Russia Got Targeted By Rotexy Trojan
Due to the hipe of trojan activity, Kaspersky decided to do a deep analysis of the evolution of popular malware family. And they found one most interesting (Rotexy) trojan...
Loki Got an upgrade – Loki Botnet new varient Detected
Loki Botnet (Malware) works in the same way as Marvel's Villen cum hero works (Trick the user and steal the information). Loki botnet, A bot (malware) which was detected...
Demonbot is on rising | A New Botnet
As security is getting stronger so hackers are getting more stronger. Once a loophole is closed by Operating systems or any vendors then hackers find out another way to breach...
What is Sandboxing and How it works?
In this article, we will discuss sandboxing, how it works and list of free sandboxing environments, etc. Hybrid analysis, Malware analysis, and Threat analysis, they all use the same technology...
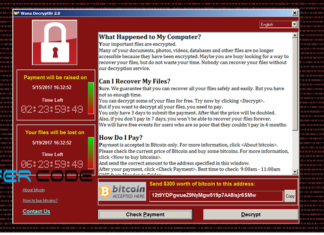
WannaCry ransomware attack: Largest Ransomware Attack In The History
By now, we are sure that you have heard something about wannacry ransomware. There may be a lot of questions in your mind such as What is wannacry ?...
What is Ransomware and How it works?
Attackers use ransomware to get ransom from its victims. In other words, ransomware is a malicious program or software to block user access on their own system or encrypt...
How to make sure a file is safe or threat? | How to do...
Today, we will discuss how to find, a file is safe or a threat for your system?
Or we can say, how to do malware and threat analysis?
Watch Video on...
Mac Malware: Time to test Apple’s Security
Last quarter shows an interestingly spike in malware activity that targeted Mac users only. New samples in the 1st 3 months of this year are nearly equal to the...
An Almost Impossible To Detect Phishing Attack Using Punycode
In our previous article How to secure you account from phishing page, we discussed about how to create and detect whether a page is a phishing page or original...
Android Banking Trojan Hiding In Apps Under Different Names: Targeting over 420 apps worldwide
Beware if you recently have installed any funny video application from Google Play Store as it may contain android banking Trojan.
Most of the people love to watch funny videos...
Managing the Safety and Security of Sensitive Documents
The digital era has made it effortless and more efficient to conduct business than ever before, be it in a local space or on a largely worldwide scale. In...
Attackers are using facebook messenger to spread Locky Ransomware
Any Facebook message with an image file (.svg format) send by your friend can be a Locky Ransomware file, so just avoid clicking it.
What is Locky Ransomware?
Locky is ransomware released...
How to Choose a Router for Your Business
If you think that choosing a router for your business is an easy task, you have no idea how wrong you are. It is not like choosing a standard...
Introduction to Log Collector and Event Sources | SIEM
In this article, we will discuss how we use a log collector to collect and analyze logs. While in the previous article we have discussed Logs. We already have...
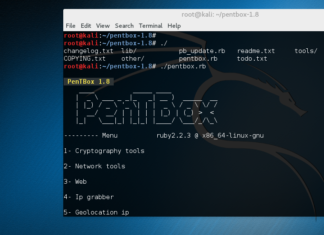
How to Install Honeypot on Kali Linux
In this article we will show how to install Honeypot in Kali Linux. The Pentbox is Security suite that can be use for penetration testing to perform various operations. The...
Droid Turbo new update started rolling out
Droid Turbo new update started rolling out : New updates brings latest security patches and some performance related improvement to Droid Turbo, recently Verizon has stated rolling out a...
Top Free Vpn Provides 2016
A VPN (Virtual Private Network) extends your private network across a public network, such as a company internal network. There are several numbers of system that enables you to...
End-To-End Encryption is now on WHATSAPP
On Tuesday,Whatsapp's founder Jan Koum disclosed that all the messages and call which are done through Whatsapp are fully encrypted.Whatsapp is now lot more secure.
All user those who want...
Explore and Search Exploit in Metasploit
Metasploit having a big name, when we talking about security. Metasploit was written in Perl as a portable network tool, In 2007 the Metasploit Freamwork has completely rewritten in...
Bitport Review : Download torrents to your cloud and play them online
Bitport.io review :Most of the people here use torrent to download movies, games , series , software and much more. But there is a question is it safe to...
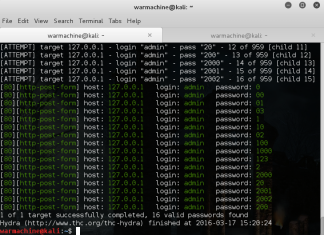
How To Crack Web Form Passwords Using Hydra With Burpsuite In Kali Linux
In our previous article How To Crack Password Using Hydra In Kali Linux , we have discussed about THC Hydra- A tool for Online Password attacks. In this tutorial we will discuss...
How To Crack Password Using Hydra In Kali Linux
Weak password is still a big problem in the world of security. User need to set a strong password to restrict the access of data from anonymous user. Even a...
Guccifer hacker extradited to the US
Guccifer is a egregious Romanian hacker,whose real name is Marcel Lazar Lehel has been permitted to abandon to the United States to face Computer Intrusion and Identity theft charges...
Let’s Encrypt: Free SSL Certificate Install by 1 Million websites
Let’s Encrypt published 1 million free Transport Layer Security SSL Certificates to webmasters who want to secure their connection between their users and domains and has achieved a vast...
Developer of most secure messaging app hired by Apple
This time Apple is very sincere about upgrading the security of its iPhone so that no can hack it.Apple also hired one of the key builders of signal to...
Phishing malware crashes ICICI bank
#Phshing Malware crashes ICICI bank .... https://t.co/a8vTOVvuob
— Buffercode (@buffercoding) February 25, 2016
Official @ICICIBank_Care reply to tweet :
@buffercoding Hi, ICICI Bank has a robust & multi-level security system for all its banking...