Loki Got an upgrade – Loki Botnet new varient Detected
Loki Botnet (Malware) works in the same way as Marvel's Villen cum hero works (Trick the user and steal the information). Loki botnet, A bot (malware) which was detected...
How To Crack Password Using Hydra In Kali Linux
Weak password is still a big problem in the world of security. User need to set a strong password to restrict the access of data from anonymous user. Even a...
Managing Kali Linux Services
Managing Kali Linux Services
Kali Linux is a specialized Linux distribution aimed to test Network. The default Kali installation comes with several services preinstall like SSH, HTTP, MySQL, etc. These...
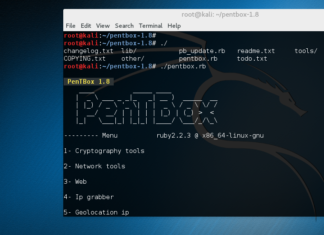
How to Install Honeypot on Kali Linux
In this article we will show how to install Honeypot in Kali Linux. The Pentbox is Security suite that can be use for penetration testing to perform various operations. The...
What is Sandboxing and How it works?
In this article, we will discuss sandboxing, how it works and list of free sandboxing environments, etc. Hybrid analysis, Malware analysis, and Threat analysis, they all use the same technology...
Basic Linux Exploits:Make your Pc more secure
Basic Linux Exploits:Make your Pc more secure and learn the basics of computer world
Why study Exploits?
Before learning exploits ,one should know about vulnerability.What does it means in the world...
Demonbot is on rising | A New Botnet
As security is getting stronger so hackers are getting more stronger. Once a loophole is closed by Operating systems or any vendors then hackers find out another way to breach...
Recently Whatsapp Banned users for using Whatsapp Plus Application
OOOOhh cut off with friends due to using watsapp plus :(
i missed my friends , my watsapp plus stop working :`(
...
Explore and Search Exploit in Metasploit
Metasploit having a big name, when we talking about security. Metasploit was written in Perl as a portable network tool, In 2007 the Metasploit Freamwork has completely rewritten in...
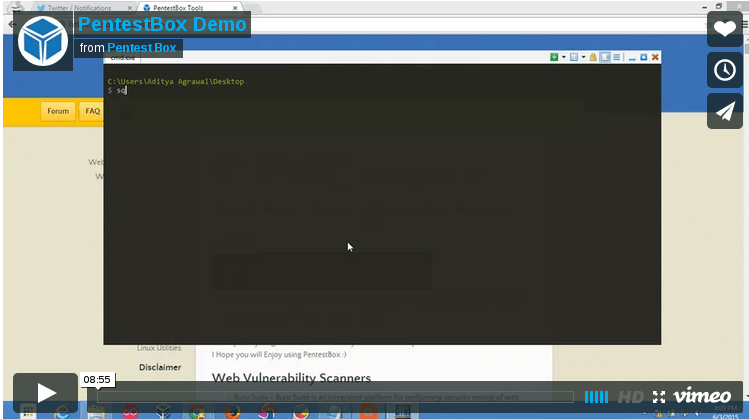
PentestBox: A Portable Penetration Testing Distribution for Windows Environments
Download SourceForge Download Torrent
PentestBox is a...
How to secure your account from phishing attacks on Internet
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Creating Phishing page to know the safety cautions
on Internet
To know the cautions we must know...
End-To-End Encryption is now on WHATSAPP
On Tuesday,Whatsapp's founder Jan Koum disclosed that all the messages and call which are done through Whatsapp are fully encrypted.Whatsapp is now lot more secure.
All user those who want...
Important things to do after installing Kali Linux
There are small set of important softwares that are required after installation of Kali Linux. Linux operating system is not too much user friendly but it is highly flexible...
Explore into the Metasploit ( a Ultimate Hackers Tool)
Metasploit is a complete and a Ultimate Security tool that provides information about Computer Security Vulnerabilities and also use in penetration testing .It was develop by HD Moore in...
CIA Director’s hacked email: Pak uses militants to counter India’s Influence in Afghanistan
Last week WikiLeaks started publishing the documents from the CIA Director’s hacked email revealing some top secrets. A set of document of released by WikiLeaks says that Pakistan uses...
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
The most popular Kali Linux was released on last week at DefCon 23 in Las Vegas.Kali is successor of Backtrack...
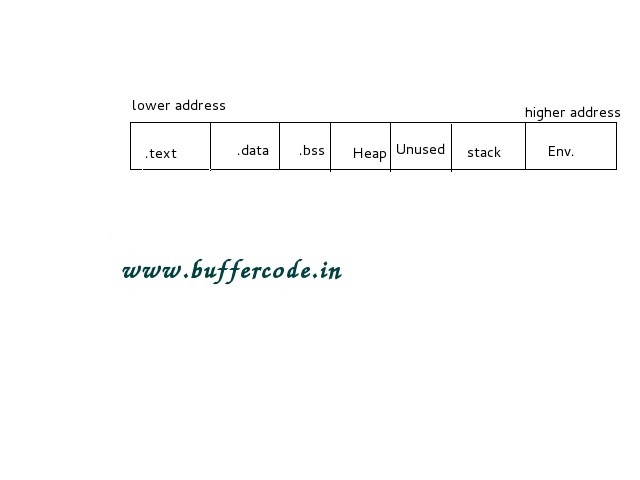
Memory management in C Programming:Computer Memory
Memory management in C is one of the important topic as it's not only about memory management in c but also about Computer Memory Management. In this section you...
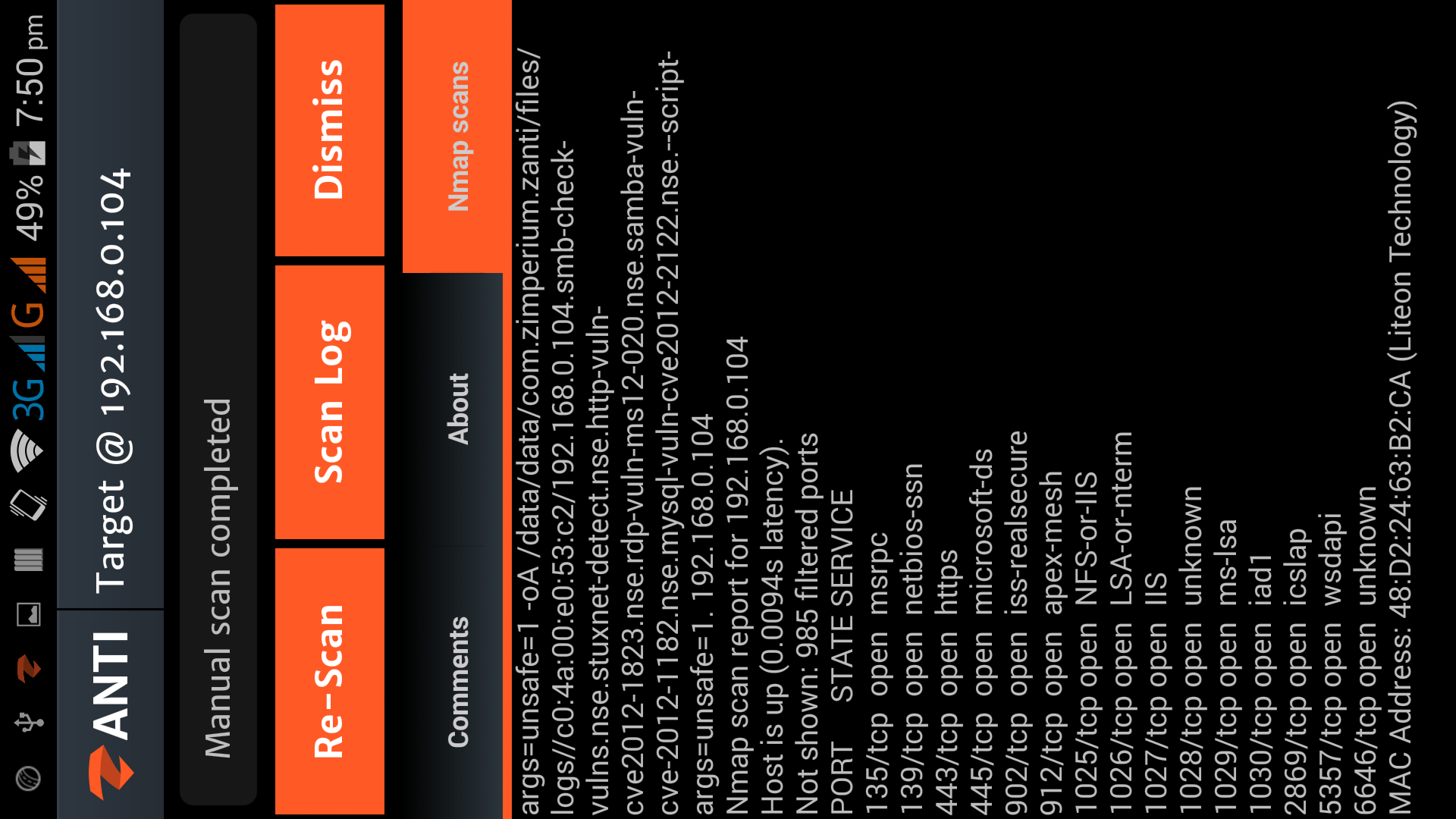
Hacking with Android Smartphone using zANTI2
Download zANTI 2.2(Apk)
Hacking with Android Smartphone using zANTI2
zANTI2 is a Network Analysis and penetration suit developed by ZImperium family as a software developer and researcher, the name zANTI2 comes...
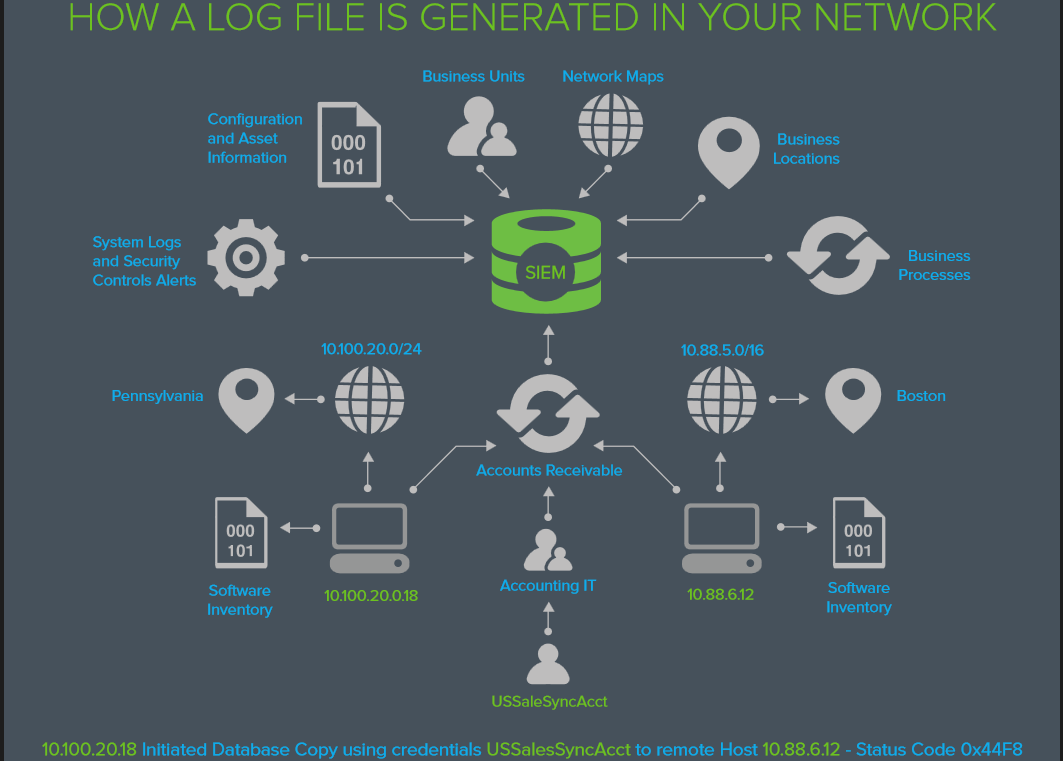
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
What’s in the LOG?
The information you need to answer
Who’s attacking us today? and
How did...
How to use backtrack
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Before you start
Before we start playing with safty tools follow the following steps :-
Download btr5...
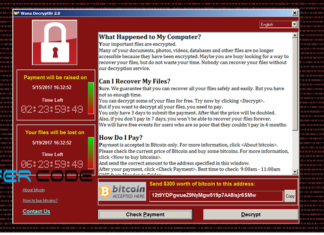
WannaCry ransomware attack: Largest Ransomware Attack In The History
By now, we are sure that you have heard something about wannacry ransomware. There may be a lot of questions in your mind such as What is wannacry ?...
Shocking secrets about Ashley Madison: Women were actually not using the website
The hacked data of Ashley Madison website is been a reason for many criminal activities since it’s data is dumped on to the dark web (also known as deep...
Exploit Development Process:Moving towards Real world Hacking
Now that we have covered basics of exploit , you are ready to look at real world examples like metasploit . As you all know - vulnerabilities in real...
WordPress XML-RPC: Brute Force Amplification Attack
It is always interesting to hear about the bugs in world’s most famous systems, this time it is WordPress. Yes the world’s most famous content management system is vulnerable...
Finally Hackers Dumped Stolen Ashley Madison Data Onto Dark Web
Ashley Madison, the largest cheating website with the tag line " Life is short. Have an affair " was hacked by the group of hackers called itself The Impact Team . And...
What is Ransomware and How it works?
Attackers use ransomware to get ransom from its victims. In other words, ransomware is a malicious program or software to block user access on their own system or encrypt...