Kali Linux Rolling Edition updated with the latest patches
The most popular Kali Linux was released on 2015 at DefCon 23 in Las Vegas. Kali is successor of Backtrack based on Debian Jessie,distribution, includes many popular penetration...
VDI Deployment Mistakes
Firstly, we should know about VDI. It stands for Virtual Desktop Infrastructure. It is a practice which hosts desktop operating system within a Virtual Machine (VM) running on a...
US Intelligence Chief Hacked by a teen
The email of US Intelligence Chief Hacked!
The same teenager who hacked the AOL email of CIA Director John Brennan back in October last year has now hacked into personal...
PlayStation Hacked! Hackers managed to run Linux on PS4 gaming Console
PlayStation Hacked!
This might be the craziest thing done in the world of gaming, when some hackers hacked Sony’s PlayStation gaming console to run Linux.
This console hacking goes by the...
Instagram Hacked: A security researcher hacked into the servers of Instagram
Instagram Hacked!
Someone just hacked into the servers of Instagram, showing the most secure mechanisms also have bugs.
But you don’t try to do anything like this because even reporting the...
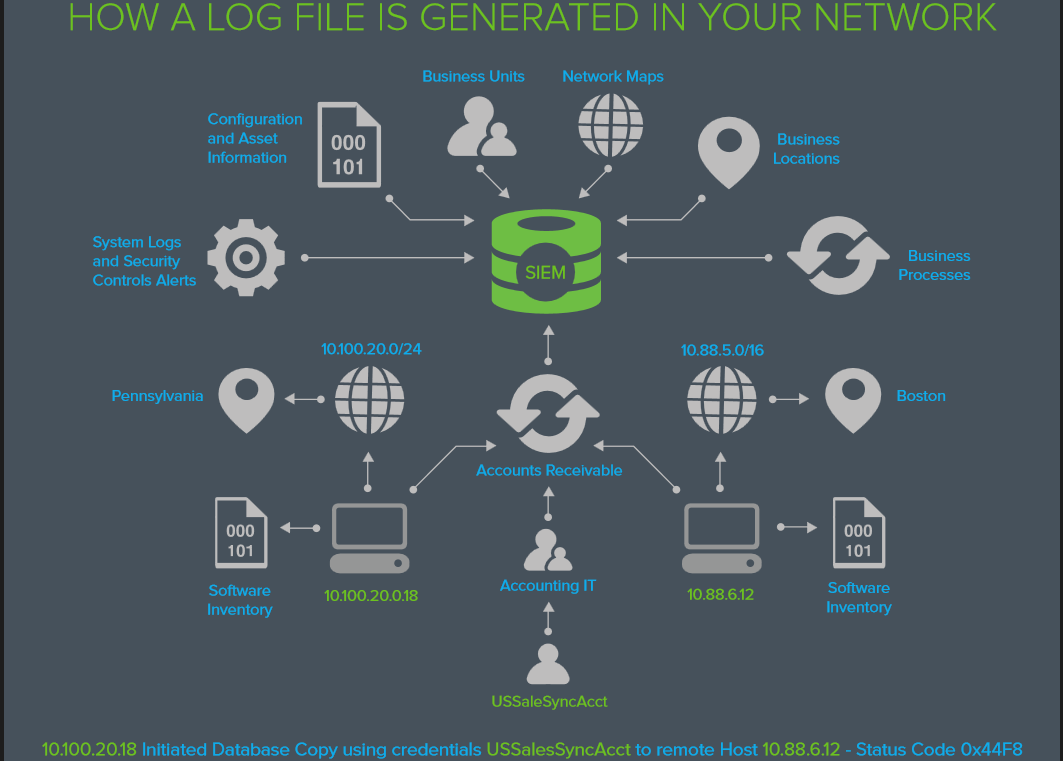
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
EVERYTHING YOU WANTED TO KNOW ABOUT LOG MANAGEMENT BUT WERE AFRAID TO ASK
What’s in the LOG?
The information you need to answer
Who’s attacking us today? and
How did...
The Trojanized Adware: It can automatically install apps to your Android Device
What sort of apps do you install on your Android Smartphone?
I hope the trusted ones. Now, what if someone installs a malicious app on your smartphone without your permission?
It...
ISIS hackers hacked 54,000 twitter accounts: Publishing the secret information of CIA Head
The year has been bad so far for CIA and other US agencies, now this time ISIS hackers hacked 54,000 twitter accounts which also include the accounts of FBI...
Baidu SDK Bug: Puts over 100 Million devices at risk
Researchers recently found that Baidu’s software development kit (SDK) is vulnerable to a bug that can allow the hacker to gain the backdoor like access to a user’s device....
TalkTalk Cyber-attack: Another teenager arrested in London
Another teenager arrested in London.
This time the British police arrested a 16 year old boy from Feltham in West London in case of TalkTalk data breach.
On Monday, Metropolitan Police...
18,000 malicious apps are stealing the text messages from your android device
Knowing that there are number of Android apps that are stealing the copies of the text messages received or sent to your device may leave you a bit insecure,...
15 Year old Boy Arrested as the suspect of TalkTalk cyber Attack
After the data breach of largest phone and broadband provider in UK, police for the first time has taken some action.
Last week TalkTalk the biggest Phone and Broadband provider...
CIA Director’s hacked email: Pak uses militants to counter India’s Influence in Afghanistan
Last week WikiLeaks started publishing the documents from the CIA Director’s hacked email revealing some top secrets. A set of document of released by WikiLeaks says that Pakistan uses...
WikiLeaks to publish the content from CIA’s Director Email
You must have visited the website of WikiLeaks, the non-profit and transparency organisation to read about the leaks and top secrets of this world.
And now Julian Assange, the founder...
Apple refused to unlock the iPhone on the enforcement of U.S Federal Judge
Once again the tech giant Apple has proved that how much they are concerned about the privacy of its users, and they will never break the users’ security for...
Google is going to mandate the Full Disk Encryption by default for devices with...
Last year when Google launched Android Lollipop 5.0, Google wanted to make the full disk encryption mandatory, but due to some reasons the idea didn’t work.
But this time with...
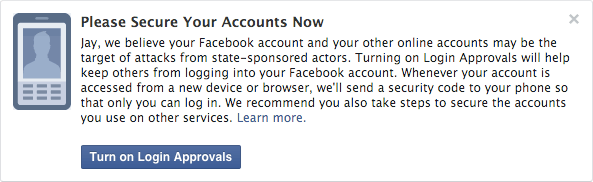
Facebook’s New Notification Feature: Facebook will now Notify you if Government is Spying on...
Yet another feature by Facebook to make the world’s largest social network more secure. Facebook has just launched a new Notification feature that will alert you if it believes...
ISIS Hacker Arrested In Malaysia: US Military Data Hacked By ISIS Hacker
A Kosovo citizen is arrested by Malaysian Authorities in the charges of computer hacking and providing the personal data of U.S. Military members to the Islamic State terrorist group...
Radio Wave Hack: It allows the hacker to control your phone from 16 feet...
Every day we get to know about a different hack and every hack has its own dependencies and capabilities.
Now, this is crazy. Security researchers have discovered a new hack...
A new Zero-Day vulnerability in recently patched Flash Player
It seems to be no benefits of fixing the issues in its latest patch that was released by Flash Player yesterday.
Adobe is trying its best to make the Flash...
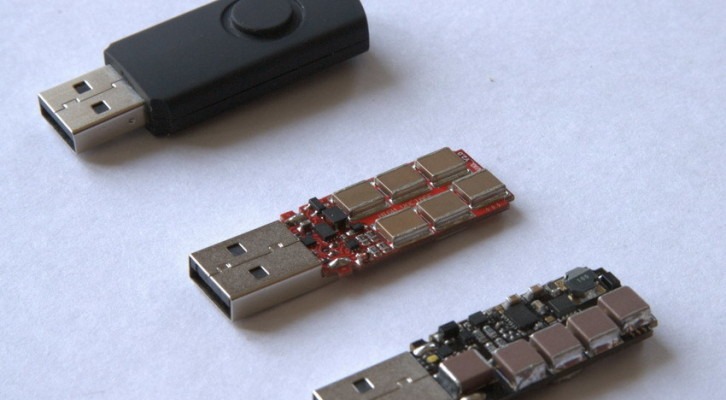
USB Killer 2.0 : It can destroy your system in just some seconds
Do you remember Killer USB? It is about the new version of Killer USB, this time with tremendous powers.
Let’s talk a bit about the previous version of Killer USB,...
Apple Removed malicious Apps from App Store: Apps were installing the Root Certificates to...
Apple has recently removed some malicious apps from its App Store. According to Apple there were some apps on the App store that have the ability to negotiate encrypted...
Obama Encryption Policy: Are they violating the definitions of Security, Privacy and Encryption?
Obama Encryption Policy
As the consequences of exposure that Edward Snowden made about NSA, the citizens of USA are now demanding for more transparent security.
From last some days citizens of...
China Helped U.S.A: China Arrested Hackers on the Request of U.S Government.
China Arrested Hackers on the Request of U.S Government
The things happen in movies can actually happen in the real life too. The recent action of China reminds me of...
NETGEAR Router Exploit: Critical Bug in NETGEAR Router
Do you use NETGEAR Router, then have a look at it.
NETGEAR Routers are once again vulnerable to the DNS Monitoring. A security researcher discovered that there is a serious...
WordPress XML-RPC: Brute Force Amplification Attack
It is always interesting to hear about the bugs in world’s most famous systems, this time it is WordPress. Yes the world’s most famous content management system is vulnerable...