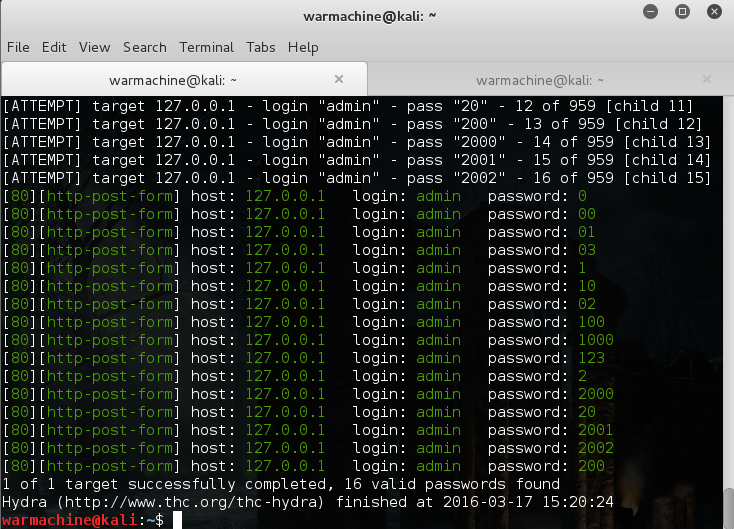
In our previous article How To Crack Password Using Hydra In Kali Linux , we have discussed about THC Hydra- A tool for Online Password attacks. In this tutorial we will discuss about How To Crack Web Form Passwords Using Hydra With Burp Suite .
What is Burp Suite?
Burp Suite is an integrated platform for performing security testing of web applications. Its various tools work seamlessly together to support the entire testing process, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities.
We will be attempting to crack web form passwords on DVWA- Damn Vulnerable Web Application. You can download it from here.
Prerequisite To Learn-How To Crack Web Form Passwords
- Running DVWA
- Installed Hydra
- Installed Burp Suite
Note: You can use kali-linux , Hydra and Burp Suite are pre-installed application of Kali-Linux.
Steps to Crack Web Form Passwords
Step 1: Determine the web form parameters
To Hack/Crack Web Form Passwords, we need to find some parameters of web form and also how it responds to failed/ bad login. The key params we need to identify are:
1. IP Address of the website 2. URL 3. type of form 4. field containing the username 5.field containing the password 6.failure message
We can use web application proxy such as paros or burpsuite to identify these parameters.
Step 2: Using Burp suite to identify above parameters
As we told you that we can use any proxy tool including Tamper Data and Paros Proxy to identify these parameters, in this tutorial we will use Burp Suite. In Kali Linux 2 you can open burp suite by pressing window key and type burpsuite in search or by going to Applications ->Web Application Analysis -> Web Application Proxies -> Burpsuite.
Step 3: Running Damn Vulnerable Web Application(DVWA)
Now we will be attempting to crack the web form password on the Damn Vulnerable Web Application. Its login page will looks like the page in below image.
Now after opening burp suite we need to enable the proxy and intercept as shown in below image. Please make sure that “intercept is on”.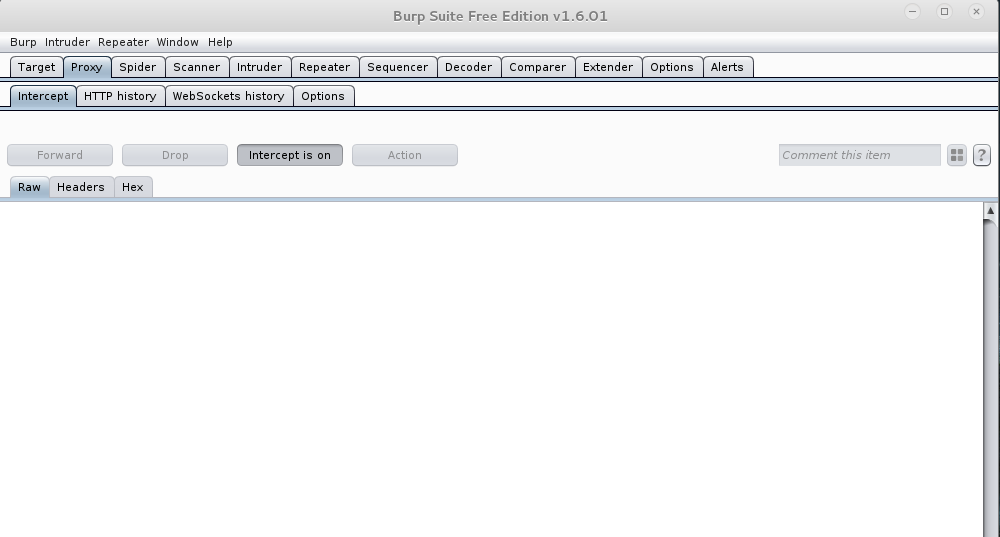
If you have configured it as need to be, it will start showing Bad Login responses. So let’s try… 😉
Step 4: Get key fields we need for THC-Hydra
Open your Iceweasel browser and setup proxy settings for burpsuite. Now open DVWA app such that it start showing login page. Now enter username as buffercode and password as buffercode and hit login button. When you will do so burpsuite will intercept the request and show us parameters we need for THC-Hydra.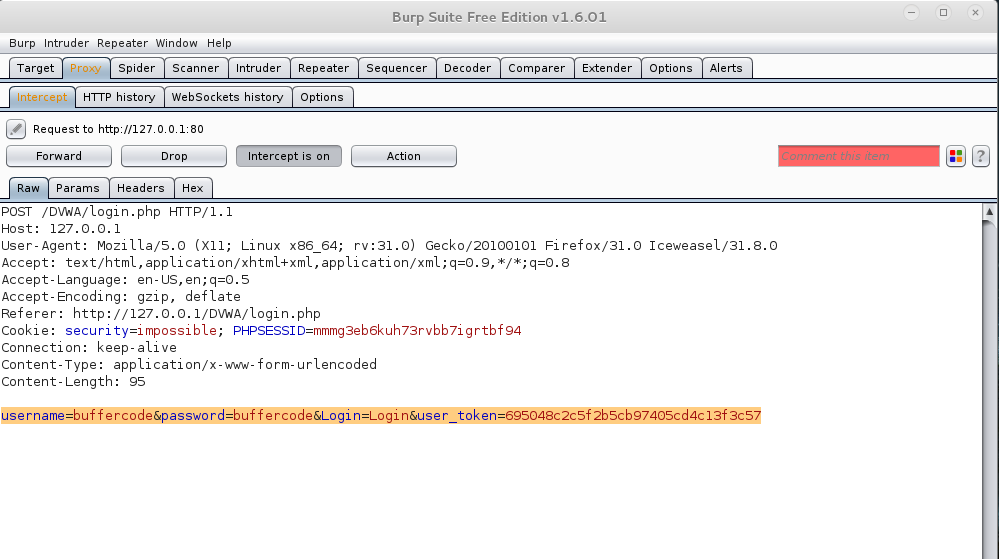
After getting this information(parameters), we then forward the request from burp suite. Forward button is far left from “intercept is on” button. Now return to the browser, there DVWA will show Login failed message. We need Login Failed message because Hydra will try till Login Failed message will be there. Only when that message doesn’t appear have we succeeded.
Step 5: Using THC-Hydra to Crack Web Form Passwords
Now we have all the information we needed for THC-Hydra to crack web form passwords. So now it’s time to place these parameters into the THC-Hydra command. Below is the syntax for command:
warmachine@kali:~$hydra -L <user list> -P <pass list> <ip address> <form parameters> <failed login message>
Now insert your information you get from burp suite as per the above syntax .
warmachine@kali:~$ hydra -L "wordlist" -P "password list" 127.0.0.1 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Log in failed"
Note: Here use capital “L” and “P” for list of username from file while small “l” and “p” for one username and password. You can use hydra -h for more options.
Step 6: Final step
Now it’s time to build the final command with proper wordlist. As in any dictionary attack we need to choose a wordlist. There is multiple password list available, but in this guide we will use default password list provided by John the Ripper which is another password cracking tool. Now enter the final command, it will looks similar to below command.
warmachine@kali:~$hydra -l admin -P /usr/share/dirb/wordlists/small.txt 127.0.0.1 http-post-form "/dvwa/login.php:username=^USER^&password=^PASS^&Login=Login:Login failed" -V
Eh! her 16 valid passwords found 😀
Things to Note
It is not as easy to crack passwords as in DVWA. Even there may be many challenges like some sites will lock you out after getting some wrong passwords etc, you need to practice more and more to find and win over those challenges. You can ask your doubts in comments and we will try to help you as much as we can. One last thing “don’t try it for bad purpose”.
Have something to add in How To Crack Web Form Passwords Using Hydra With Burpsuite In Kali Linux?? Please share in comments.
Follow us for more hacking tutorials on Facebook, Google Plus and Twitter.