Camscanner is scanner application available in google play and app store. Recently, it is found as a front for disseminating malware on gadgets and has been expelled by Google from the Play Store.
The recent report on the vulnerability by security specialists from Kaspersky Lab uncovered that the CamScanner has been conveying malware. Prominently, CamScanner is a famous photograph examining application that enables clients to make PDF, and furthermore has OCR (optical character recognition) abilities.
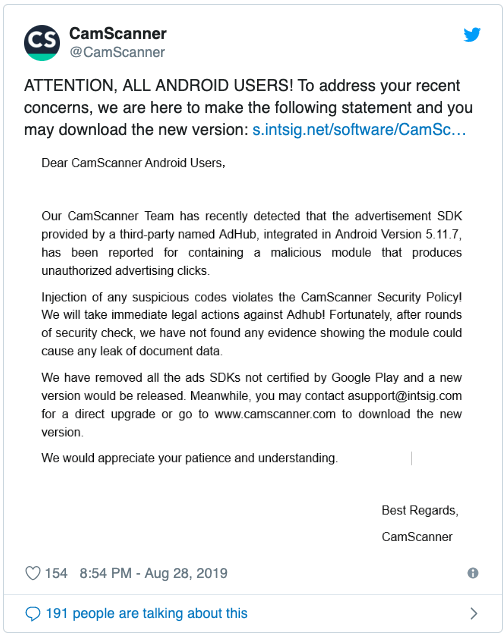
CamScanner has recognized that a malicious module was available in the promotion SDK of CamScanner Version 5.11.7. The SDK was evidently given by the third party called AdHub and was creating unapproved advertisement clicks.
The organization guarantees that it will make a quick legitimate move against Adhub since the infusion of any suspicious code damages the organization’s security strategy. Furthermore, no proof of any record breaks has been found after ’rounds of security checks.’ CamScanner has clearly evacuated all the promotion SDKs that are not ensured by Google Play and is discharging another form that can be at present downloaded from the organization’s site.
Kaspersky Labs has also stated, “malicious code may show intrusive ads and sign users up for paid subscriptions.” Such intrusive ads are irritable and no consumers will pay for subscriptions they have not subscribed for.
What should users do?
It is strongly recommended to uninstall the app immedietly till it will be available again on play store or next official update. A good antivurus can also be useful for detection of malicious application installed on your mobile.
Also, it is recommended for our users to check for the unnecessory permissions asked by installed applications and read reviews by other users for the same.
“The application’s free version is currently unavailable on the Google Play Store while the paid version urges users to update the app to the latest version as soon as possible. The app contains a Trojan dropper which has been configured to connect to attacker’s servers and download additional code. The code is then executed on Android devices which has the application installed.”
The malware module was spotted distinctly on the Android variant of the application and it appears as though its iOS adaptation is as yet accessible on the App Store, likely as a result of Apple’s exacting application checking arrangements. As per the Kaspersky blog notes, CamScanner was a quite decent application that offered outstanding usefulness. While it showed promotions for creating income, there were possibilities for in-application buys and purchasing a License independently for disposing of advertisements. Be that as it may, the Trojan-Dropper module found inside the application is said to concentrate and run another vindictive module from a scrambled record incorporated into the application’s assets.
Have something to ask???? Please ask in comments or contact us.
Follow us on Facebook, Instagram and Twitter.