Today, we will discuss how to find, a file is safe or a threat for your system?
Or we can say, how to do malware and threat analysis?
Watch Video on Malware analysis | Threat analysis | How to make sure a file is safe or threat?
In today’s world, it’s very hard to find that which file is safe or which file is suspicious and threat for the system. Because threats also comes with genuine file name, also signed with some fake certificates.
Many of threats comes in the form of .dll, .exe, weaponised PDF, weaponised word documents and software downloaded from malware site or phishing sites, adware etc.
Malware: –
Malware are the programs that are specially designed to disrupt the services, damage your systems or provide authorized access to the attacker. It comes in different forms like virus, Trojan, risk-ware, spyware, adware, ransomware, scareware and another malicious program. Well, we will discuss in another post about malware types and their activities.
As day-to-day security techniques are improving, hackers are also improving their techniques and skills to attack on targeted user or to hack their system or sites. They have created lots of advance threats that are nearly impossible to detect by a single antivirus.
Also, it’s true that one user should not have more than one antivirus installed in their system. Because it will be too costly for the user. It will also impact the system performance.
Now we have question that how can we identify that a file is safe or it’s a threat for your system? or how we can feel protected?
Threat Analysis: Below are the steps to identify a file is safe or it’s a threat?
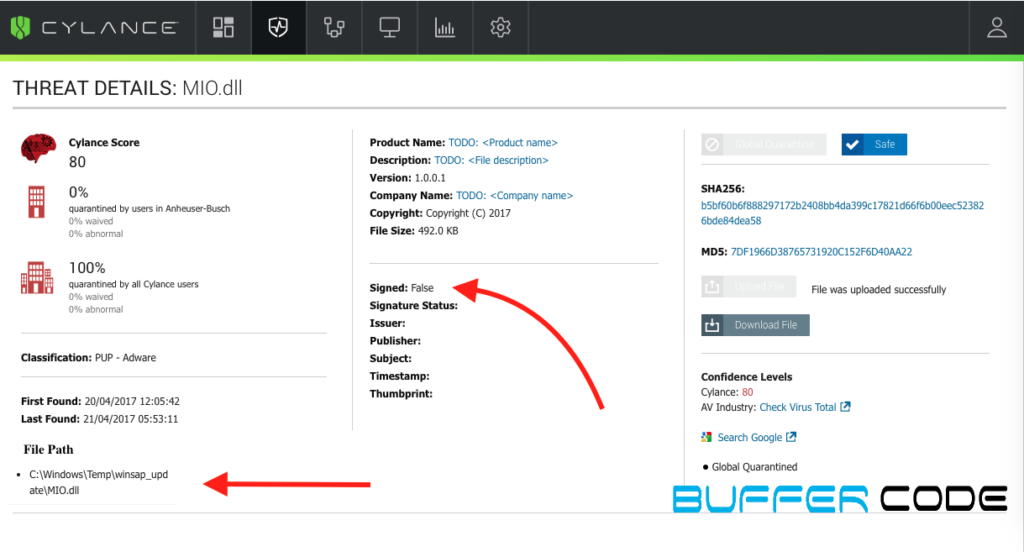
Today, most of the threats comes in the form of genuine file or attached with ads or any other program files. So, there are chances that antivirus can miss that file to detect as threat or also can detect a genuine file as a serious threat. See below example, as per the file name and file path its look like its windows file.
In this case, before we allow that file to run in our system we need to confirm either it is safe or infected.
- To check file reputation in virus total, we can use file hash
- But in few antivirus, we don’t get file hash so download the file and upload it in to Virus total to check what other antivirus tells us about this file
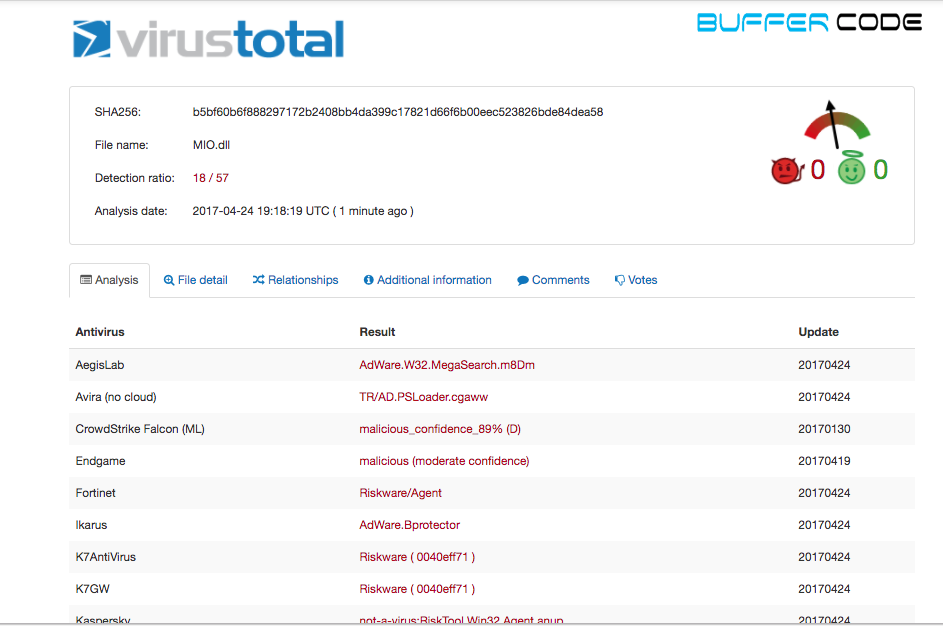 As per virus total, out of 57 antivirus 18 says it is virus or riskware. It mean we should remove this file. But still it’s confusing because 39 antivirus didn’t found it malicious. So we need more proofs to make sure that we should allow this file or block this file.
As per virus total, out of 57 antivirus 18 says it is virus or riskware. It mean we should remove this file. But still it’s confusing because 39 antivirus didn’t found it malicious. So we need more proofs to make sure that we should allow this file or block this file. - Let’s run this file into a sandbox environment. We have lots of sandboxing option like hybrid analysis, Cuckoo, threat-grid and more. Here we will use open source sandbox environment called Hybrid analysis to get more detail about this file. [We will discuss later about what is sandbox and how it works]
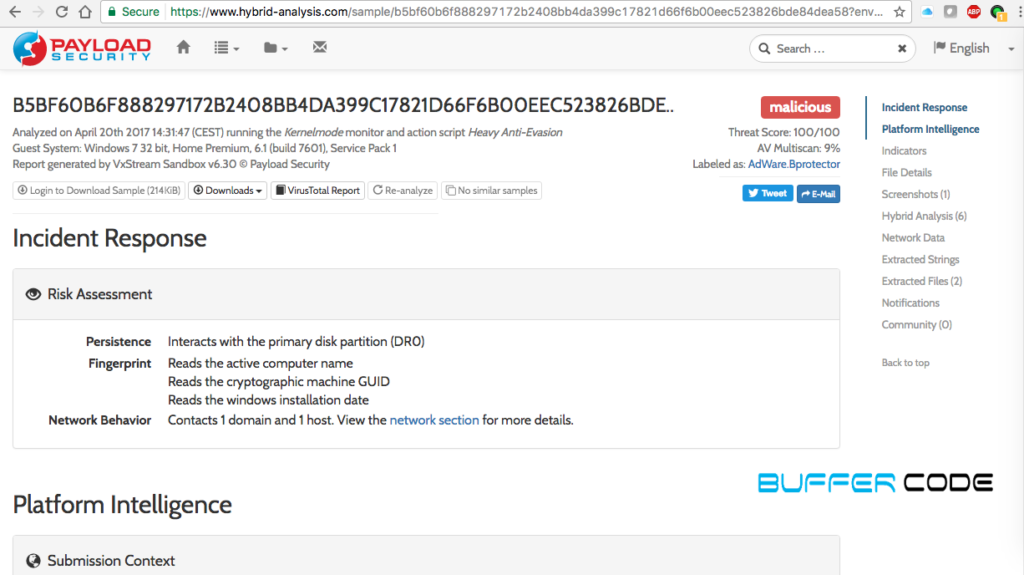
- In above step, we run the hybrid analysis and found file is 100% malicious. We can check in all sections to get all IOC which are proof of this file to say Why it is 100% malicious .
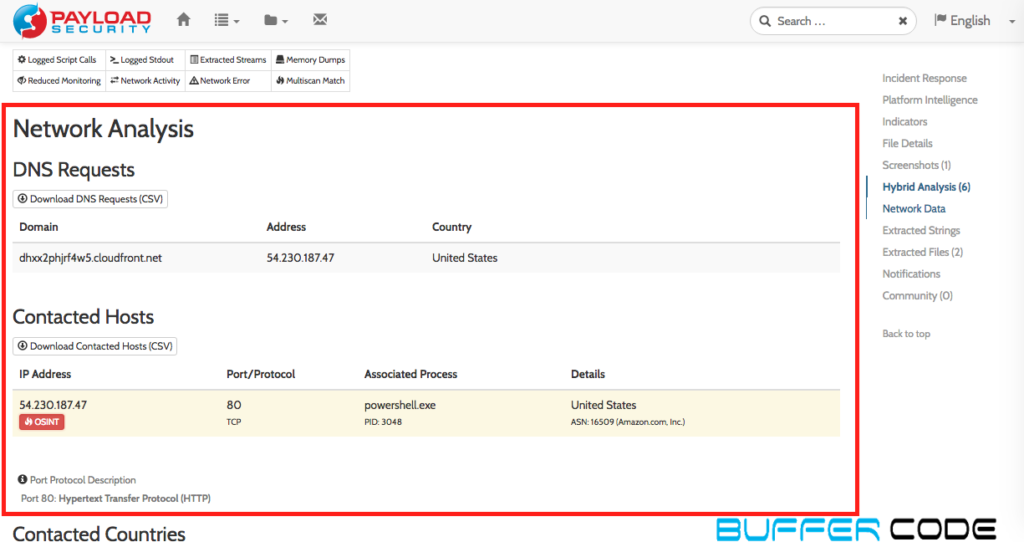
- You may find network analysis of this threat much interesting because it is connecting to a wired domain associated with IP [542.30.187.47] and county location in US. It also uses powershell.exe to connect with that domain which makes it more interesting. [you can check all the strings into other sections]
- Copy the IP/URL and check into URL/IP scanner site called bright cloud.
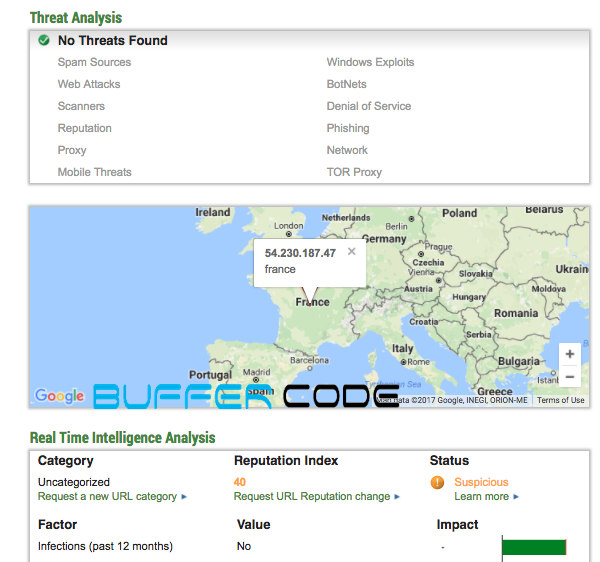 We checked the IP reputation and found it is trustworthy but suspicious.
We checked the IP reputation and found it is trustworthy but suspicious.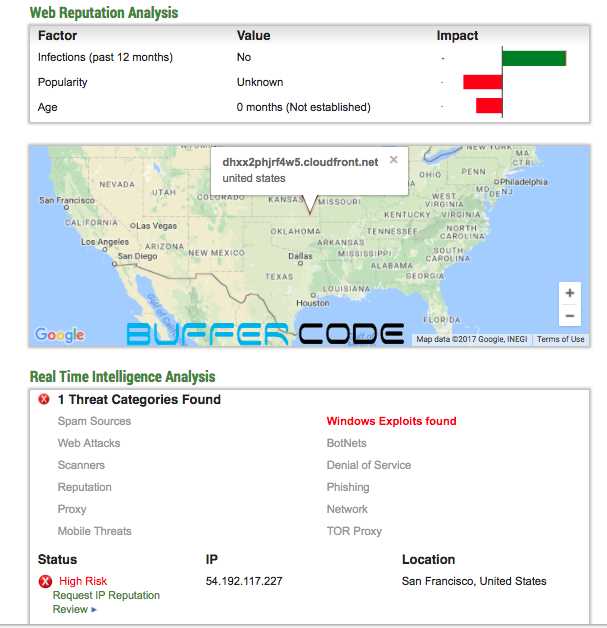 Here, we checked the domain reputation and found it is related to window exploits.
Here, we checked the domain reputation and found it is related to window exploits. - In above step we found, this file is trying to communicate with a domain that is related to windows exploits. It make our system vulnerable so we should immediately block this file or if in an organization then we should add this file or Hash in auto-quarantine list. Once file comes into the system antivirus will auto-quarantine this file.
SEE ALSO:An Almost Impossible To Detect Phishing Attack Using Punycode
How you can feel safe or protected?
- Always install full version of antivirus. Don’t hesitate to buy, if you can not get crack, that will be worth it.
- Keep your antivirus up-to-date. Schedule check for update weekly or set it on auto update mode. Antivirus will not wait for your permission to update its database with latest threat signature if it is on auto update mode.
- Schedule a full scan at-least once in every week.
- If antivirus detect any legitimate application as a threat than please cross check the source of that application and run a hybrid analysis on that file/application.
- If required talked to antivirus or application technical support team, about this issue.
- Make sure the application you downloaded are from trusted source.
- Most important, update yourself with latest threats and hacking techniques by keep visiting our site .
Have something to add in How to make sure a file is safe or threat? | How to do malware or threat analysis??? Please share in comments or contact us.
Follow us on Facebook, Google Plus and Twitter.