A new Zero-Day vulnerability in recently patched Flash Player
It seems to be no benefits of fixing the issues in its latest patch that was released by Flash Player yesterday.
Adobe is trying its best to make the Flash...
How to surf internet Anonymously
Hello friends this post is about how to hide your machine IP for surfing internet Anonymously. To read this may bore you but keep patience because it is important....
What is Ransomware and How it works?
Attackers use ransomware to get ransom from its victims. In other words, ransomware is a malicious program or software to block user access on their own system or encrypt...
Attackers are using facebook messenger to spread Locky Ransomware
Any Facebook message with an image file (.svg format) send by your friend can be a Locky Ransomware file, so just avoid clicking it.
What is Locky Ransomware?
Locky is ransomware released...
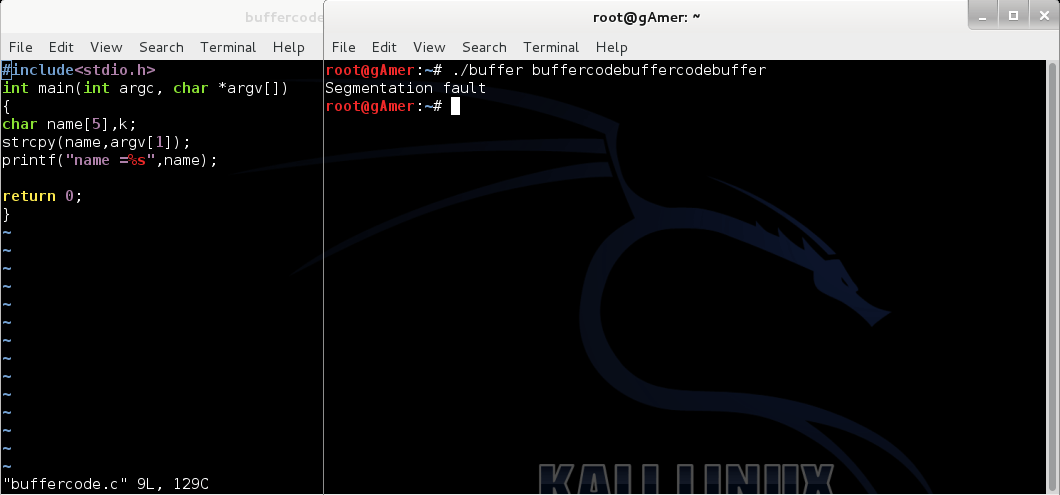
Basic Linux Exploits: Moving towards exploits
Note: Hacking is not a joke so please keep patience and learn it step by step.
If you have read all our previous posts , you are ready to exploits the...
China Helped U.S.A: China Arrested Hackers on the Request of U.S Government.
China Arrested Hackers on the Request of U.S Government
The things happen in movies can actually happen in the real life too. The recent action of China reminds me of...
Obama Encryption Policy: Are they violating the definitions of Security, Privacy and Encryption?
Obama Encryption Policy
As the consequences of exposure that Edward Snowden made about NSA, the citizens of USA are now demanding for more transparent security.
From last some days citizens of...
The Data You Keep In Your Mobile Is Not Secure: Pre-Installed Spywares in Smartphones
If you think that the data you keep in your phone is confidential then you must read this. A report claims that some smartphones are coming with the pre-installed...
Bitport Review : Download torrents to your cloud and play them online
Bitport.io review :Most of the people here use torrent to download movies, games , series , software and much more. But there is a question is it safe to...
Android Banking Trojan Hiding In Apps Under Different Names: Targeting over 420 apps worldwide
Beware if you recently have installed any funny video application from Google Play Store as it may contain android banking Trojan.
Most of the people love to watch funny videos...
ISIS Hacker Arrested In Malaysia: US Military Data Hacked By ISIS Hacker
A Kosovo citizen is arrested by Malaysian Authorities in the charges of computer hacking and providing the personal data of U.S. Military members to the Islamic State terrorist group...
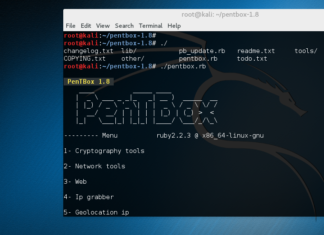
How to Install Honeypot on Kali Linux
In this article we will show how to install Honeypot in Kali Linux. The Pentbox is Security suite that can be use for penetration testing to perform various operations. The...
$ 500,000 Reward For Impact Team Information :Ashley Madison Hack Has Become A Reason...
In our previous article Finally Hackers Dumped Stolen Ashley Madison Data Onto Dark Web we told you why the group of hackers dumped Ashley Madison's Data on dark web which includes...
WikiLeaks to publish the content from CIA’s Director Email
You must have visited the website of WikiLeaks, the non-profit and transparency organisation to read about the leaks and top secrets of this world.
And now Julian Assange, the founder...
Hackers Attacked Microsoft Outlook Web App to steal Login Credentials
Hackers Attacked Microsoft Outlook Web App to steal Login Credentials
Researchers have recently founded a hazardous Backdoor in Microsoft’s Outlook Web Application, which allows the hackers to steal e-mail and...
Security Flaw found in WhatsApp : 200 million users are at Risk
Security Flaw found in WhatsApp: 200 million users are at Risk
You will be shocked to know that about 200 million users of the world’s most famous instant messaging service...
Mozilla Placing High Bandwidth Tor Middle Relays
Mozilla Placing High Bandwidth Tor Middle Relays
Mozilla Placing High Bandwidth Tor Middle Relays to add more secure anonymity in Firefox. Tor and Mozilla working together to provide a more...
Three Vulnerabilities Of Starbucks Website: Credit Card details in Risk
The famous coffeehouse Starbucks is undoubtedly the best in its class and taste but registering yourself on the website of Starbucks could be dangerous. The registered accounts and credit...
How to use backtrack
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Before you start
Before we start playing with safty tools follow the following steps :-
Download btr5...
The Trojanized Adware: It can automatically install apps to your Android Device
What sort of apps do you install on your Android Smartphone?
I hope the trusted ones. Now, what if someone installs a malicious app on your smartphone without your permission?
It...
Radio Wave Hack: It allows the hacker to control your phone from 16 feet...
Every day we get to know about a different hack and every hack has its own dependencies and capabilities.
Now, this is crazy. Security researchers have discovered a new hack...
Next step towards exploit : finding the return address
Hey friends , I think it's the time to take next step towards exploit after reading our all previous posts . In this tutorial you will learn about :...
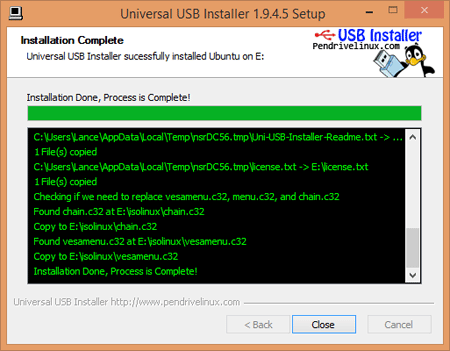
Complete Guidance to Install Kali linux in Dual Boot Mode without any Problem
Before start Complete Guidance to Install Kali linux in Dual Boot Mode without any Problem remember it's slogan:-
The Quiter you become ,the more you are able to hear
Do you...
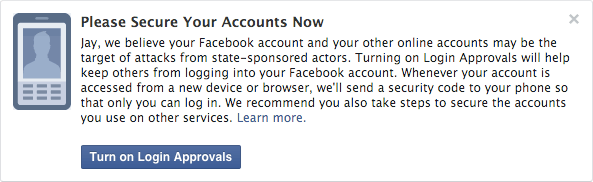
Facebook’s New Notification Feature: Facebook will now Notify you if Government is Spying on...
Yet another feature by Facebook to make the world’s largest social network more secure. Facebook has just launched a new Notification feature that will alert you if it believes...
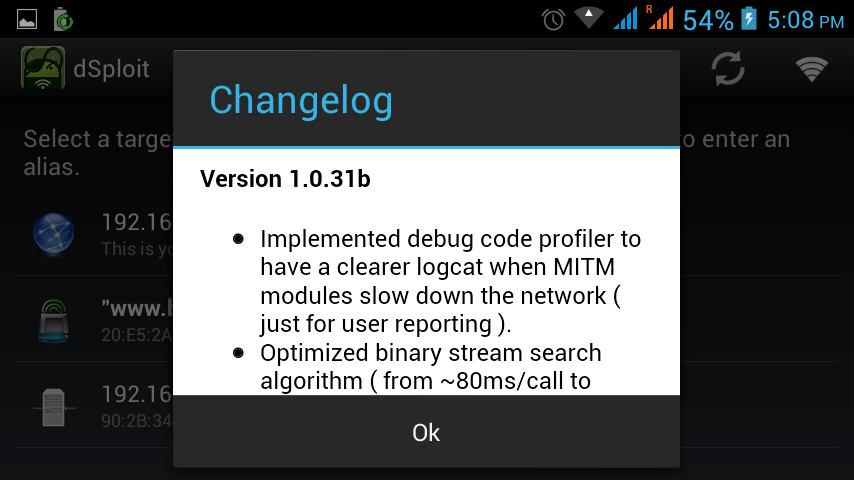
Top Penetration Testing Application for Android Mobiles
Android is a Linux based small operating which runs on mobile. Most of the user in the world are using Android because of its large application in play or...
What is Sandboxing and How it works?
In this article, we will discuss sandboxing, how it works and list of free sandboxing environments, etc. Hybrid analysis, Malware analysis, and Threat analysis, they all use the same technology...