Note: Hacking is not a joke so please keep patience and learn it step by step.
If you have read all our previous posts , you are ready to exploits the system. So after cover all basics and necessary things it’s time to moving towards exploits. Lets start from Buffer-code overflows .
There is a basic question that what can buffer-overflow do in exploit , so lets see the power of buffer overflows here.
So if you are ready to moving towards exploit ,lets start:
What are Buffers ?
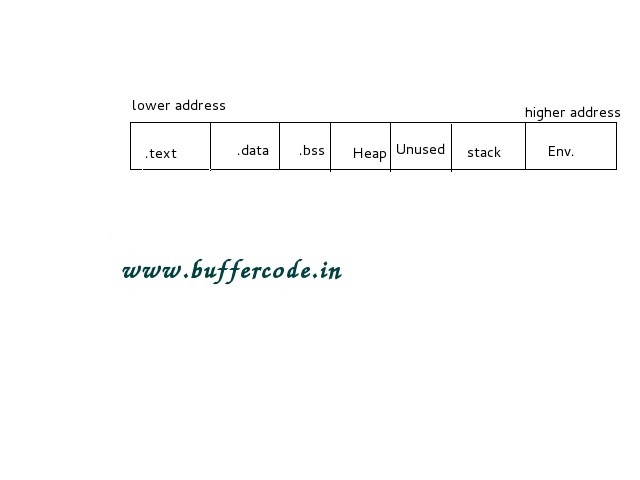
Buffers are basically use to store data in memory. While we are moving towards buffers we are basically interested in special types of buffers , buffers that can store strings or say that can hold strings.
Problems with buffers
There is a basic problem with bufffers that they itself have no mechanism to handle exception i.e, putting to much data into the reserve place.
Lets see an Example :
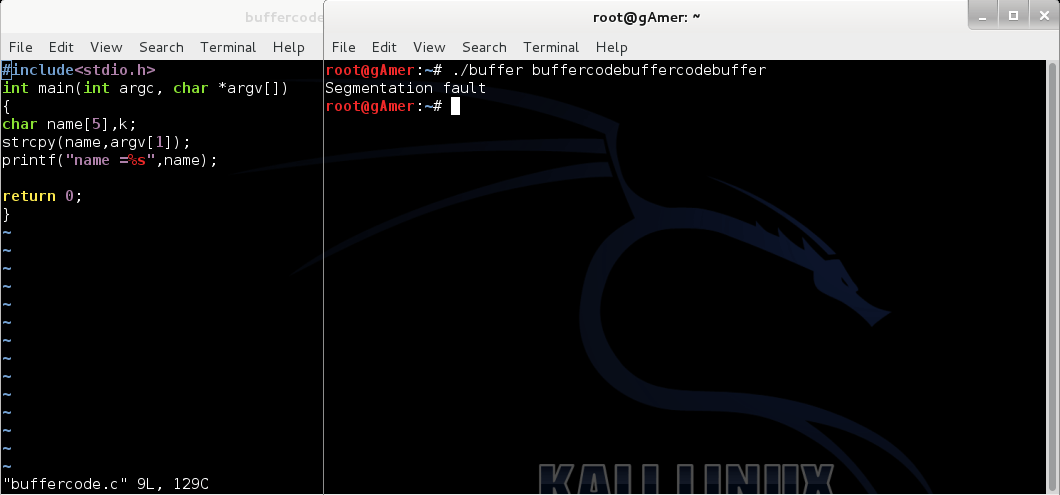
Try to copy 25 characters in a character type array of size[5]
Look at the code:
#include<stdio.h>
int main(int argc, char *argv[])
{
char buffer[5],k;
strcpy(buffer,argv[1]);
printf(“buffer =%s”,buffer);
return 0;
}
What just happens?
Output : segmentation fault
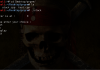
Look at the screenshot below
This is we did to crash whatsapp , we just passes a large string of special characters which it can’t handle and just start crashing repeatedly .
But it’s not the end of our exploit tutorial even it’s only the starting. As I said before “Hacking is not a joke so please keep patience and learn it step by step.” So please stick with us , in our next post we will show you by debugging it, and will tell you how to find it’s eip or rip(instruction pointer ,which will help us to make a jump for next instruction).
Have something to add in Basic Linux Exploits: Moving towards exploits?? Please share in comments.
Follow us on Facebook, Google Plus and Twitter.