Stone tether smallest tracking device finds your lost items
Stone tether smallest tracking device:
Technology has made life easier if you fail to remember something. A new device is becoming to discover your lost items. Its name is stone...
Now use Facebook anonymously via Tor networks: good news for Tor users
Now use Facebook anonymously:
Facebook is a most popular social network in world. Here is good news for Facebook lovers, who want to keep secret their identity on internet. Identity...
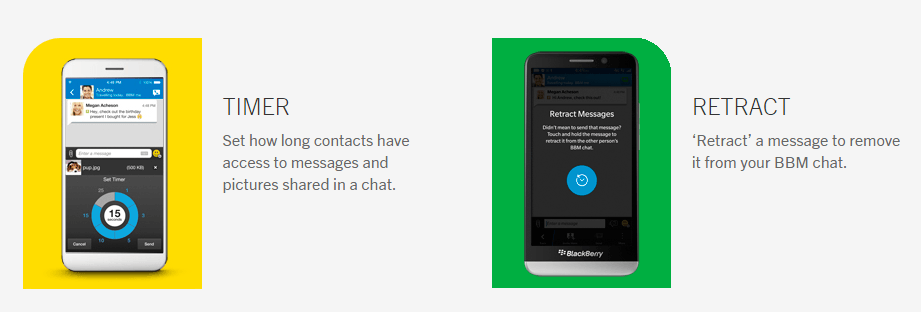
BBM BlackBerry now features timer just like Snapchat
Here is a good news for all BBM ( BlackBerry Messenger) Lovers, new Privacy features update which is live by BBM BlackBerry Application for all Android, ios or windows device....
Learn hacking for free on buffercode
Start from 15/Nov/2014 see here Basics Linux exploits
To learn hacking is art , and to do hacking is also an art . Similarly friends to teach hacking is an...
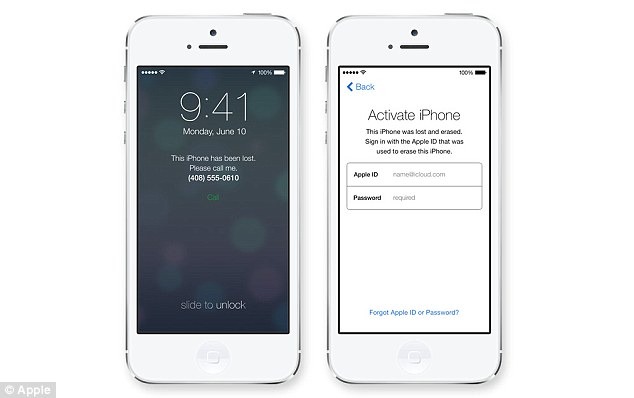
Smartphones with a ‘kill switch’ to prevent from thefts
New software 'kill switch' to thwart thefts:
Microsoft & Google Follows Apple Security Software Which Render handset Unusable after Reported Stolen
Microsoft and google said that phones using their operating systems...
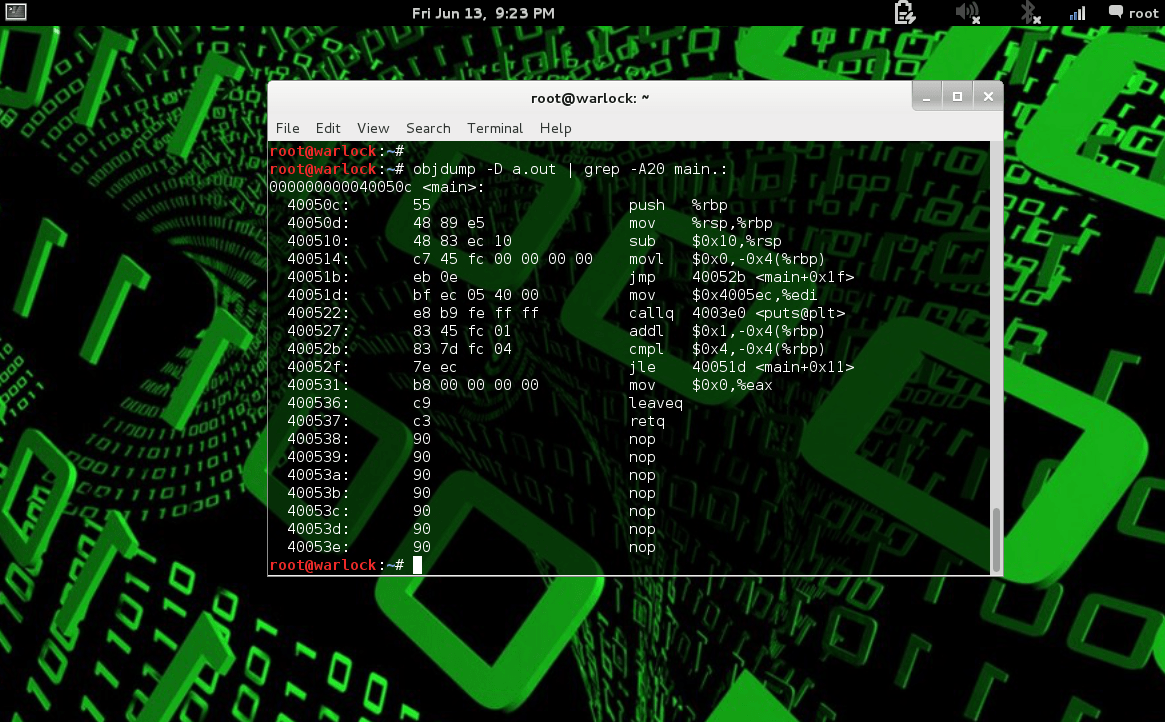
How to use Debugger tool objdump in Linux
Debugger Tool Objdump in Linux
Debugger Tool objdump: C feel more familiar and C compiler exist in every operating system .Basically Linux is a free operating system that every has...
Top Penetration Testing Application for Android Mobiles
Android is a Linux based small operating which runs on mobile. Most of the user in the world are using Android because of its large application in play or...
How to surf web anonymously ??
Continue with our previous post How to surf web anonymously ......
Today i am going to tell you one of the best solution to surf web anonymously...
In my personal point...
How to send encrypted message using softwares or applications??
How to Send Encrypted Message??
In our previous post Encryption and Decryption ,we told you the meaning and need of encryption and decryption. After that you may want to know...
What is Encryption and Decryption , and how it make our message anonymous??
Friends in our previous post How to surf internet Anonymously we tell you why to surf internet anonymously and number of ways to do that. Our aim is to make...
How to surf internet Anonymously
Hello friends this post is about how to hide your machine IP for surfing internet Anonymously. To read this may bore you but keep patience because it is important....
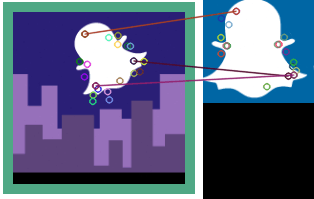
Snapchat’s Security break by Steven Hickson
It's all about little bit of simple programming and computer graphics . Snapchat's Security broke by Steven Hickson a programmer as well as a hacker or you can say that every...
How to use backtrack
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Before you start
Before we start playing with safty tools follow the following steps :-
Download btr5...
How to hack windows password
How to hack windows password
Change your password if you Forget it
Hello friends today we learn how to change your password if your account or change windows password is locked/you forget your password.At that...