Important things to do after installing Kali Linux
There are small set of important softwares that are required after installation of Kali Linux. Linux operating system is not too much user friendly but it is highly flexible...
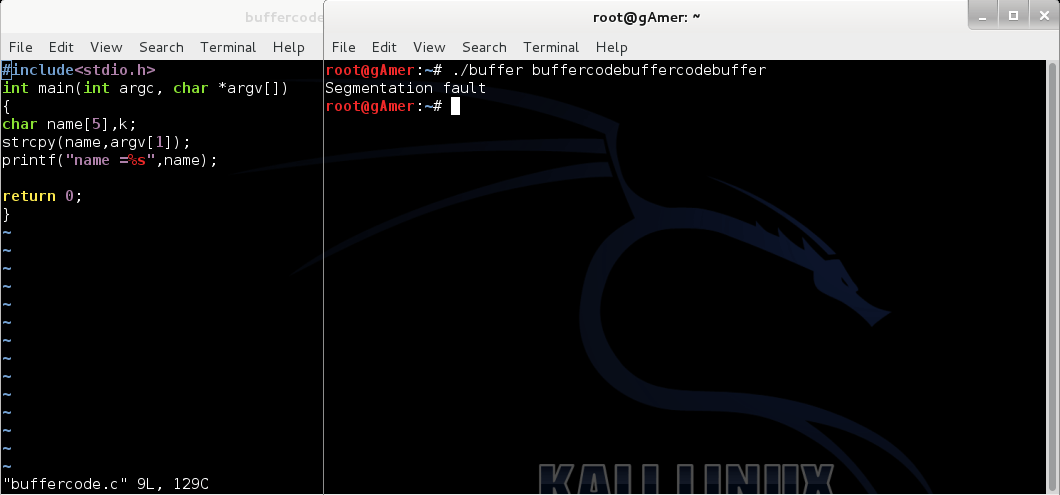
Exploit using shell code from command line
After reading our previous post:Exploiting buffer overflows using command line it's time to do Exploit Shell code using Command-line but I think you do want to clear your doubt...
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
The most popular Kali Linux was released on last week at DefCon 23 in Las Vegas.Kali is successor of Backtrack...
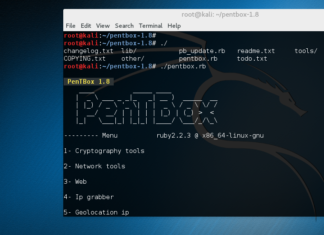
How to Install Honeypot on Kali Linux
In this article we will show how to install Honeypot in Kali Linux. The Pentbox is Security suite that can be use for penetration testing to perform various operations. The...
Managing Kali Linux Services
Managing Kali Linux Services
Kali Linux is a specialized Linux distribution aimed to test Network. The default Kali installation comes with several services preinstall like SSH, HTTP, MySQL, etc. These...
Basic Exploits : Stack Operations
Note: Hacking is not a joke so please keep patience and learn it step by step.
Stack Operations
First and the most important topic to learn the basics of Exploits is...
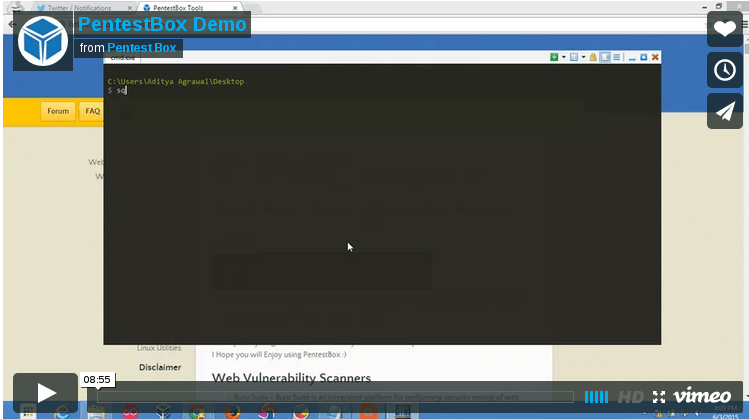
PentestBox: A Portable Penetration Testing Distribution for Windows Environments
Download SourceForge Download Torrent
PentestBox is a...
How to secure your account from phishing attacks on Internet
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Creating Phishing page to know the safety cautions
on Internet
To know the cautions we must know...
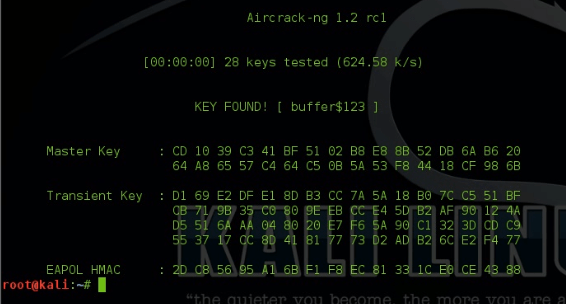
Hack WPA2 Encrypted Wi-Fi Networks using Aircrack-ng
Hack WPA2 Encrypted Wi-Fi Networks using Aircrack-ng | Kali-Linux
Hello friend ,In this article I will demonstrate how to crack or hack some one's WiFi Network just in simple steps...
Step-by-Step Guide to Install Kali 2.0 Linux in VMware workstation 11
The New Kali 2.0 codename as Kali Sana, is an open-source penetration testing platform having pre-installed hundreds of Hacking ,Reverse Engineering, Forensics and Penetration Testing tools. Kali 2.0 was redesigned...
Connect WiFi network from command line
Wifi connection is one of the most common issue in linux. In this article we will discuss how to handle this issue using command line. In this guide we...
Kali Linux Rolling Edition updated with the latest patches
The most popular Kali Linux was released on 2015 at DefCon 23 in Las Vegas. Kali is successor of Backtrack based on Debian Jessie,distribution, includes many popular penetration...
Exploit Development Process:Moving towards Real world Hacking
Now that we have covered basics of exploit , you are ready to look at real world examples like metasploit . As you all know - vulnerabilities in real...
How has open source changed the way students learn new technology
Open-Source Software (OSS):
is computer...
Latest tech trends (Internet of Things -IoT , mobile app development , cloud/distributed computing)
The Internet of Things?
The Internet of things, also known as the Internet of objects, refers to the networked interconnection of everyday objects.
The Internet of Things, or IoT, is emerging...
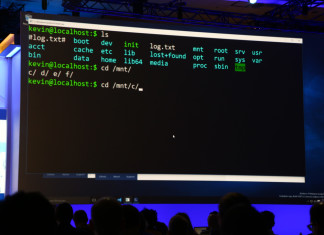
Windows 10 may have hidden linux subsystem
If you remember, in the end of last year every one was impressed from the announcement by Microsoft "Microsoft loves Linux". Microsoft also added about development of ACS (...
Microsoft is bringing the GNU project’s Bash shell to Windows 10
Microsoft announced that it bringing the GNU project’s Bash shell to Windows 10. If you remember, in our previous article :- Windows 10 may have hidden linux subsystem, we told you that Waliking...
Lava Iris Selfie 50 Affordable 5 inch HD Smartphone
Lava Launched it new Lava Iris Selfie focused smartphone is 5-inch HD display smartphone loaded with Android KitKat version 4.4.2.Lava Iris powered by 1.2GHz Quad Core Processor and 1GB...
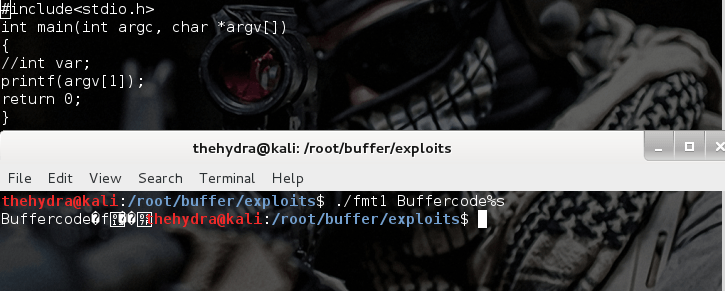
Format string exploits
Format string exploits became public in late 2000. It is easy to find errors in format string in comparison of buffer overflows. Once errors are spotted, they are usually...
Boss Linux Gonna Overshadow Windows in Government Desktops
Boss Gonna Overshadow Windows in Government Desktops
It seems that Indian government is taking concern and serious efforts in the area of cyber security. Well the new initiative by them...
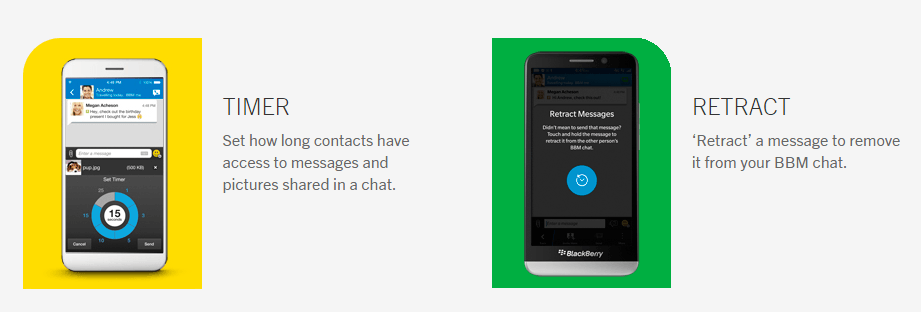
BBM BlackBerry now features timer just like Snapchat
Here is a good news for all BBM ( BlackBerry Messenger) Lovers, new Privacy features update which is live by BBM BlackBerry Application for all Android, ios or windows device....