Loki Botnet (Malware) works in the same way as Marvel’s Villen cum hero works (Trick the user and steal the information). Loki botnet, A bot (malware) which was detected in early 2017 and used for credential stealing purpose. It was designed to steal credentials from victim’s machine software like the email client, FTP client, browser, file management clients and whatever credential were being used in victim’s system. It was used to spread using phishing emails.
Loki Botnet (Malware):
Recently, Fortinet threat researcher team has detected a new variant of Loki Botnet (Malware) and again it is spreading using Phishing emails.
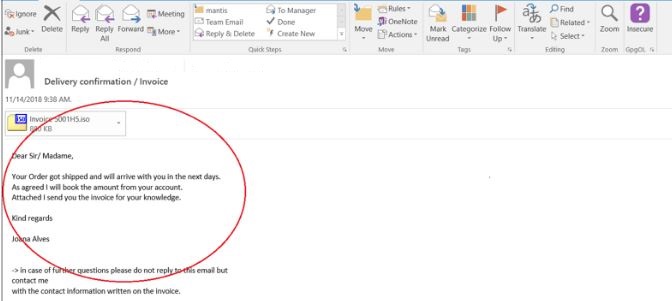
Above Picture shows an example of phishing email which is received by one user, email body message or attachment name can be different for another victim or target. This email has an attachment named invoice with extension ISO. Normally, invoice file comes in PDF format, but email body tells that it an invoice, there are common tricks to convince a user to click or open attachments.
Once the victim clicks on the ISO file it will open in Winzip or any archiving software that is installed. And it will show you what this attachment contains inside.
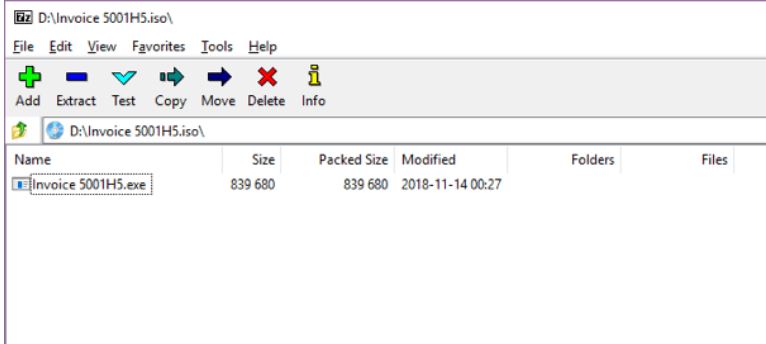
Fortunately, the attachment does not contain any autorun file otherwise file can run automatically once downloaded and clicked by the victim. fortinet researcher team analyzed this file in PE tools, they found this executable extract another executable file in its memory and that executable is the main module of Loki Botnet (Malware).
Please check: what is sandboxing and how it works?
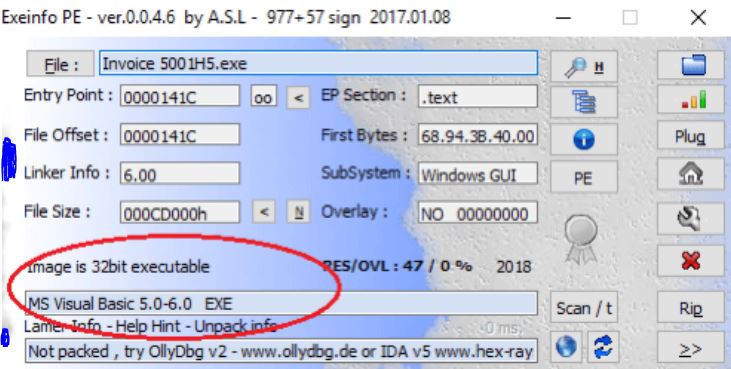
Researcher team found this module do the exact same job that Loki Botnet (malware) did in his previous variant. The whole purpose of this (Loki) botnet malware is to steal the credentials from victims system. And targeted softer can be the browser, VPN clients, FTP clients, IM clients or any software that is using user’s account and credential to authenticate or functionality.
The only new thing in this module is the URL of its C&C server on which it was reporting, once it collects credentials from the victim’s system.
“hxxp://utl-ae.ml/img/tim/Panel/five/fre.php”
However, this URL has been reported as malicious URL and Fortinet antivirus detecting attachment as a virus. Below are the things that you can perform as a user or admin level.
- Please do not open any email that seems suspicious or coming from an unknown source
- Do not open any attachment coming in an email from an unknown source. first, validate the sender address and his name spelling.
-
Keep applications and operating systems up to date with the latest patch released by respective vendors
-
Make sure anti-virus software and associated files are up to date
-
Search for existing signs of the indicated IOCs or suspicious activity in your systems and environment
- Ask the network team to block the above-given link in the perimeter devices.
- Ask antivirus team or admin to block below Hashes:[Invoice 5001H5.iso]31F6B075E2F4C9D6463839BE7A2CEFDABF99A488329CEA185D2F333A5F9FF8B7
[Invoice 5001H5.exe]
37F936321D0925413DC203C318B631E71040E07A1FB4B7057778D6F628B2A346
- To track the number of users which got infected with this Malware (Loki botnet), ask security team to track for the number of hits on above mentioned URL and other detail if requires.
If need any help or want to add something please use the comment box.








