Attackers use ransomware to get ransom from its victims. In other words, ransomware is a malicious program or software to block user access on their own system or encrypt user data asking for ransom to unlock the system or decrypt the data.
Simple ransomware locks the system and displays a message to pay the ransom in exchange to unlock the system. Its not difficult to crack down a ransomware for a knowledgeable person.
Advanced ransomware may encrypt the files from user system as well as the user hard disk and make them inaccessible leaving the attacker to demand ransom for decrypting the files.
Trojans mostly leads to ransomware attacks carried by any legitimate file or email to the victims system. The downloaded file runs the malicious payload or contains Trojan that locks the user system or encrypt the file/hard disk.
Also check: What is sandboxing and how it works?
Ransomware attacks happens in four round:
- Ransomware targets the user system via email, attractive ads or any malicious sites. When the user clicks on the link received in email or clicks on the ads it downloads and runs the malicious program that locks the user system.
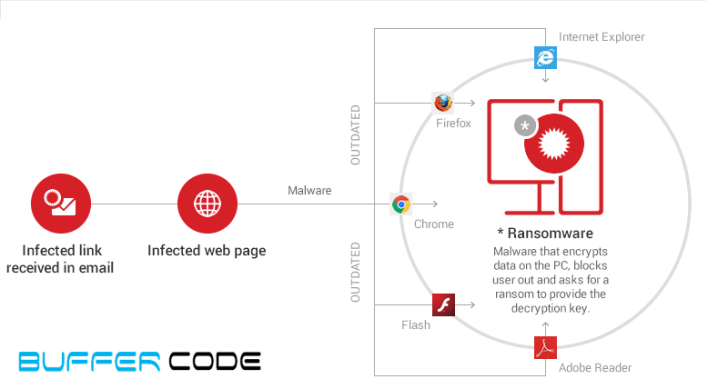
- The malicious program locks the user system or encrypt the file, displays few codes and a ransom message to unlock the system or decrypt the files.
- The victim sends the code and pay ransom as demanded. The Attacker receives the ransom to unlock the system or decrypt the files.
- Ransom is the main goal of attacker. There may be chances that the attacker provides code to unlock the system or decrypt the file or by supplying another program that can decrypt the files.
Various types of ransomware involved in the cybercrime activity:
-
- Encrypting Ransomware: AIDS Trojan used in malware attack to get extortion. However the ransomeware is not a success because of the design failure that encrypts only the file names.
- Non-encrypting Ransomware: Also called WinLock came into picture. It removes the user access and displays an extortion message of ransom to unlock the system. Another ransomware was detected that displays a message of windows product activation. An online windows activation option was offered similar to genuine windows activation process removes the user access from the system as soon as the user clicks on it
- Leakware or Doxware: It steals and threatens to publish the user data if the ransom is not paid. It does not removes the user access.
- Mobile and Smart TV Ransomware: With increasing popularity in ransomware, the attackers are targeting smartphones and smart TV users. Mobile ransomware mainly targets the android/IOS users because of third-party application installation.The infected application asks for root privileges after installation. The user accepts the requests assuming to be a step of application installation. After getting the root or admin access, ransomware blocks user access to the device and displays a ransom message to unlock the device. Various methods are tried by attacker for instance iCloud account login and lock the device using find my phone for iPhone users. Apple introduced patches for all the bugs before the vulnerability got exploited.
- Cryptolocker Ransomware: Ransomware reappeared in 2013 with a known Trojan called CryptoLocker. This ransomware use 2048 bit RSA key to encrypt data and upload it in C2C server. It displays a ransom message of deleting public key if it is not paid within three days.
It collected around 3 million us dollars before wiping it off. - Cryptowall Ransomware: It spread as a part of malvertising on Zedo ad-network. The advertisement redirects the users on rouge sites to download the malicious payload using browser plugins. Sometimes, the payload is signed with a valid digital signature to show it is a part of security software.
Another version of cryptowall ransomware writes java script in an email attachment that downloads executable in form of JPG image is created.Furthermore another version of this ransomware is used to create new process in the system named explore.exe and svchost.exe. Both are legal process of Microsoft windows and the difference can be found out by monitoring the activity of these process. We can find them communicating to their Command and control servers or the master servers on which they can transfer data remotely.
These ransomwares were used to delete the backup copies after encrypting the files or the data. In that case the user would have nothing to recover than to pay Ransom.
The most recent version of this ransomware is cryptowall 4.0 that hides itself from antivirus detection and encrypt the file name as well as encrypting the files.
Example of ransomware activity:
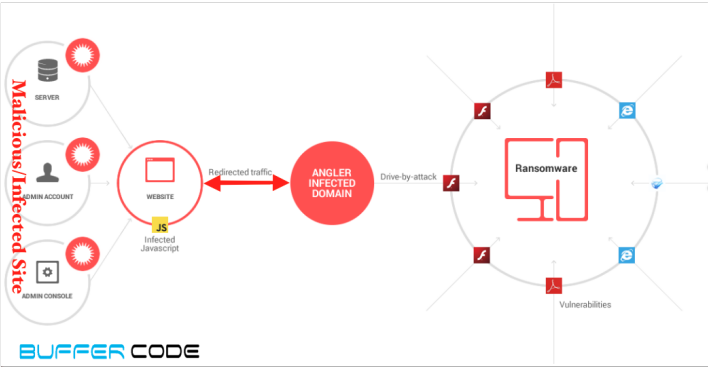
Below is a ransomware example where a malicious java script and ransomware is downloaded.
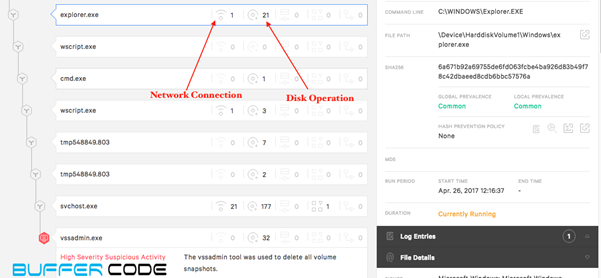
- Full process table of ransomware activity.
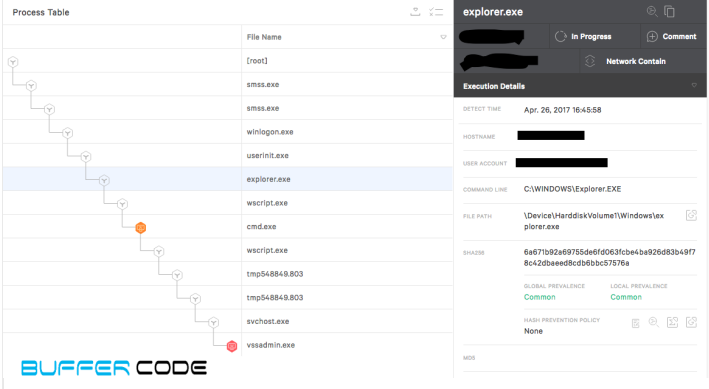
- As we discussed above, new ransomware use the legal process in the system to execute ransomware payload. In this example explore.exe downloads a malicious java script.

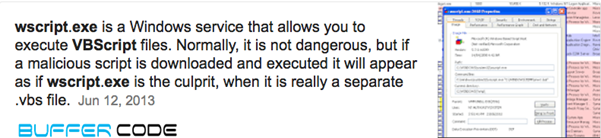
- Another legal process wscript.exe runs a malicious java script named “270828.js” through command line.

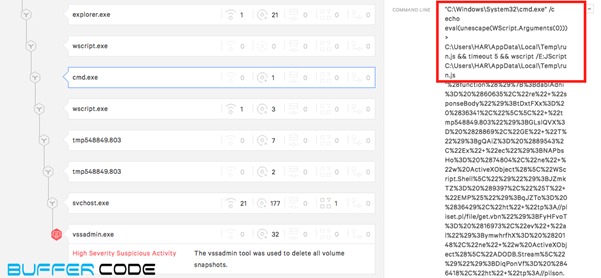
- Another legal process cmd.exe writes a malicious java script named “run.js”.
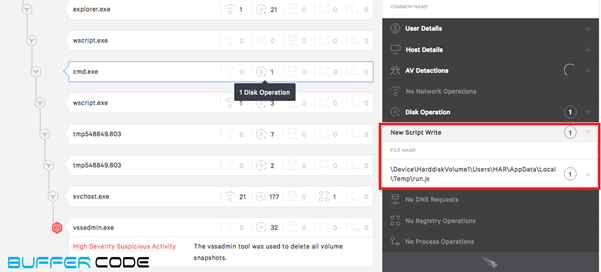
- Again, Wscript.exe runs the java script to connect with malicious site and downloads another malicious payload.
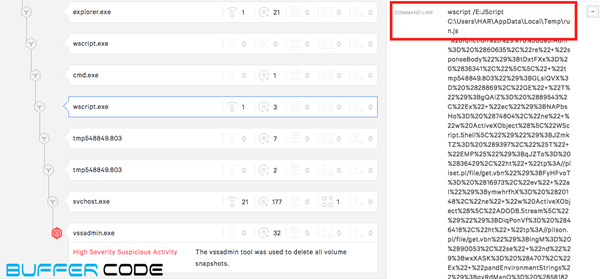
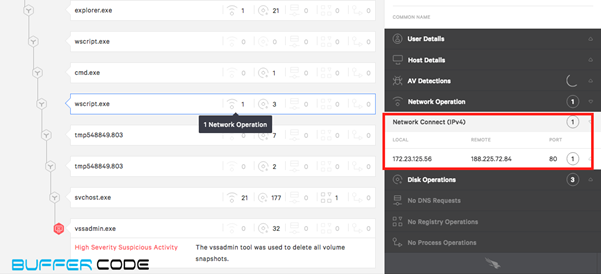
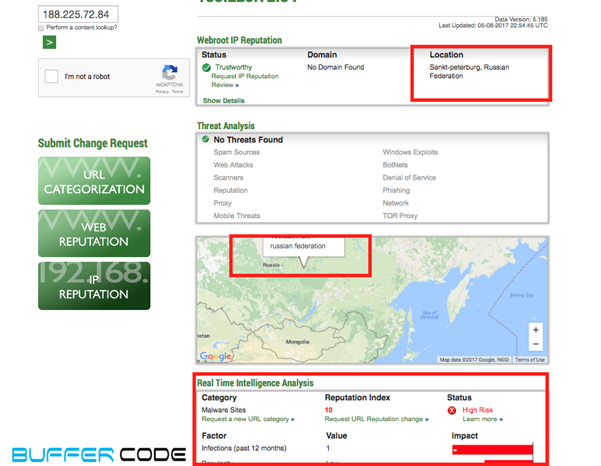
- Let’s check the IP reputation, whether its a safe connection or connecting to a malicious site. Wow, the IP belongs to a Russian federation that hosts a malware site. The downloaded java script is connected to this malware site.
- Java script downloads another malicious payload named “tmp548849.803” from the malware site .
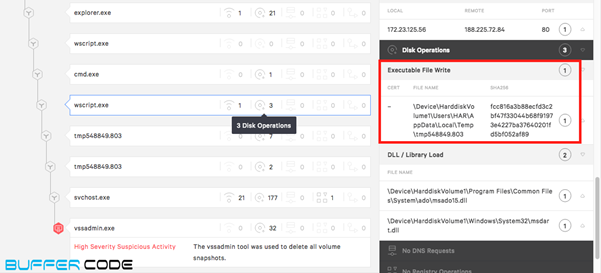
- The malicious payload is ransomware payload. It is detected as malicious by around 38 antiviruses, also a few antiviruses were able to detect that this payload relates to a ransomware.
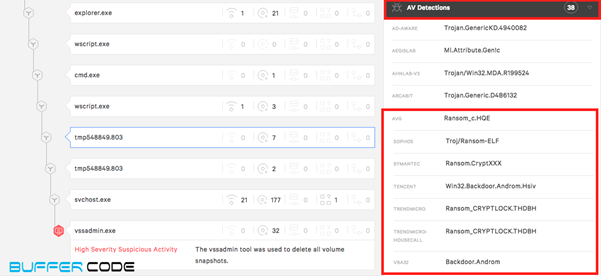
- This malicious payload run and writes few .dll file downloading another malicious program.

- Newly written .dll runs svchost.exe to connect with other malicious IP addresses.
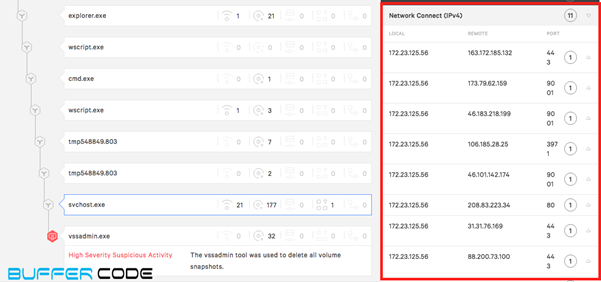
- Svchost.exe connects to malicious IP address and downloads a ransomware file named “ullivunan.exe”
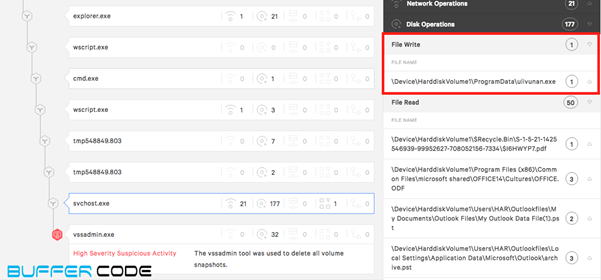
and modify the registry to run that file.

that file runs and encrypts all the files in that system.
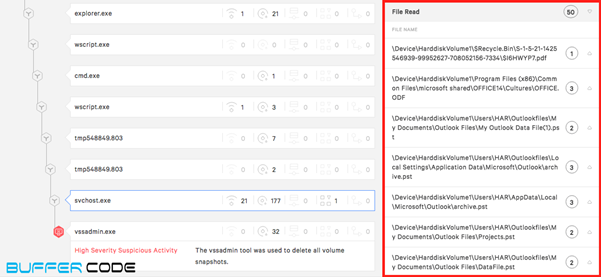
- Consequently vssadmin.exe deletes all the backup snapshots, so the user cannot recover from backup files. After encryption of all the files the user receives a ransom note on his system screen.

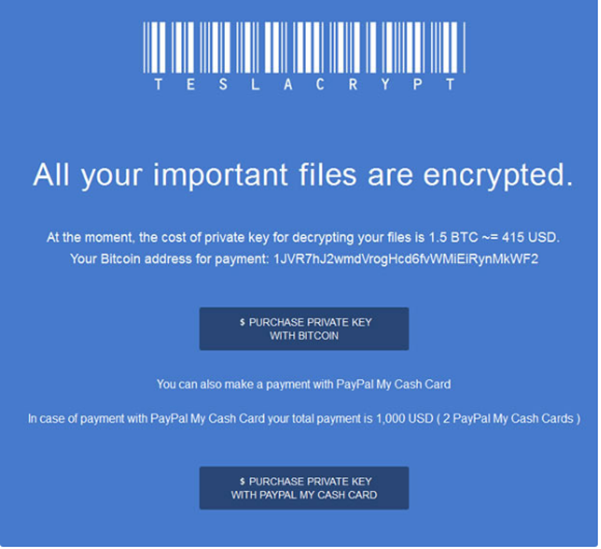
- The user communicates the situation to his security team realizing the system to be compromised.
- The Security team investigates the ransomware activity and suggests the IT team to re-image the system and recover the files from offline backup.
Things to remember:
We cannot eliminate the cyber risk completely however the attacks can be minimized using good detection and prevention technology we can mitigate them and we can stop damage to our data.
Mitigation steps: – Ransomware payloads are not detectable by security software or antivirus. Ransomware can be stopped from encrypting data if such payloads or malicious programs are detected . Because ransomware payloads takes time to encrypt the files.
We can stop damage to our data by immediately removing the malicious program, adware and extra plugins that gets added from an unknown source.
Deception technology is designed to tackle ransomware . Deception technology works on non-signature based approach to detect ransomware or any other threats. This technology uses fake SMB data shares into the real IT assets. These fake SMB used itself to deceive ransomware and make busy ransomware in encryption of fake SMB. Along with this technology alert and notify security team that helps to stop the attack.
- Security researcher and experts have suggested few important precautions to deal with ransomware and other threats.
- Use a policy to block all known malicious payloads and any other payload that we found suspicious.If it requires in an organisation, then it can be unblock on request of user and team.
- Always keep backup of your system and servers.
- Keep your backup file offline or in cloud in distributed mode.
- Remove plugins like Flash player, Java and others from your browser if you don’t require them.
- Set the browser to ask me if I want to activate these plugins when needed.
- Keep a good and reputed full version antivirus with web protection, installed in your system.
- Keep your security application up-to date.
- Use an ad blocker to stop malicious ads.
- Never pay ransom, by doing this you are motivating the attacker to do it again with you or any other.
Have something to ask???? Please ask in comments or contact us.
Follow us on Facebook, Instagram and Twitter.