In this article, we will discuss sandboxing, how it works and list of free sandboxing environments, etc. Hybrid analysis, Malware analysis, and Threat analysis, they all use the same technology called sandboxing.
What is sandboxing?
Sandboxing is a technology that provides a virtual platform to use security mechanism against the untested code or third party software whose source is not verified or any program that seems to be a threat or suspicious for the system.
Also check: What is ransomware and how it works?
How sandboxing works?
We run suspicious programs in the sandbox environment to check the behavior i.e., activities of the program on execution. While analyzing, it gives us a risk-free environment where we can run and analyze the behavior of the program.
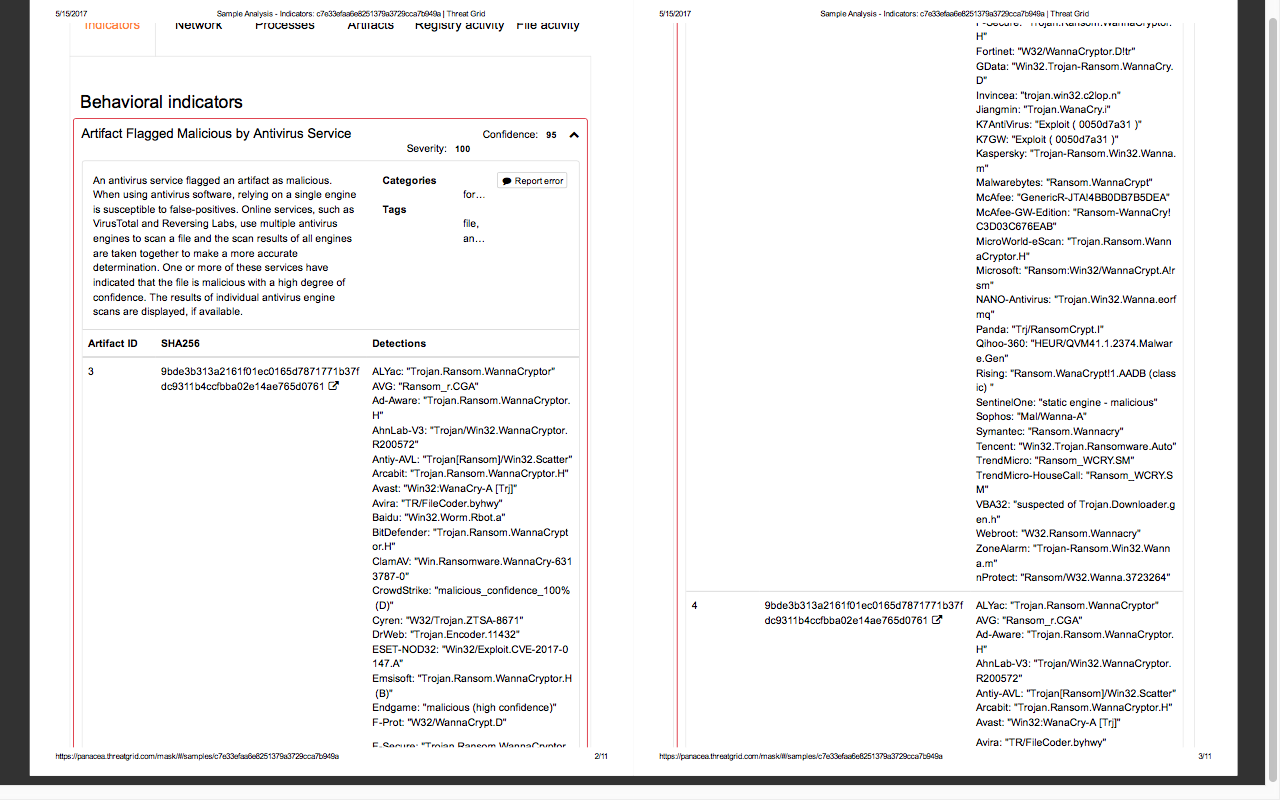
After analysis sandbox makes a report that contains all the activities of processes that were executed by the program tested in the sandbox.
In matters of sec or minutes [depend on file] sandbox environment will provide you the detail output that contains all the activities of file/program
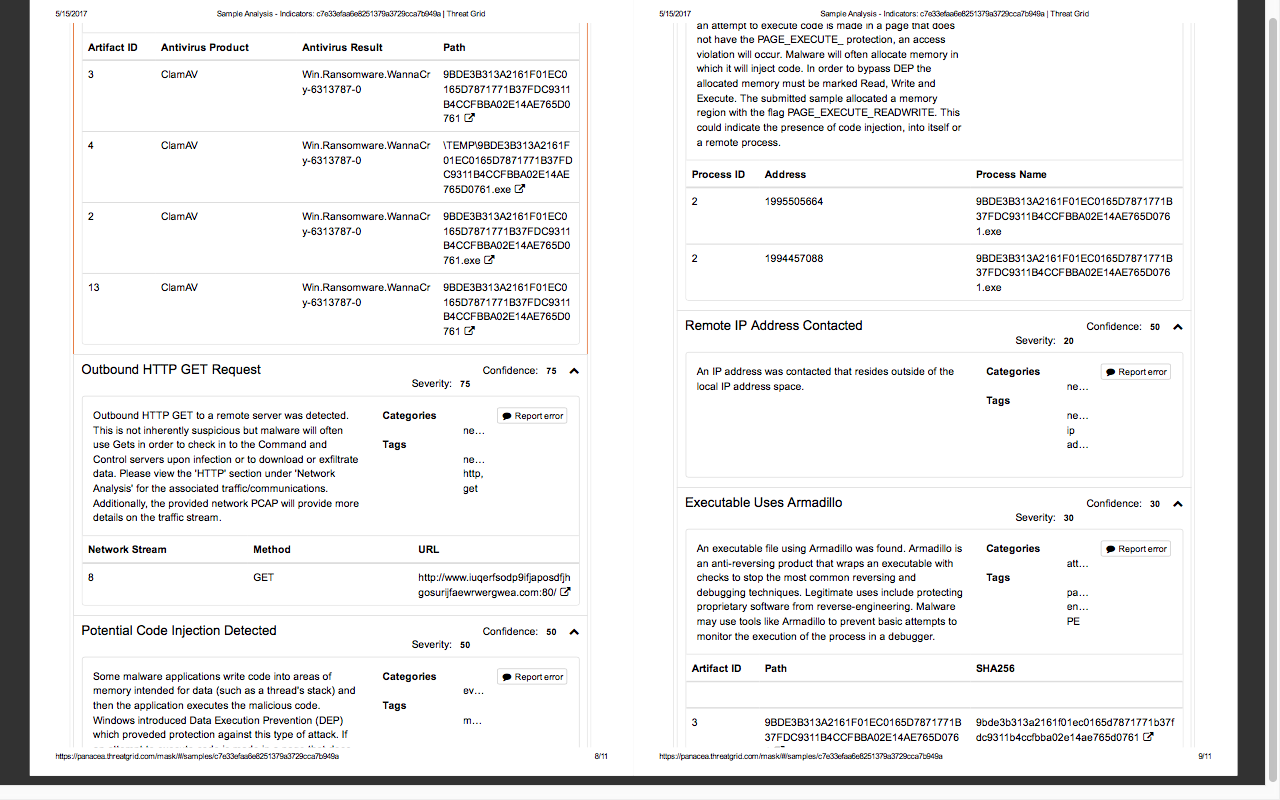
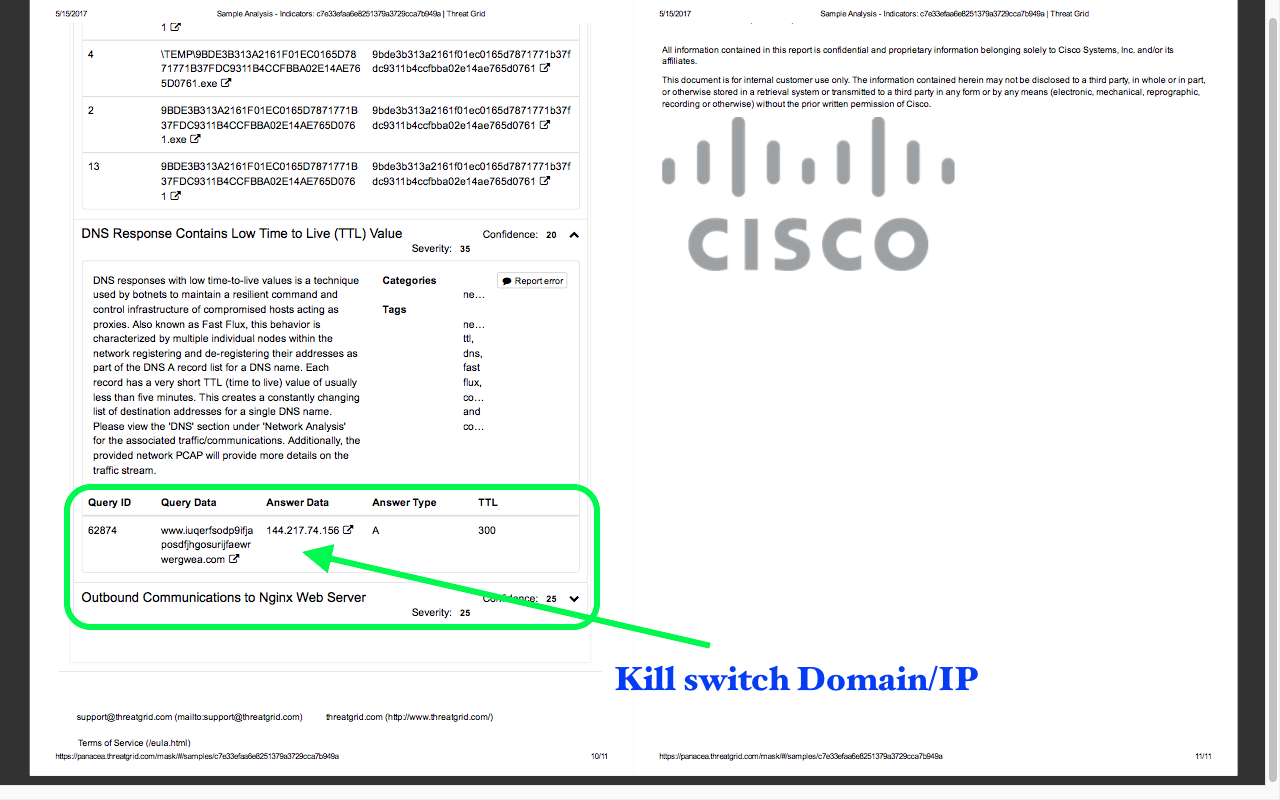
Ex:- what this file did, what it tried to do and what commands it runs, which process was triggered, and on which process it failed to call, to which domains and IP’s it tried to communicate, memory dump, etc.
In the end, it will provide you the total score based analysis on all activities and indicator of compromise. If the file found to be malicious then it will also tell us about the nature of file i.e., it meets to which threat category. Below is the list of free sandboxing environment:
List of the free sandboxing environment:
- Reverse.it: It is a free malware analysis service running on VxStream Sandbox v6.50 in the backend.
- Valkyrie runs several analyses using run-time behavior and can warn users against malware undetected by classic antivirus. Click here to know more.
- Virus total: It is a free malware analysis system that can detect malware from files or URLs. Click here to know more.
- Viacheck.ca: You can upload any kind of file including executable ones for malware analysis. It will email a complete report based on the analysis.
- Cuckoo sandbox: It is the opensource automated malware system. Click here to know more.
Preparing a sandbox:
Instead of using an online sandbox environment, we can also prepare our own sandbox environment as per the requirement. But before installing and configuring a sandbox environment, we should take care of a few things like:
- What we want to achieve and how?
- Which type of file we have to analyze?
- Which operating system do we need to install to run the analysis?
- And which type of information we want from file analysis?
Virtual machine preparation is the most important and critical part of sandboxing, step by step planning is needed for the same.
For example:
- Which operating system and patching level we should use.
- Which version and which software we must install [ security software that requires analyzing the threats and software version matters when analyzing the exploits].
How sandboxing works?
Sandboxing provides an option to upload the file. After submission of the file virtual machine starts executing the file and analyzing the behavior of that file. Not only the file we can also submit URL and email to identify the nature of that URL and email. If you have doubt on any email just save that email in the mail template and submit in the analysis environment.
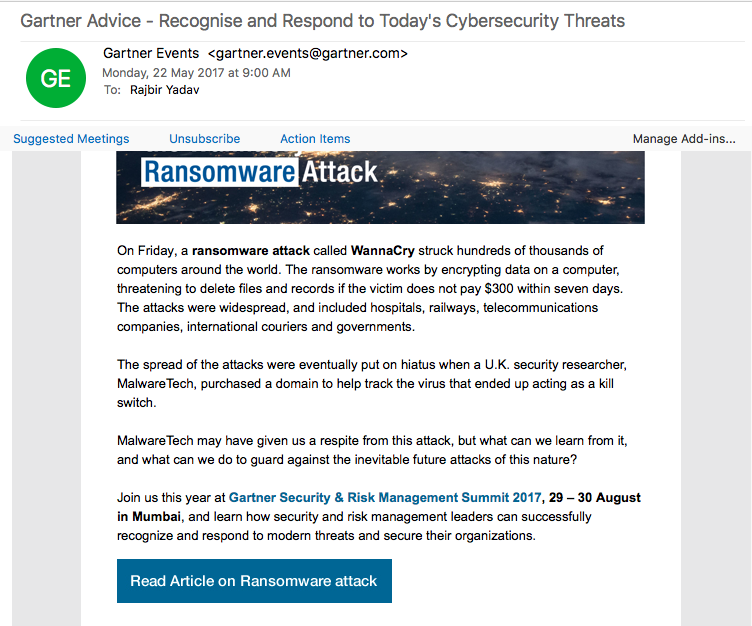
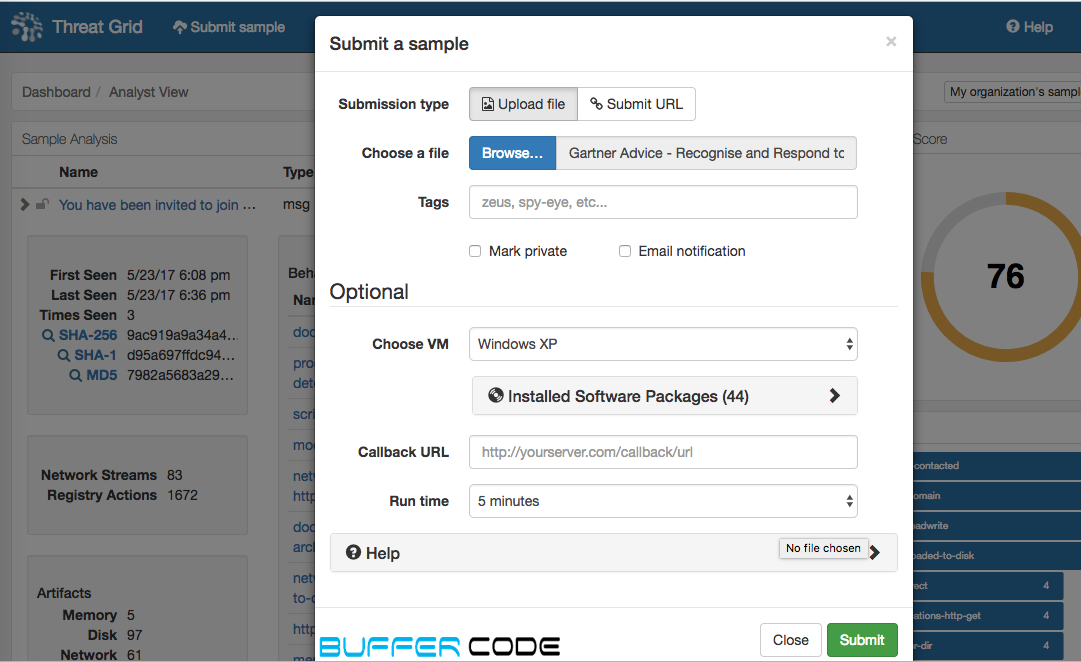
For example: Below is the screenshot of an email that we received from Gartner.
Now, we are going to test this email. We are trying to find whether this is a phishing email or spam email.
Below is the step to step screenshots, for analysis of this email:
- Browse and submit the saved mail or file you need to check and click on submit
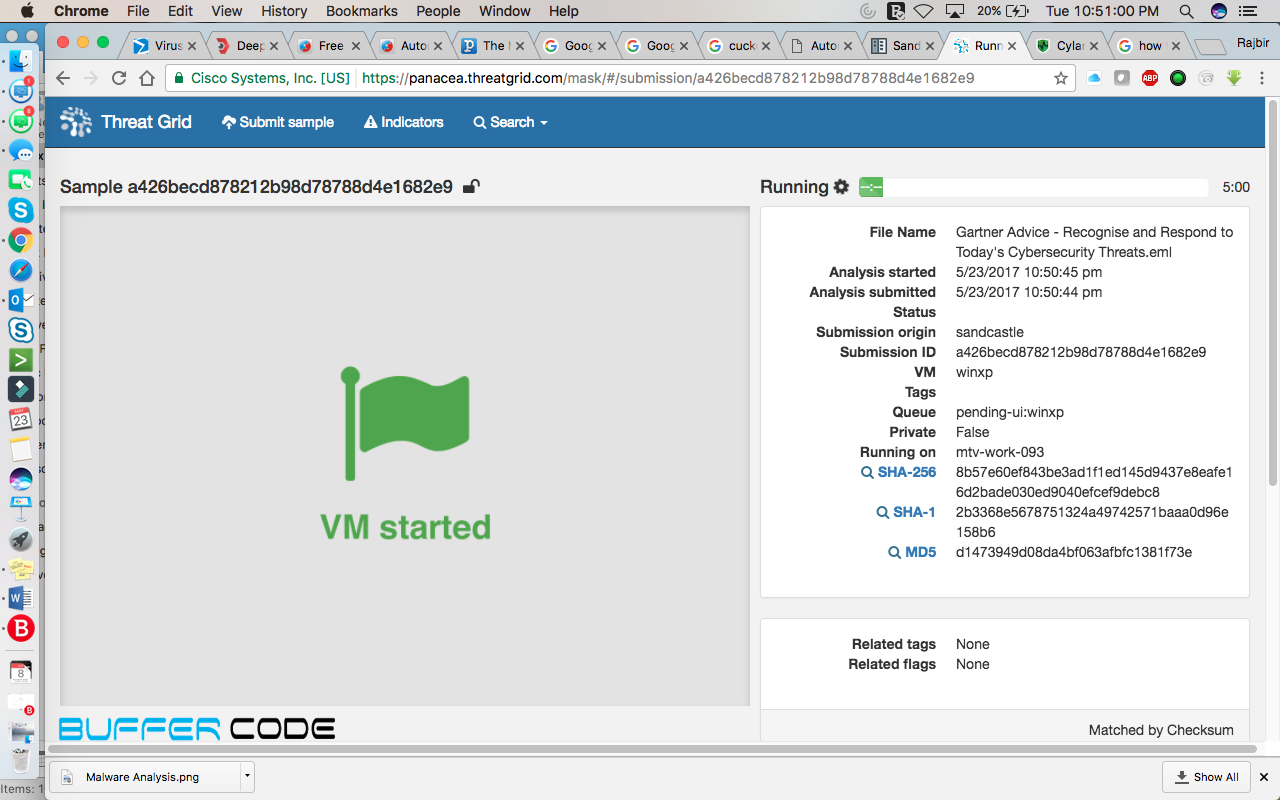
- An installed virtual machine will start execution automatically
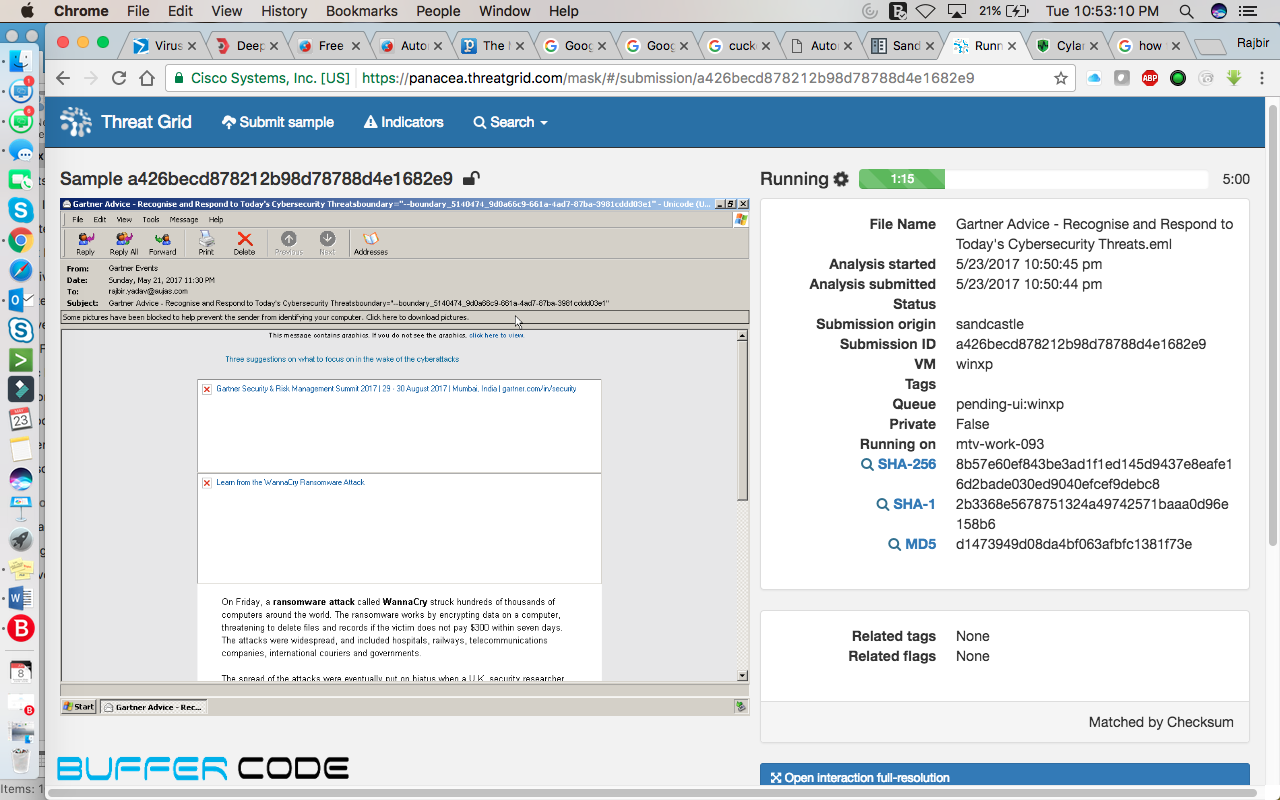
- The email we have submitted, will be open automatically into the installed Virtual machine

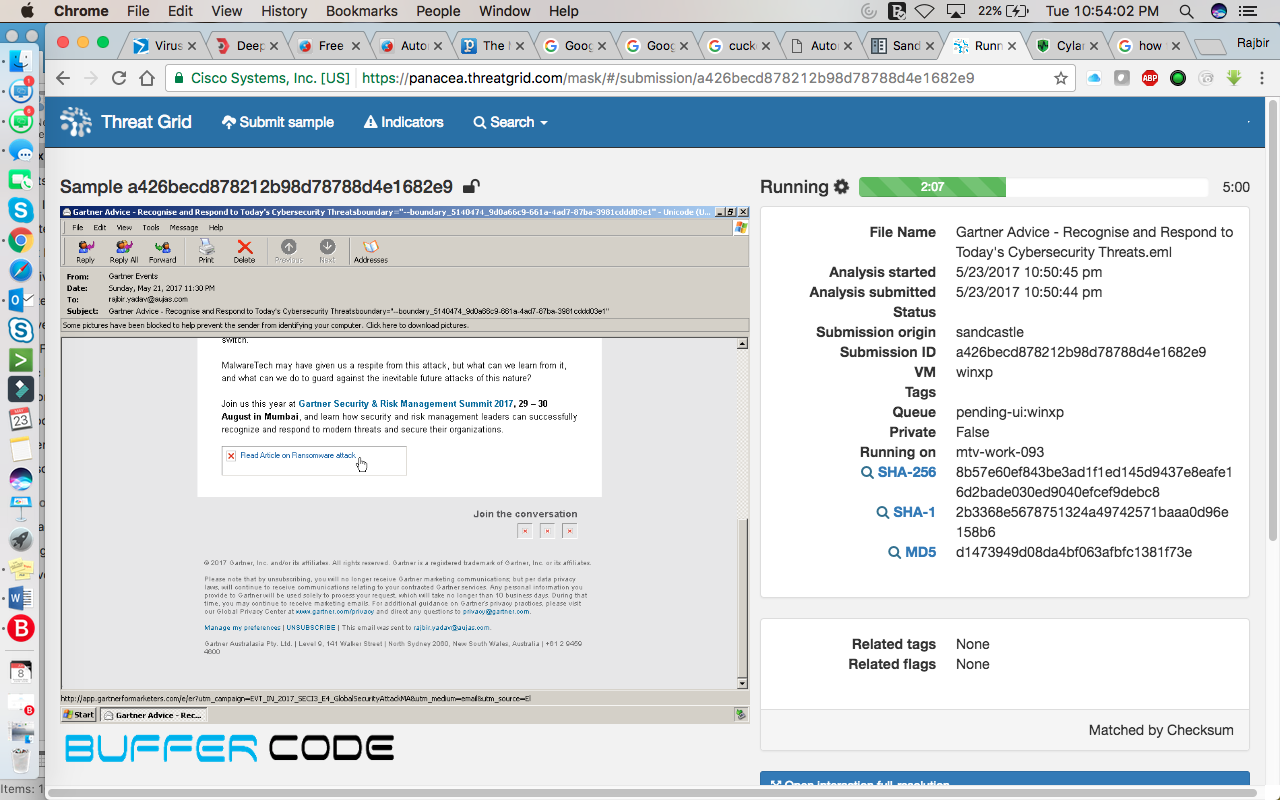
- URL available in the mail will be open in the browser. And will reach on the exact destination where email-sender wants you to reach i.e., redirection of URL, any suspicious file from any phishing site, or any site that was in the mail, got downloaded automatically.

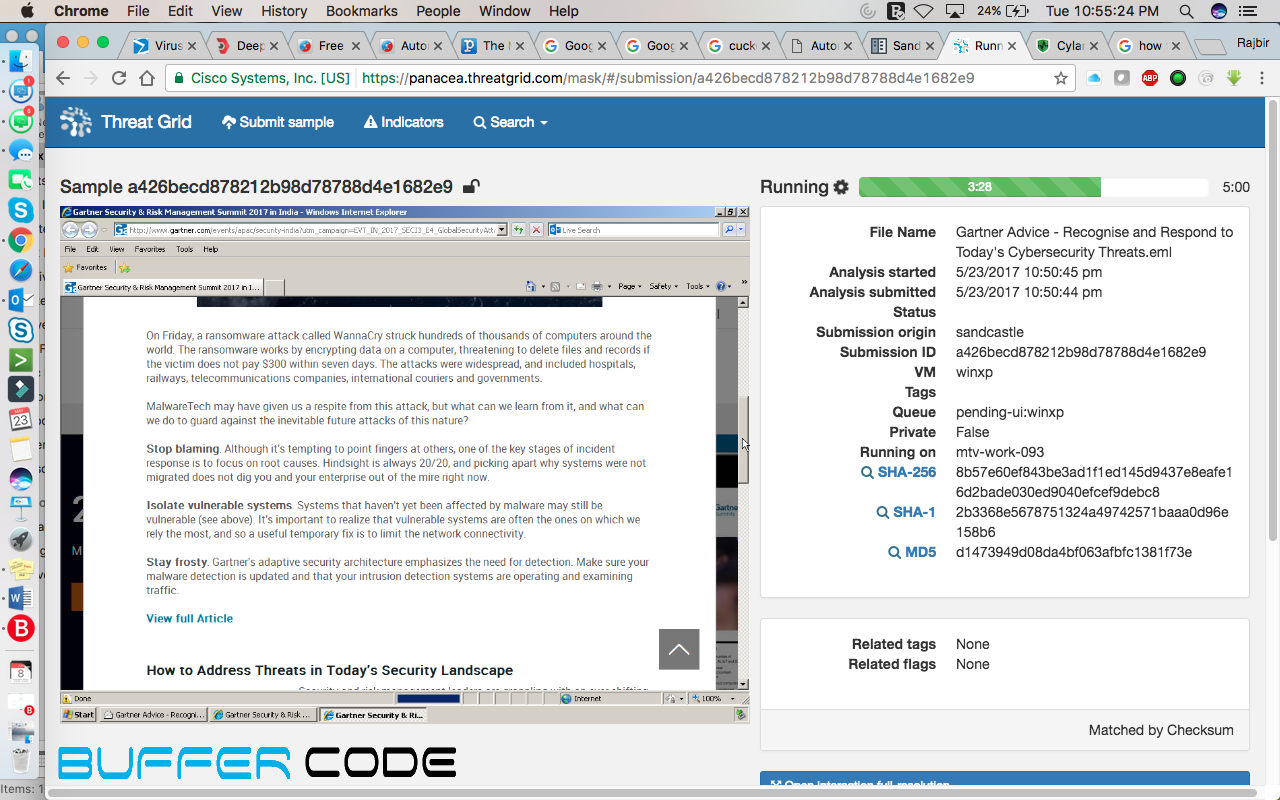 If any file got downloaded, then the virtual machine will execute that file and monitor the file behavior.
If any file got downloaded, then the virtual machine will execute that file and monitor the file behavior.- In a paid sandbox environment, you can see all these activities happening live in the environment. While in the free version like hybrid analysis or virus total, we will get a report of the submitted file.
Below is the link to the generated report on the above analysis of Gartner’s email.
Report on Gartner_email
Screenshots attached below were taken from the report of the latest ransomware “Wannacry”. This report was generated by one of the paid sandbox named Threat Grid provided by Cisco.
Have something to ask? Please contact us on the social network.
Follow us on Facebook, Linkedin and Twitter.