EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
What’s in the LOG?
- The information you need to answer
- Who’s attacking us today? and
- How did they get access to all our corporate secrets?
Every time there is some activity in your device, it will create a LOG for you. Now the matter is how to find and analyze these LOGS.
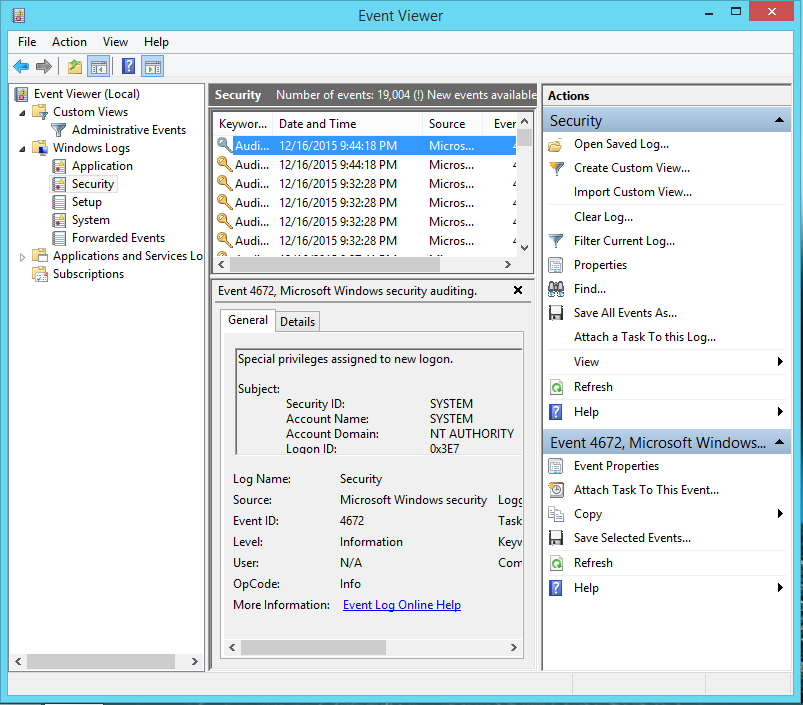
How to find LOGS in windows device?
It depends on the type of device you are using, for ex- In the Windows system, there is an Event Viewer. Below are the steps to view windows logs.
- Press Windows+ S to search and type “Event”
- Click on “View Event Logs”
An event viewer will be open. There you will find your windows logs. Similarly every device or application, either it is windows or cisco router creates logs.
But now the main challenge is to manage and understand these logs. If you go through these logs you will find it a bit complex and in the unmanaged form so there are some tools which use to create ALERTS, WARNING, and REPORT on these logs EX: RSA SA, IBM Q-RADAR, Splunk, etc. You also can investigate through these tools on the basis of some in-built or customized rules.
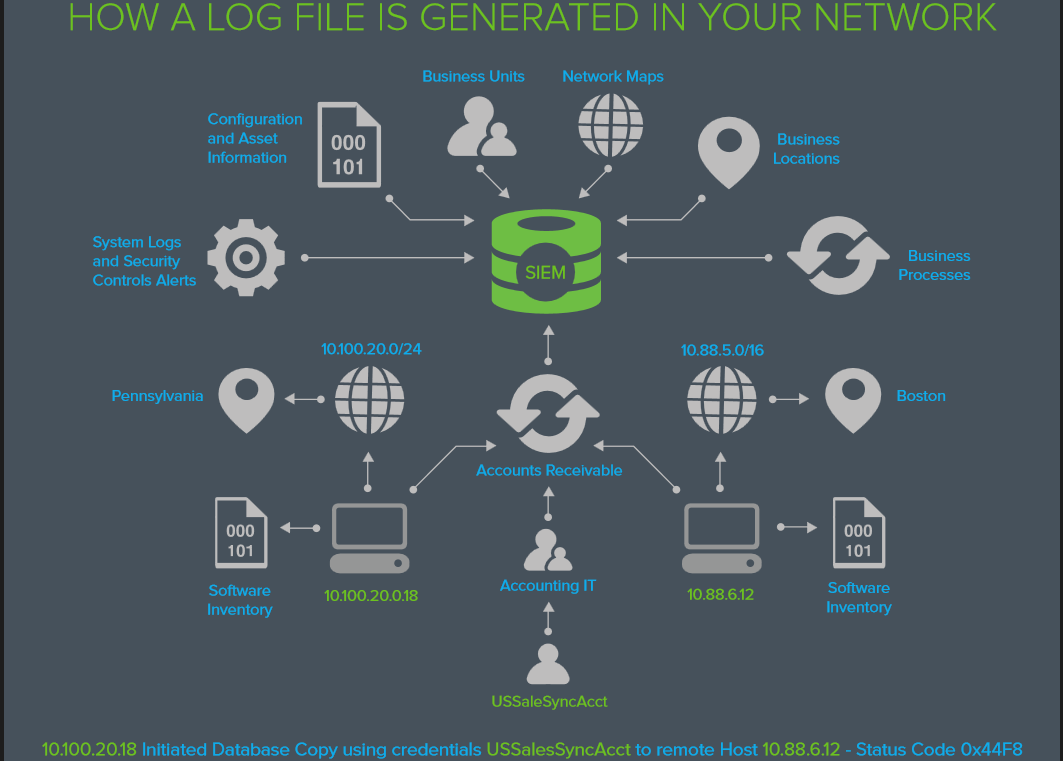
SIEM A Single View of Your IT Security
SIEM is about looking at what’s happening on your network through a larger lens that can be provided via any one security control or information source.
- Your Intrusion Detection only understands Packets, Protocols & IP Addresses
- Your Endpoint Security sees files, usernames & hosts
- Your Service Logs show user logins, service activity & configuration changes.
- Your Asset Management system sees apps, business processes & owners
None of these by themselves can tell you what is happening to your business in terms of securing the continuity of your business processes… But together, they can.
SIEM stands for Security Information and Events management, which is nothing more than a management layer above your existing devices and security controls.
In other words SIEM is a technology connects and unifies the information contained in your existing systems, allowing them to be analyzed and cross-referenced from a single interface. The more valid information depicting your network, systems, and behavior the SIEM has the more effective it will be in helping you make effective detections, analyses, and responses in your security operations.
We can create rules based on the use cases such as: For the Brute-Force attacks in which attackers use a dictionary of passwords to crack the password, we can create a rule for multiple login failures followed by the same IP / username/ password(for reverse brute-force).
It will generate a warning + alert and then you can easily investigate the case.
Similarly, we can create alerts for a new user creates or privileges change for the non-admin users, etc.
In next article we will discuss about how industry works with SIEM and Security Analytics.
Have something to add ?? share it in comments .
Follow us on Facebook, Linkdin and Twitter.