Attackers are using facebook messenger to spread Locky Ransomware
Any Facebook message with an image file (.svg format) send by your friend can be a Locky Ransomware file, so just avoid clicking it.
What is Locky Ransomware?
Locky is ransomware released...
How to use backtrack
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Before you start
Before we start playing with safty tools follow the following steps :-
Download btr5...
Now BackUp Your WhatsApp Data to Google Drive
BackUp Your WhatsApp Data
The first thing comes to my mind when I think about losing my phone is “Oh! No I will lose all my data all the conversation”...
How To Crack Password Using Hydra In Kali Linux
Weak password is still a big problem in the world of security. User need to set a strong password to restrict the access of data from anonymous user. Even a...
Apple refused to unlock the iPhone on the enforcement of U.S Federal Judge
Once again the tech giant Apple has proved that how much they are concerned about the privacy of its users, and they will never break the users’ security for...
How to surf internet Anonymously
Hello friends this post is about how to hide your machine IP for surfing internet Anonymously. To read this may bore you but keep patience because it is important....
Mozilla Placing High Bandwidth Tor Middle Relays
Mozilla Placing High Bandwidth Tor Middle Relays
Mozilla Placing High Bandwidth Tor Middle Relays to add more secure anonymity in Firefox. Tor and Mozilla working together to provide a more...
Vulnerability in PayPal user authentication system
It's always a matter of attraction when money is in the frame of attack. So It's time to get into the users PayPal account.. Paypal provides online / ebay...
Demonbot is on rising | A New Botnet
As security is getting stronger so hackers are getting more stronger. Once a loophole is closed by Operating systems or any vendors then hackers find out another way to breach...
Shocking secrets about Ashley Madison: Women were actually not using the website
The hacked data of Ashley Madison website is been a reason for many criminal activities since it’s data is dumped on to the dark web (also known as deep...
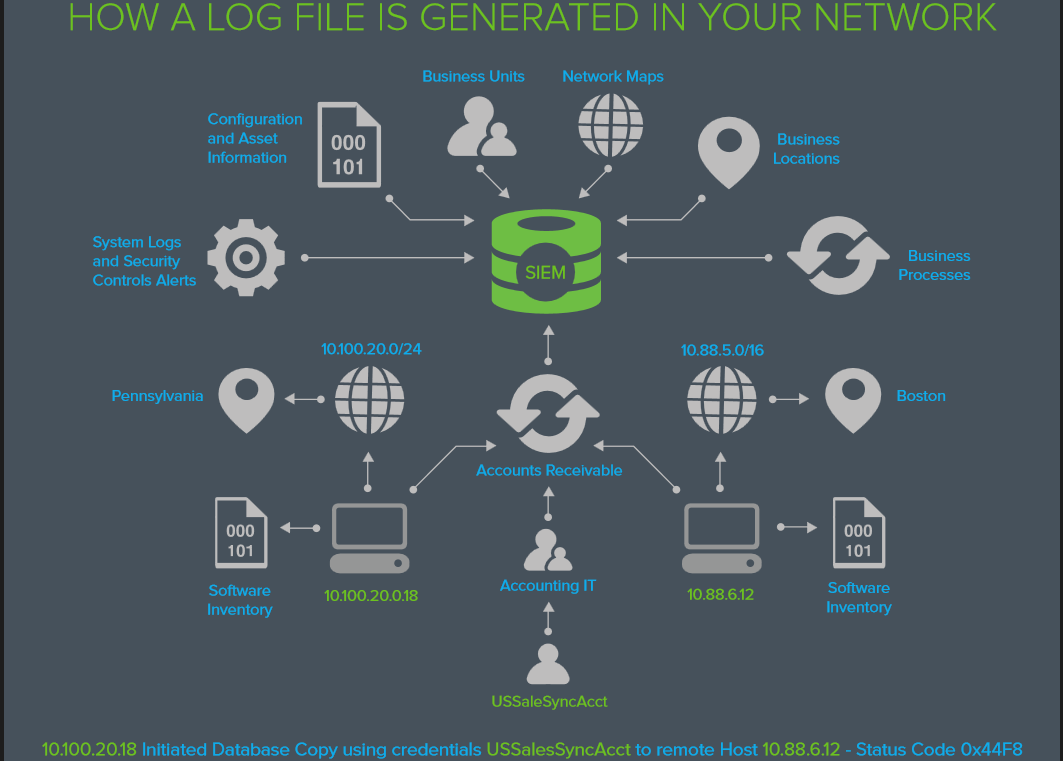
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
What’s in the LOG?
The information you need to answer
Who’s attacking us today? and
How did...
Three Vulnerabilities Of Starbucks Website: Credit Card details in Risk
The famous coffeehouse Starbucks is undoubtedly the best in its class and taste but registering yourself on the website of Starbucks could be dangerous. The registered accounts and credit...
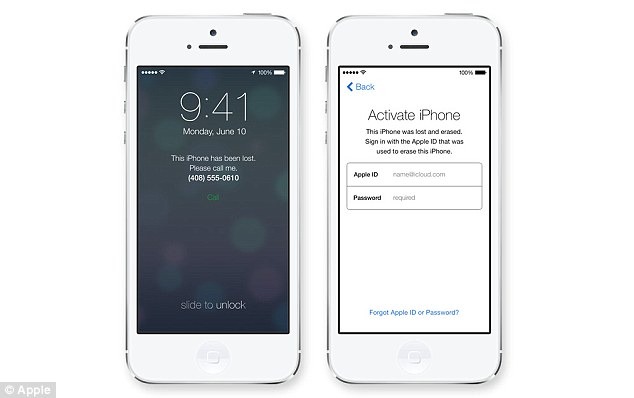
Smartphones with a ‘kill switch’ to prevent from thefts
New software 'kill switch' to thwart thefts:
Microsoft & Google Follows Apple Security Software Which Render handset Unusable after Reported Stolen
Microsoft and google said that phones using their operating systems...
Finally Hackers Dumped Stolen Ashley Madison Data Onto Dark Web
Ashley Madison, the largest cheating website with the tag line " Life is short. Have an affair " was hacked by the group of hackers called itself The Impact Team . And...