TalkTalk Cyber-attack: Another teenager arrested in London
Another teenager arrested in London.
This time the British police arrested a 16 year old boy from Feltham in West London in case of TalkTalk data breach.
On Monday, Metropolitan Police...
Yahoo! Launched its own Web Application Security Scanner
Yahoo! Launched its own Web Application Security Scanner
Gryffin, the web application security scanner by Yahoo! is now open source for the purpose to improve the safety on the web...
ISIS hackers hacked 54,000 twitter accounts: Publishing the secret information of CIA Head
The year has been bad so far for CIA and other US agencies, now this time ISIS hackers hacked 54,000 twitter accounts which also include the accounts of FBI...
Complete Guidance to Install Kali linux in Dual Boot Mode without any Problem
Before start Complete Guidance to Install Kali linux in Dual Boot Mode without any Problem remember it's slogan:-
The Quiter you become ,the more you are able to hear
Do you...
Kali Linux Rolling Edition updated with the latest patches
The most popular Kali Linux was released on 2015 at DefCon 23 in Las Vegas. Kali is successor of Backtrack based on Debian Jessie,distribution, includes many popular penetration...
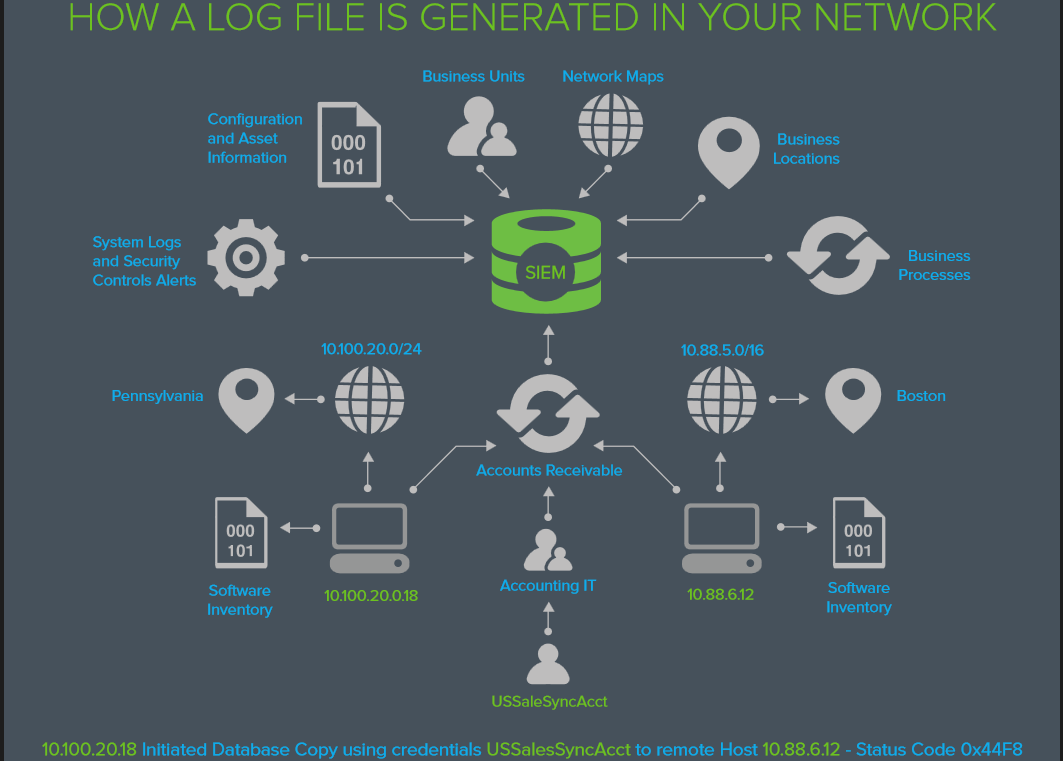
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
What’s in the LOG?
The information you need to answer
Who’s attacking us today? and
How did...
How to hack windows password
How to hack windows password
Change your password if you Forget it
Hello friends today we learn how to change your password if your account or change windows password is locked/you forget your password.At that...
How to make sure a file is safe or threat? | How to do...
Today, we will discuss how to find, a file is safe or a threat for your system?
Or we can say, how to do malware and threat analysis?
Watch Video on...
NETGEAR Router Exploit: Critical Bug in NETGEAR Router
Do you use NETGEAR Router, then have a look at it.
NETGEAR Routers are once again vulnerable to the DNS Monitoring. A security researcher discovered that there is a serious...
IOS 9 Content Blockers: 1Blocker and Blocker
Apple will now support ad blocking. The new operating system iOS9 launching on Wednesday is dignified to change the interaction of users with the web on mobile and iPad....
Three Vulnerabilities Of Starbucks Website: Credit Card details in Risk
The famous coffeehouse Starbucks is undoubtedly the best in its class and taste but registering yourself on the website of Starbucks could be dangerous. The registered accounts and credit...
Managing the Safety and Security of Sensitive Documents
The digital era has made it effortless and more efficient to conduct business than ever before, be it in a local space or on a largely worldwide scale. In...
What is Ransomware and How it works?
Attackers use ransomware to get ransom from its victims. In other words, ransomware is a malicious program or software to block user access on their own system or encrypt...
Is Dropbox safe against Ransomware and Hacks?
Imagine backing up your sensitive data on Dropbox and one fine morning, finding out that your password has been leaked or you are locked out of your account and...
CIA Director’s hacked email: Pak uses militants to counter India’s Influence in Afghanistan
Last week WikiLeaks started publishing the documents from the CIA Director’s hacked email revealing some top secrets. A set of document of released by WikiLeaks says that Pakistan uses...
How to surf internet Anonymously
Hello friends this post is about how to hide your machine IP for surfing internet Anonymously. To read this may bore you but keep patience because it is important....
The Data You Keep In Your Mobile Is Not Secure: Pre-Installed Spywares in Smartphones
If you think that the data you keep in your phone is confidential then you must read this. A report claims that some smartphones are coming with the pre-installed...
How to use backtrack
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Before you start
Before we start playing with safty tools follow the following steps :-
Download btr5...
Developer of most secure messaging app hired by Apple
This time Apple is very sincere about upgrading the security of its iPhone so that no can hack it.Apple also hired one of the key builders of signal to...
What is Sandboxing and How it works?
In this article, we will discuss sandboxing, how it works and list of free sandboxing environments, etc. Hybrid analysis, Malware analysis, and Threat analysis, they all use the same technology...
An Almost Impossible To Detect Phishing Attack Using Punycode
In our previous article How to secure you account from phishing page, we discussed about how to create and detect whether a page is a phishing page or original...
Phishing malware crashes ICICI bank
#Phshing Malware crashes ICICI bank .... https://t.co/a8vTOVvuob
— Buffercode (@buffercoding) February 25, 2016
Official @ICICIBank_Care reply to tweet :
@buffercoding Hi, ICICI Bank has a robust & multi-level security system for all its banking...
Step-by-Step Guide to Install Kali 2.0 Linux in VMware workstation 11
The New Kali 2.0 codename as Kali Sana, is an open-source penetration testing platform having pre-installed hundreds of Hacking ,Reverse Engineering, Forensics and Penetration Testing tools. Kali 2.0 was redesigned...
End-To-End Encryption is now on WHATSAPP
On Tuesday,Whatsapp's founder Jan Koum disclosed that all the messages and call which are done through Whatsapp are fully encrypted.Whatsapp is now lot more secure.
All user those who want...
Shocking: AdBlock has been Sold to an Anonymous Buyer
It might be a bit shocking for you but TRUE!!!
The most popular ad blocking extension Ad block has been sold. And more scandalous news is the buyer of the...
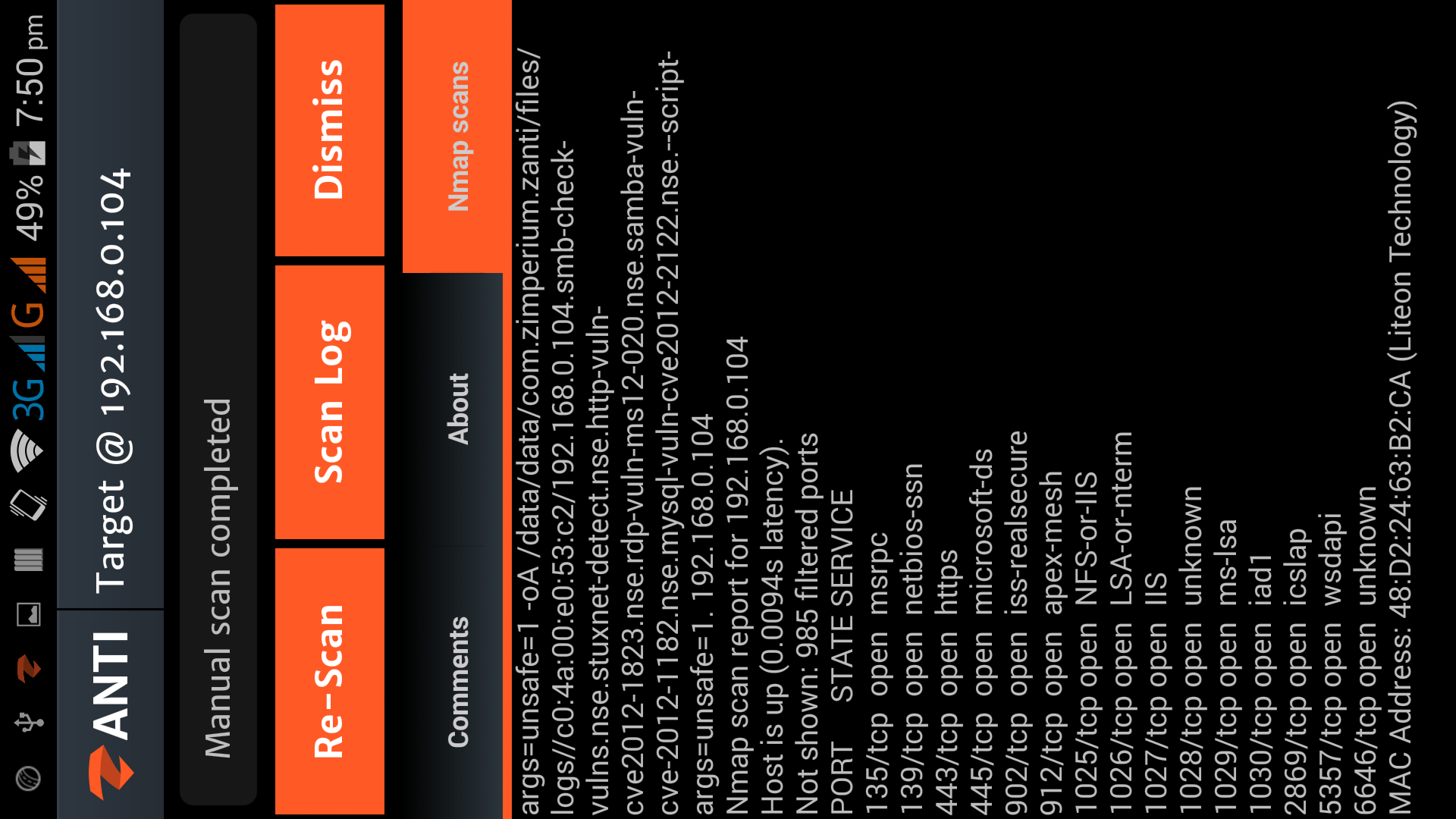
Hacking with Android Smartphone using zANTI2
Download zANTI 2.2(Apk)
Hacking with Android Smartphone using zANTI2
zANTI2 is a Network Analysis and penetration suit developed by ZImperium family as a software developer and researcher, the name zANTI2 comes...