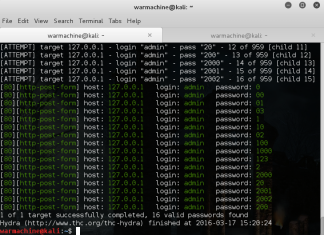
How To Crack Web Form Passwords Using Hydra With Burpsuite In Kali Linux
In our previous article How To Crack Password Using Hydra In Kali Linux , we have discussed about THC Hydra- A tool for Online Password attacks. In this tutorial we will discuss...
Basic Linux Exploits: Moving towards exploits
Note: Hacking is not a joke so please keep patience and learn it step by step.
If you have read all our previous posts , you are ready to exploits the...
How to get into friends whatsapp and send messages
I don't know that how to Express this success !!! Everybody knows that hacking is just a creativity and finding the way to get deeper into the code. So...
Important things to do after installing Kali Linux
There are small set of important softwares that are required after installation of Kali Linux. Linux operating system is not too much user friendly but it is highly flexible...
Exploit using shell code from command line
After reading our previous post:Exploiting buffer overflows using command line it's time to do Exploit Shell code using Command-line but I think you do want to clear your doubt...
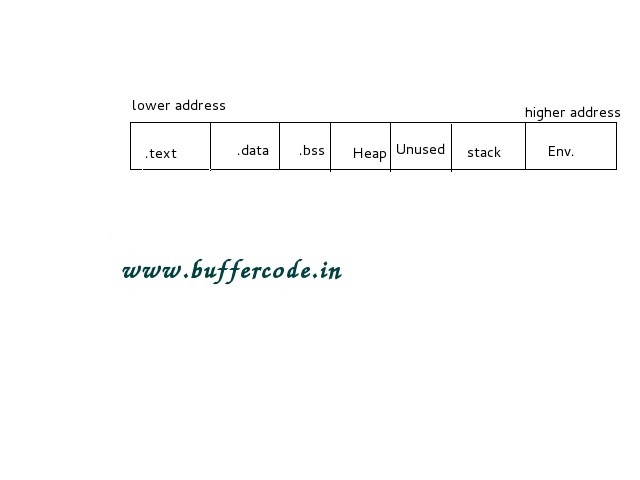
Memory management in C Programming:Computer Memory
Memory management in C is one of the important topic as it's not only about memory management in c but also about Computer Memory Management. In this section you...
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
The most popular Kali Linux was released on last week at DefCon 23 in Las Vegas.Kali is successor of Backtrack...
Basic Linux Exploits:Make your Pc more secure
Basic Linux Exploits:Make your Pc more secure and learn the basics of computer world
Why study Exploits?
Before learning exploits ,one should know about vulnerability.What does it means in the world...
How to Install Honeypot on Kali Linux
In this article we will show how to install Honeypot in Kali Linux. The Pentbox is Security suite that can be use for penetration testing to perform various operations. The...
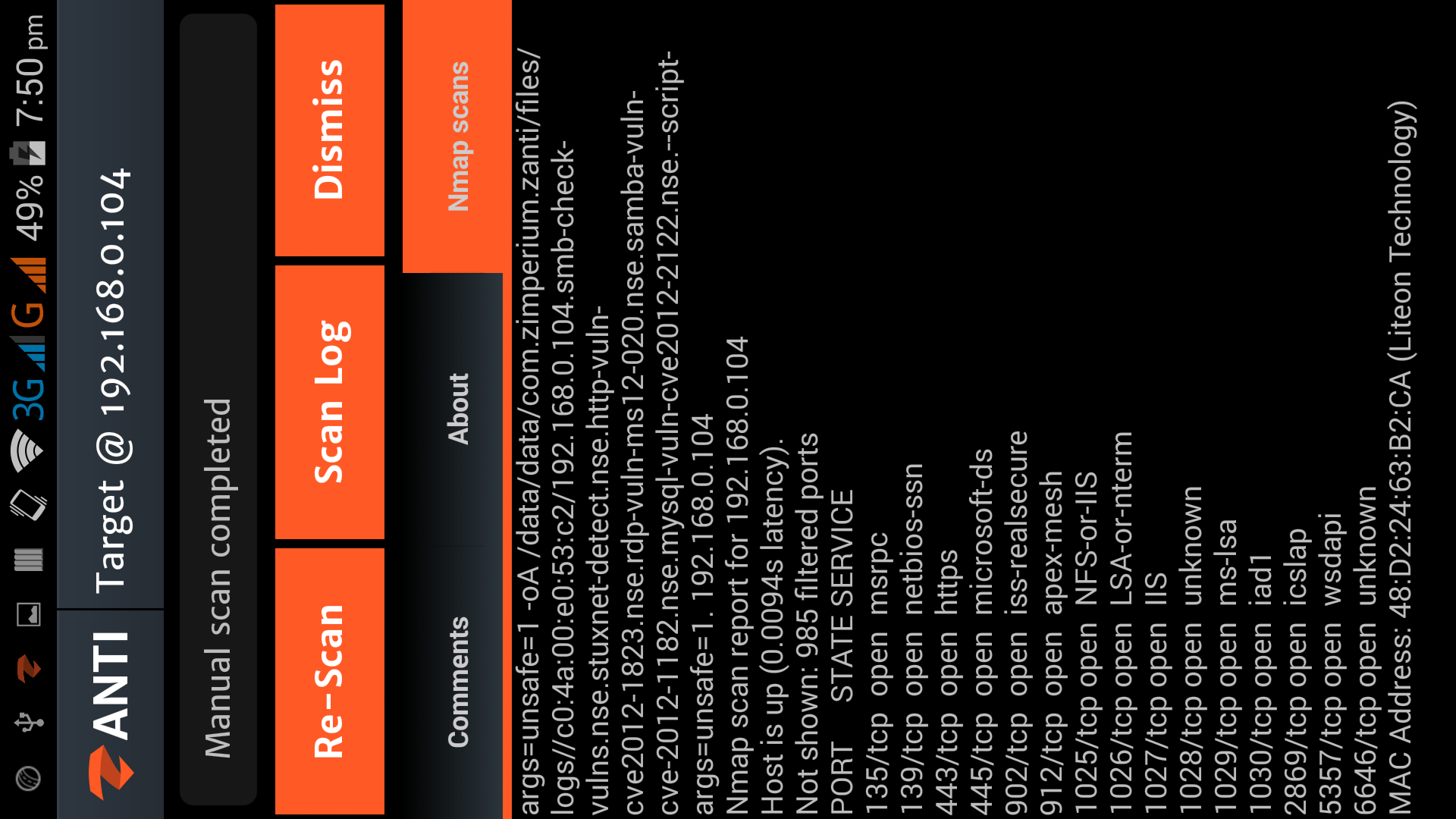
Hacking with Android Smartphone using zANTI2
Download zANTI 2.2(Apk)
Hacking with Android Smartphone using zANTI2
zANTI2 is a Network Analysis and penetration suit developed by ZImperium family as a software developer and researcher, the name zANTI2 comes...
Managing Kali Linux Services
Managing Kali Linux Services
Kali Linux is a specialized Linux distribution aimed to test Network. The default Kali installation comes with several services preinstall like SSH, HTTP, MySQL, etc. These...
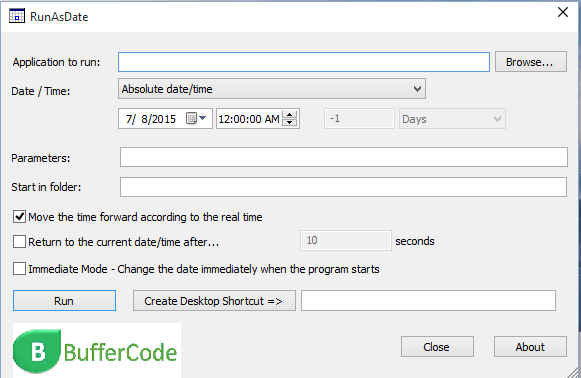
Trick to hack trial version software using RunAsDate utility tool
Here we will discuss a trick about how to hack trial version software in Windows based operating system. It is not exactly hacking of software instead you can call...
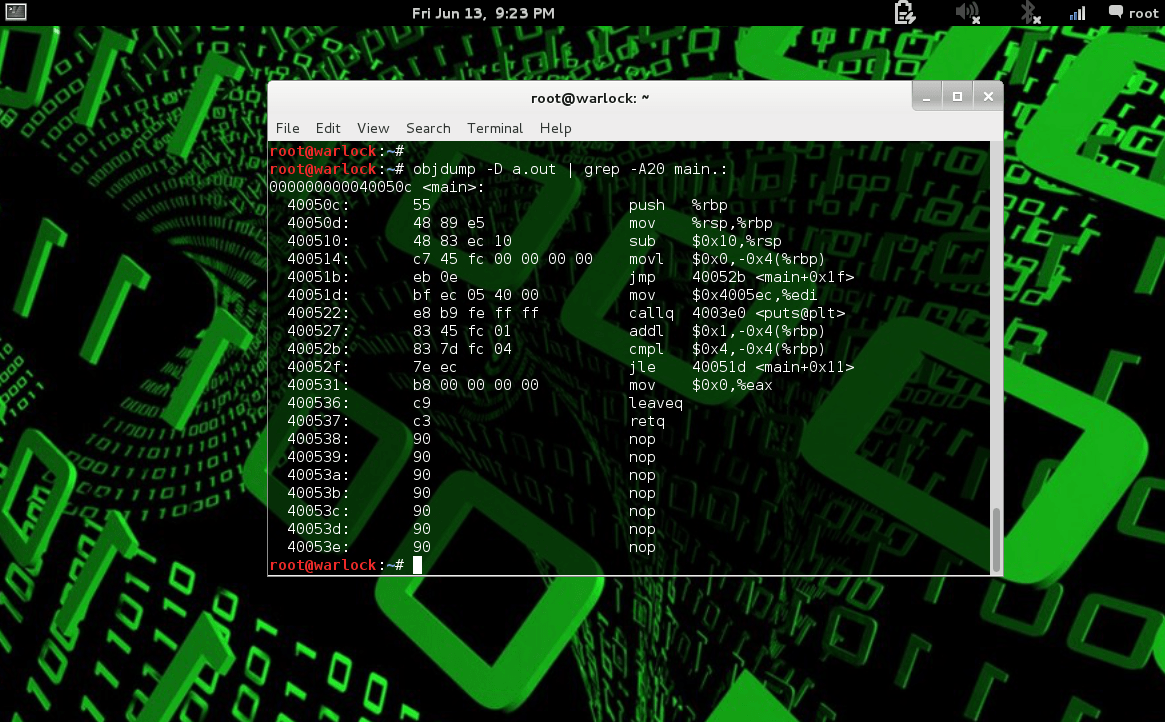
How to use Debugger tool objdump in Linux
Debugger Tool Objdump in Linux
Debugger Tool objdump: C feel more familiar and C compiler exist in every operating system .Basically Linux is a free operating system that every has...
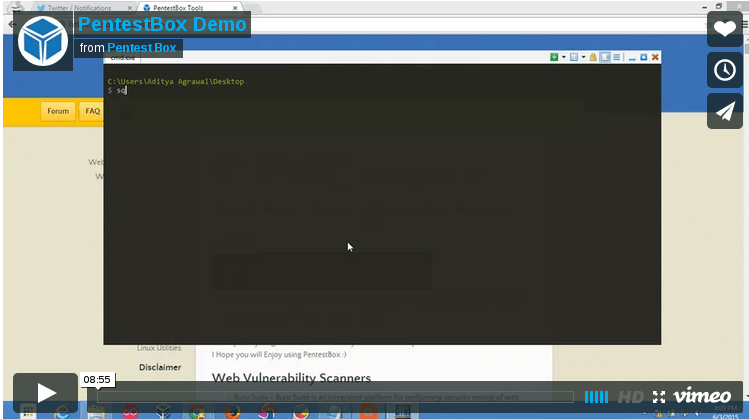
PentestBox: A Portable Penetration Testing Distribution for Windows Environments
Download SourceForge Download Torrent
PentestBox is a...
Basic Exploits : Stack Operations
Note: Hacking is not a joke so please keep patience and learn it step by step.
Stack Operations
First and the most important topic to learn the basics of Exploits is...
How to secure your account from phishing attacks on Internet
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Creating Phishing page to know the safety cautions
on Internet
To know the cautions we must know...
Introduction to Log Collector and Event Sources | SIEM
In this article, we will discuss how we use a log collector to collect and analyze logs. While in the previous article we have discussed Logs. We already have...
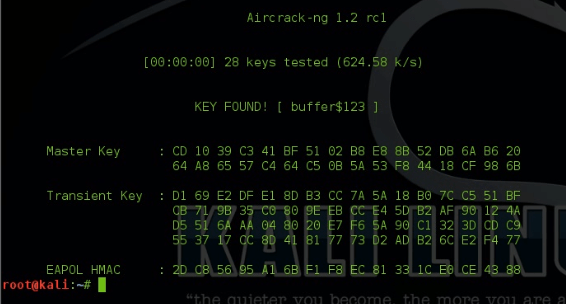
Hack WPA2 Encrypted Wi-Fi Networks using Aircrack-ng
Hack WPA2 Encrypted Wi-Fi Networks using Aircrack-ng | Kali-Linux
Hello friend ,In this article I will demonstrate how to crack or hack some one's WiFi Network just in simple steps...
Step-by-Step Guide to Install Kali 2.0 Linux in VMware workstation 11
The New Kali 2.0 codename as Kali Sana, is an open-source penetration testing platform having pre-installed hundreds of Hacking ,Reverse Engineering, Forensics and Penetration Testing tools. Kali 2.0 was redesigned...
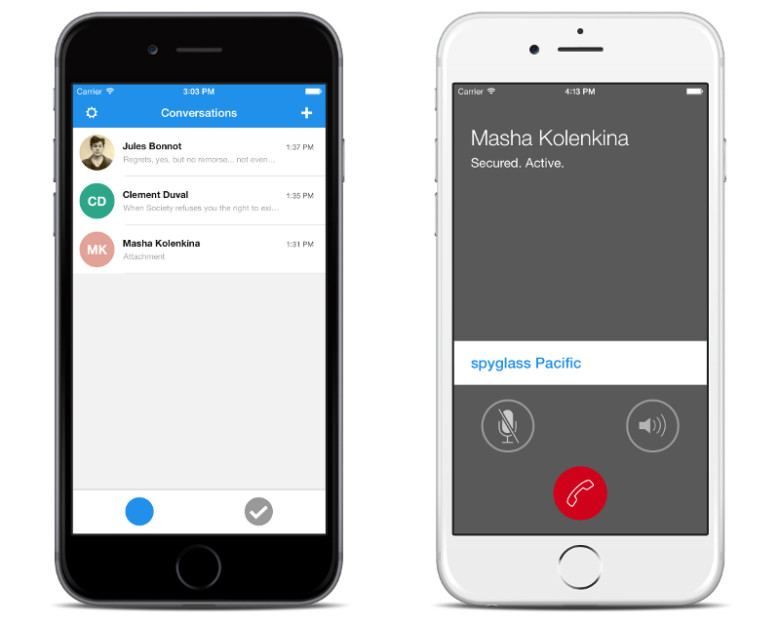
Developer of most secure messaging app hired by Apple
This time Apple is very sincere about upgrading the security of its iPhone so that no can hack it.Apple also hired one of the key builders of signal to...
How to make sure a file is safe or threat? | How to do...
Today, we will discuss how to find, a file is safe or a threat for your system?
Or we can say, how to do malware and threat analysis?
Watch Video on...
End-To-End Encryption is now on WHATSAPP
On Tuesday,Whatsapp's founder Jan Koum disclosed that all the messages and call which are done through Whatsapp are fully encrypted.Whatsapp is now lot more secure.
All user those who want...
Explore and Search Exploit in Metasploit
Metasploit having a big name, when we talking about security. Metasploit was written in Perl as a portable network tool, In 2007 the Metasploit Freamwork has completely rewritten in...
Stone tether smallest tracking device finds your lost items
Stone tether smallest tracking device:
Technology has made life easier if you fail to remember something. A new device is becoming to discover your lost items. Its name is stone...
Recently Whatsapp Banned users for using Whatsapp Plus Application
OOOOhh cut off with friends due to using watsapp plus :(
i missed my friends , my watsapp plus stop working :`(
...
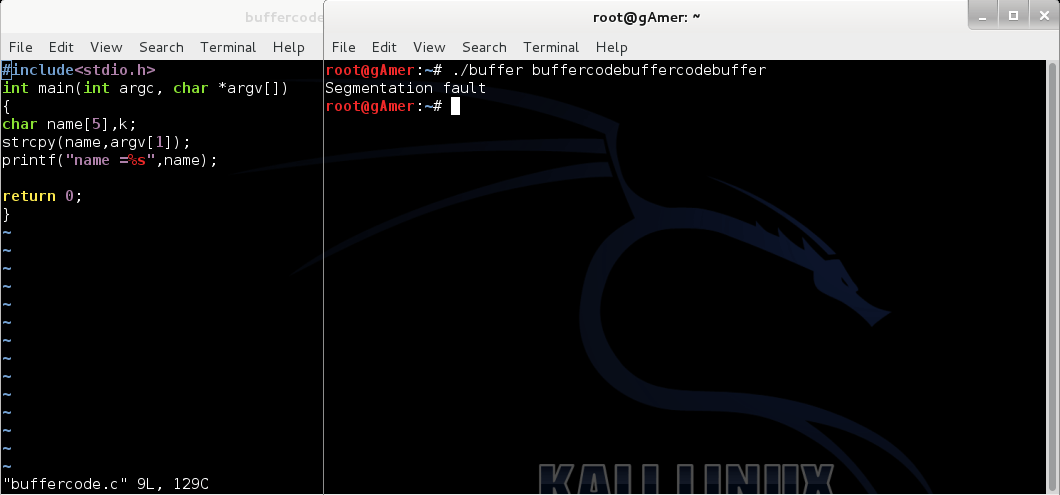
Exploiting buffer overflows using command line
After reading our previous post: Next step moving towards exploit:Finding the return address ,it's time to do some command line exploits. So this post is regarding Exploiting buffer...