Format string exploits became public in late 2000. It is easy to find errors in format string in comparison of buffer overflows. Once errors are spotted, they are usually eradicated(removed) quickly. The field is advancing continuously and you always find new techniques discovered by the countermeasures and hackers implemented by developers. We can only go so far in these tutorials, your journey is only beginning.
Format strings are found in format functions such as printf(),sprintf(),fprintf(),snprintf() etc. As you know printf() function may have any number of arguments see here . Here we will introduce you from two more format tokens, %hn and <number>$.
The %hn print the length of the current string in bytes to var where short int values overwrite 16 bit
for ex:
printf("Buffercode %hn",var);
Result:The value 04 is stored in var i.e., 2 bytes
The $ gives you direct access to parameter
Ex: printf("Buffercode %2$s","21","234");
Output: Buffercode 234 (2nd parameter is used directly)
Let’s see what happens if use format string in wrong way or say if we forget to add a value for the %s to replace
//buffercodefmt.c
#include<stdio.h>
main()
{
printf("Hello %s \n");
}
Output:

No need to get shocked from the above output, it’s not an arbitrary value instead it is machine language (binary), shown in ASCII. But still I don’t think it is what you are expecting. In worst case , consider how it works when we will use variable arguments like this.
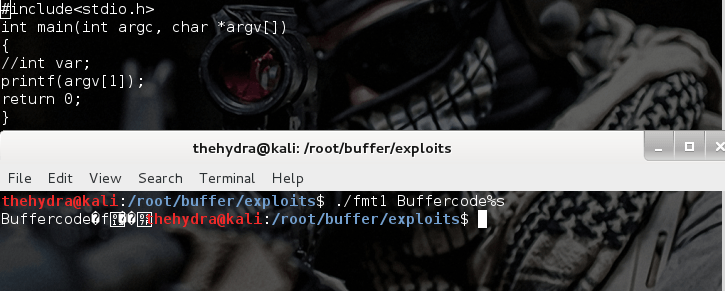
//buffercodefmt2.c
main(int argc, char *argv[])
{
printf(argv[1]);
}

Oh!! it appears that we have the same problem as in above program. But thi later case is much more deadly because it may lead to total system compromise.
Deeper into Format string exploits
To find out what happens we must recall how Stack operates on format functions. As we see in our previous post Stack Operations , how stack grows from Higher Memory to Lower Memory i.e., from bottom to top of stack. As always parameters of printf() functions are push on the stack in reverse order.
The printf() functions maintain a internal pointer that points to the format string( Top of the stack) and starts print untill it comes on a special character . If the % is encountered, the printf() function expects a format token to pointout. and thus increments the internal pointer towards the bottom of the stack to find out the variable or absolute value.
Problem in printf() function
From here problem in printf() function begins. There is no way to check if the correct number of variables or absolute values were paced on the stack for format string or not. In case if the programmer is sloppy or if the user is allow to present their own format string , the function will happily move down the stack i.e., higher in memory to grab the next value which will satisfy the format string.
In our Ex what we saw was the print() function grabbing the next value on the stack and returning it where the format token required.
Denial-Of-Service (DOS) Attack
In the best case, the stack value may contain a random hex value that may be interrupted as an out-of-bounds address by the format string. It may cause to have a segmentation fault. This could probably lead to denial-of-service condition to an attacker.
If the attacker is careful and skillful, they may be able to use this fault to read and write values/data to arbitrary addresses. In case if the attacker will wind the correct location in memory, the attacker may be able to gain root privileges.
In our Next Post we will show you how to get root privilege using this fault.
Have something to add ?? share it in comments .
Follow us on Facebook, Google Plus and Twitter.