is a malicious program or software to block user access on...
How to Capture and Record an IPhone, IPad screen without jailbreak ?
Nowadays, everybody wants to be a prominent YouTuber. Some wants to make money through it while others just do it for entertainment. The problem...
How to make sure a file is safe or threat? | How to do...
Today, we will discuss how to find, a file is safe or a threat for your system?
Or we can say, how to do malware...
Mac Malware: Time to test Apple’s Security
Last quarter shows an interestingly spike in malware activity that targeted Mac users only. New samples in the 1st 3 months of this year...
An Almost Impossible To Detect Phishing Attack Using Punycode
In our previous article How to secure you account from phishing page, we discussed about how to create and detect whether a page is...
Android Banking Trojan Hiding In Apps Under Different Names: Targeting over 420 apps worldwide
Beware if you recently have installed any funny video application from Google Play Store as it may contain android banking Trojan.
Most of the people...
Good News For Gamers: Oculus reduces their Rift and controllers price
Oculus VR , one of the most famous company of making virtual reality headset hardware and software products. Palmer Luckey is the founder of this...
Managing the Safety and Security of Sensitive Documents
The digital era has made it effortless and more efficient to conduct business than ever before, be it in a local space or on...
Surge S1: Xiaomi Launched its own Processor
Xiaomi, one of the most popular smartphone maker company of China launched it own processor named Surge S1. Smartphones, Mobile Apps, Laptops making are...
Enhance the proficiency of system administrators with these apps
A network administrator is responsible for installing computer and network systems, maintaining and upgrading network systems and also monitoring those systems to improve the...
Microsoft Hooks Up With Google for Office Mobile Apps
The mobile application is generally designed to give comfort and reduce the time for the users. In this growing economy, everything is going to...
VERSATILE ASPECTS OF USER-FRIENDLY TWITTER MOBILE APPS
Twitter- the highly popular online and social-networking service where users post and read tweets, which are of 140 character length. This social networking giant...
Attackers are using facebook messenger to spread Locky Ransomware
Any Facebook message with an image file (.svg format) send by your friend can be a Locky Ransomware file, so just avoid clicking it.
What...
Uber vs Cab :Taxi drivers started to protest against the app based raid-hailing services-who...
About four thousand taxis gathered in the centre of London, they remained idle without any movements with the intention to protest against the app...