Now BackUp Your WhatsApp Data to Google Drive
BackUp Your WhatsApp Data
The first thing comes to my mind when I think about losing my phone is “Oh! No I will lose all my data all the conversation”...
British Intelligence Agency can hack any Smartphone.
Yes it is true, British Intelligence agency has the power to hack any Smartphone in the World. This fact was disclosed by former NSA contractor Edward Snowden, he told...
Hackers Attacked Microsoft Outlook Web App to steal Login Credentials
Hackers Attacked Microsoft Outlook Web App to steal Login Credentials
Researchers have recently founded a hazardous Backdoor in Microsoft’s Outlook Web Application, which allows the hackers to steal e-mail and...
StageFright 2.0 Fixed: Google released an OTA for Nexus Devices.
StageFright 2.0 Fixed
Few days back, the researchers warned google of the new Stage Fright Bug. This bug affected more than a billion devices that are running on Android OS.
This...
iOS Malware – YiSpecter
iOS Malware- YiSpecter
Cybersecurity firm Palo Alto has recently discovered a new Malware in Apple named YiSpecter .I don't know what's wrong is going on with Apple as this is...
Shocking: AdBlock has been Sold to an Anonymous Buyer
It might be a bit shocking for you but TRUE!!!
The most popular ad blocking extension Ad block has been sold. And more scandalous news is the buyer of the...
Stage fright Bug 2.0: All Android Devices are Vulnerable to the Bugs
Once again the Stage fright vulnerability is back, two new Android Stage fright vulnerabilities are recently disclosed.
This time with some new tricks, an attacker can hack the Android Phone...
IOS 9.0.2 fixes the Lock screen ByPass Bug
IOS 9.0.2 fixes the Lock screen Bypass Bug
After the launch of its latest version of iOS, Apple has rolled out two minor updates for its operating system (iOS9.0.1 and...
Yahoo! Launched its own Web Application Security Scanner
Yahoo! Launched its own Web Application Security Scanner
Gryffin, the web application security scanner by Yahoo! is now open source for the purpose to improve the safety on the web...
SQL INJECTION BY VARIOUS WAYS
SQL INJECTION BY VARIOUS WAYS INTRODUCTION TO SQL INJECTION
The most easiest way to hack an site is hacking it by SQL injection. SQL Injection based on the vulnerabilities of an...
AVG will behave as Virus : AVG’s New Privacy Policy, Your data will be...
What is the first thing you do while setting up your computer?
Is it installing the free antivirus or Internet security software? I guess yes, this is the first thing...
Three Vulnerabilities Of Starbucks Website: Credit Card details in Risk
The famous coffeehouse Starbucks is undoubtedly the best in its class and taste but registering yourself on the website of Starbucks could be dangerous. The registered accounts and credit...
IOS 9 Content Blockers: 1Blocker and Blocker
Apple will now support ad blocking. The new operating system iOS9 launching on Wednesday is dignified to change the interaction of users with the web on mobile and iPad....
Security Flaw found in WhatsApp : 200 million users are at Risk
Security Flaw found in WhatsApp: 200 million users are at Risk
You will be shocked to know that about 200 million users of the world’s most famous instant messaging service...
The Data You Keep In Your Mobile Is Not Secure: Pre-Installed Spywares in Smartphones
If you think that the data you keep in your phone is confidential then you must read this. A report claims that some smartphones are coming with the pre-installed...
Shocking secrets about Ashley Madison: Women were actually not using the website
The hacked data of Ashley Madison website is been a reason for many criminal activities since it’s data is dumped on to the dark web (also known as deep...
$ 500,000 Reward For Impact Team Information :Ashley Madison Hack Has Become A Reason...
In our previous article Finally Hackers Dumped Stolen Ashley Madison Data Onto Dark Web we told you why the group of hackers dumped Ashley Madison's Data on dark web which includes...
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
Dual Boot Kali 2.0 and Microsoft Windows 8, 8.1, 10
The most popular Kali Linux was released on last week at DefCon 23 in Las Vegas.Kali is successor of Backtrack...
Finally Hackers Dumped Stolen Ashley Madison Data Onto Dark Web
Ashley Madison, the largest cheating website with the tag line " Life is short. Have an affair " was hacked by the group of hackers called itself The Impact Team . And...
Microsoft’s Windows 10 disables pirated games and illegal hardware
Every one is exited to get free Windows 10 upgrade because of its features , compatibility , user interface and other good features, without knowing why they make it...
Step-by-Step Guide to Install Kali 2.0 Linux in VMware workstation 11
The New Kali 2.0 codename as Kali Sana, is an open-source penetration testing platform having pre-installed hundreds of Hacking ,Reverse Engineering, Forensics and Penetration Testing tools. Kali 2.0 was redesigned...
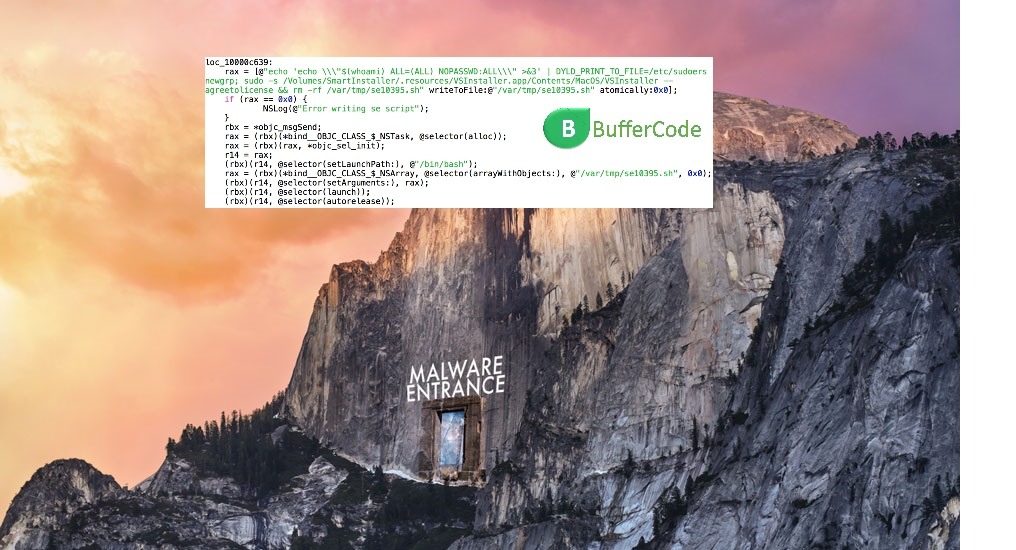
OSX Sudoers Flaw : The Script Uses Sudo’s New Password-Free Behavior
This year, in the month of January , three Apple OSx zero day flaws were revealed by Google .First vulnerability was - OS X Yosemite had flaw to pass arbitrary...
“The Pirate Bay Four” Acquitted In Criminal Copyright Case
The Founders of Pirate Bay - Gottfrid Svartholm, Fredrik Neij, Peter Sunde and Carl Lundström were acquitted (Free from charge) by a Belgian court Thursday of charges alleging criminal copyright infringement and...
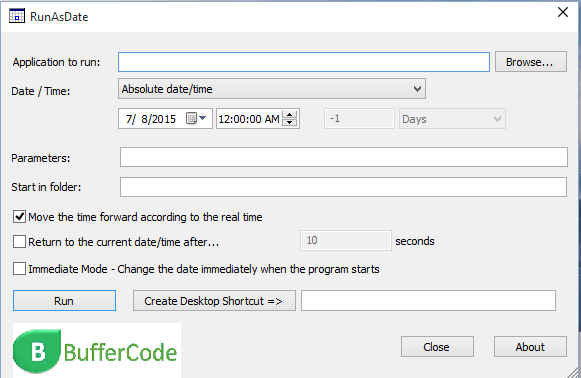
Trick to hack trial version software using RunAsDate utility tool
Here we will discuss a trick about how to hack trial version software in Windows based operating system. It is not exactly hacking of software instead you can call...
ProxyHam : Anonymously Access Wi-Fi from 2.5-Miles Away
Here we will discuss How to Anonymously Access Wi-Fi from 2.5 miles away using Dubbed Proxyham. It's always the matter of discuss when anonymity is in the frame. In...
Managing Kali Linux Services
Managing Kali Linux Services
Kali Linux is a specialized Linux distribution aimed to test Network. The default Kali installation comes with several services preinstall like SSH, HTTP, MySQL, etc. These...