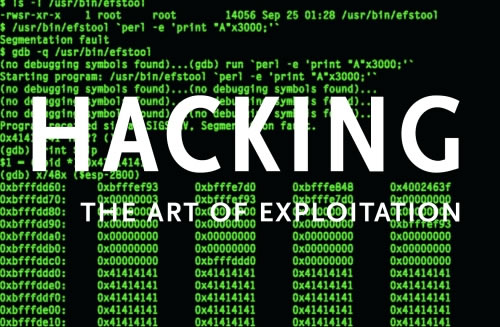
Hack WPA2 Encrypted Wi-Fi Networks using Aircrack-ng
Hack WPA2 Encrypted Wi-Fi Networks using Aircrack-ng | Kali-Linux
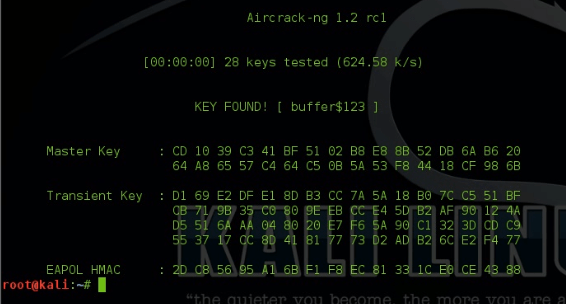
Hello friend ,In this article I will demonstrate how to crack or hack some one's WiFi Network just in simple steps...
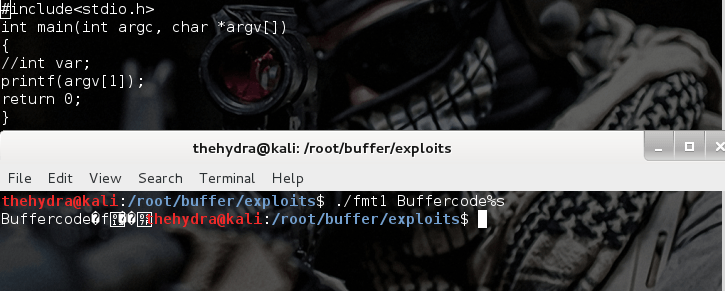
Format string exploits
Format string exploits became public in late 2000. It is easy to find errors in format string in comparison of buffer overflows. Once errors are spotted, they are usually...
PentestBox: A Portable Penetration Testing Distribution for Windows Environments
Download SourceForge Download Torrent
PentestBox is a...
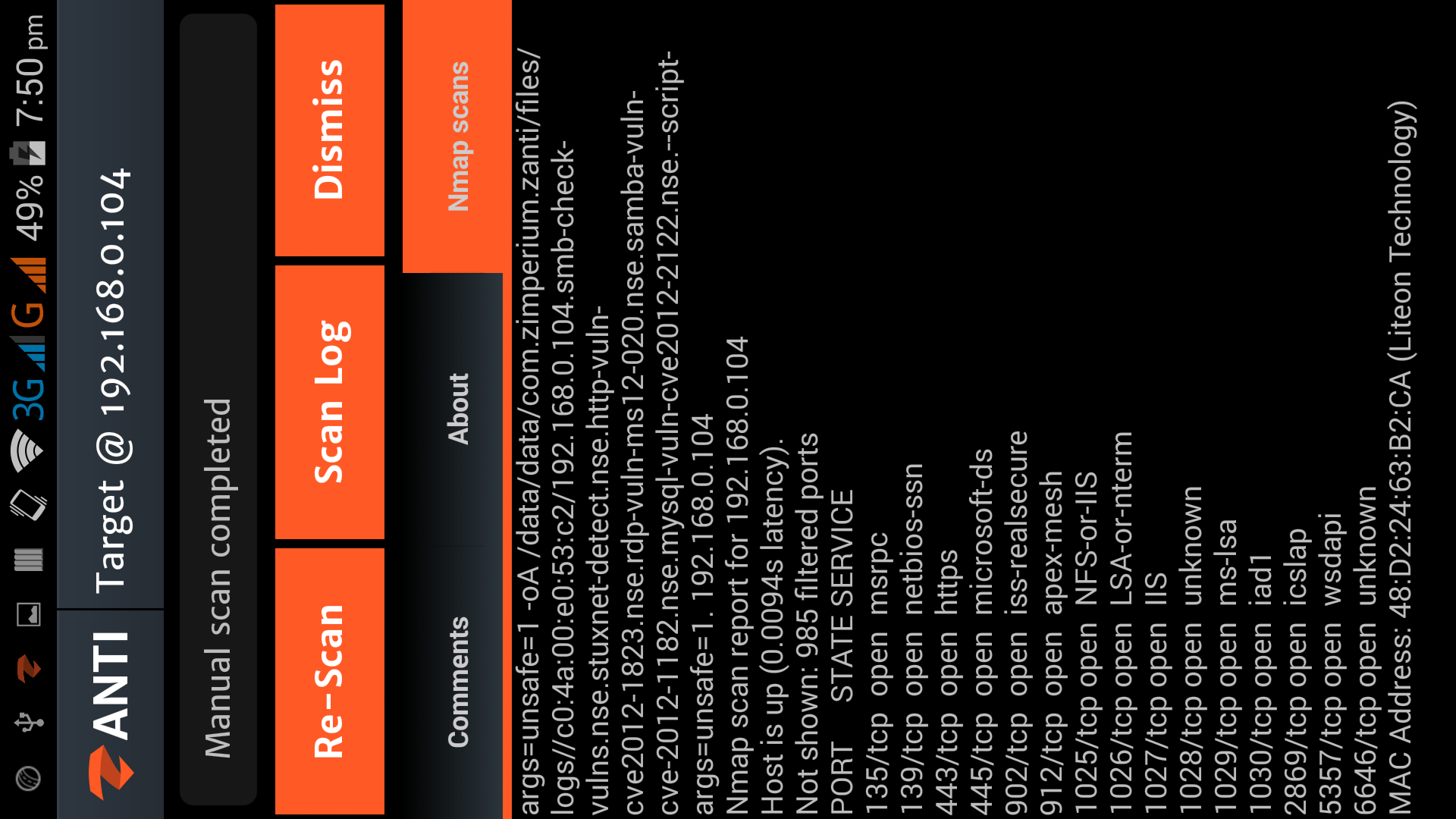
Hacking with Android Smartphone using zANTI2
Download zANTI 2.2(Apk)
Hacking with Android Smartphone using zANTI2
zANTI2 is a Network Analysis and penetration suit developed by ZImperium family as a software developer and researcher, the name zANTI2 comes...
Explore into the Metasploit ( a Ultimate Hackers Tool)
Metasploit is a complete and a Ultimate Security tool that provides information about Computer Security Vulnerabilities and also use in penetration testing .It was develop by HD Moore in...
Exploit Development Process:Moving towards Real world Hacking
Now that we have covered basics of exploit , you are ready to look at real world examples like metasploit . As you all know - vulnerabilities in real...
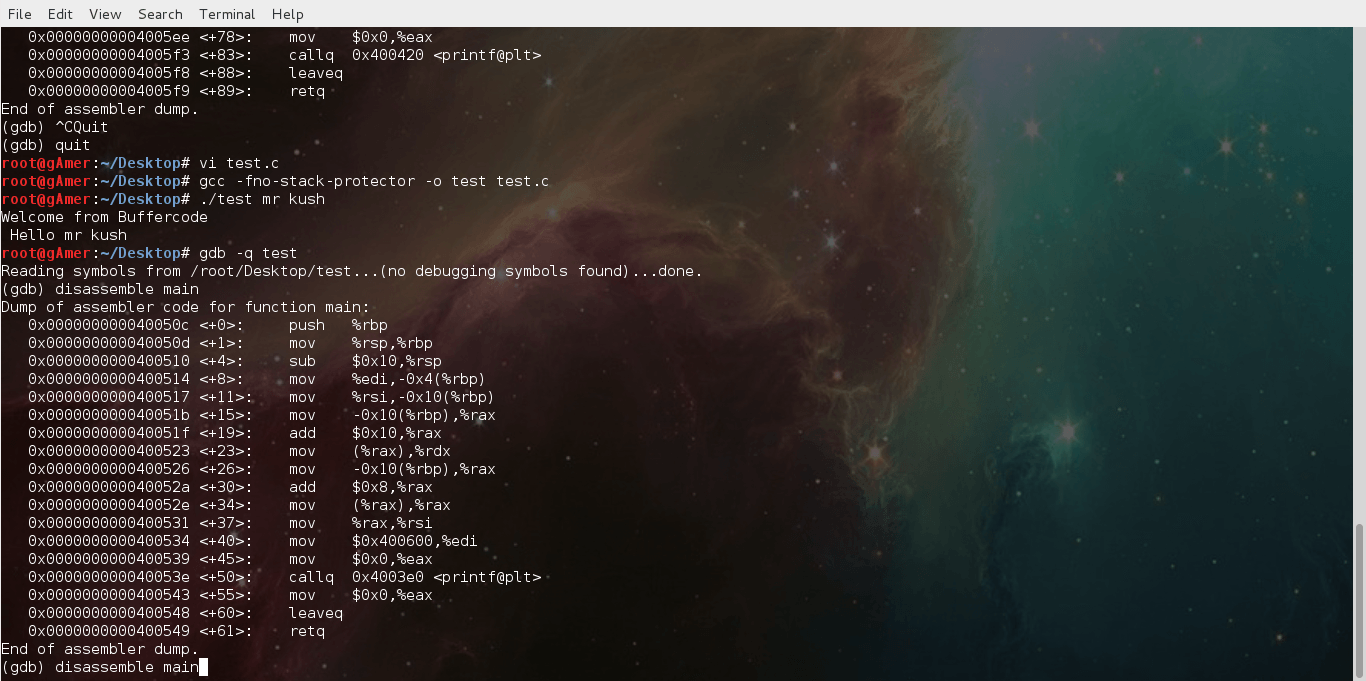
Exploit using shell code from command line
After reading our previous post:Exploiting buffer overflows using command line it's time to do Exploit Shell code using Command-line but I think you do want to clear your doubt...
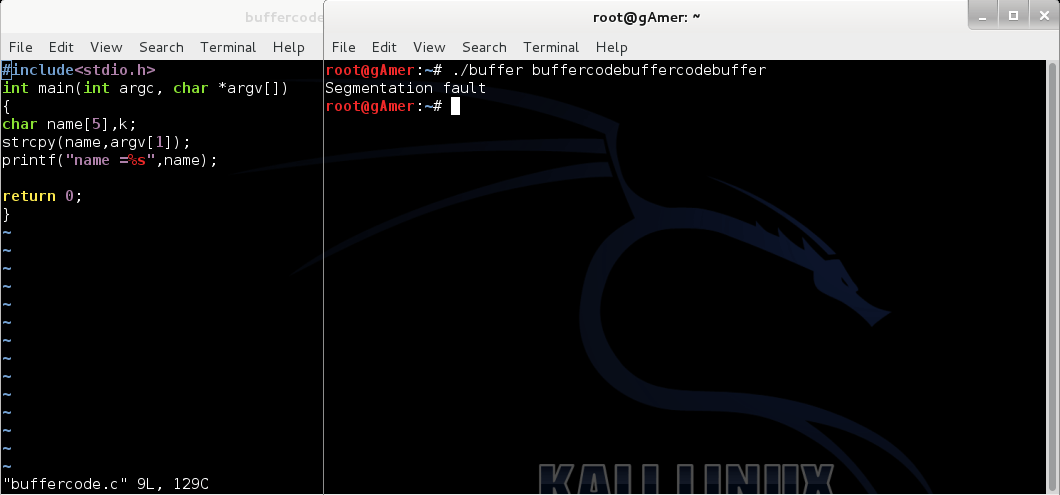
Exploiting buffer overflows using command line
After reading our previous post: Next step moving towards exploit:Finding the return address ,it's time to do some command line exploits. So this post is regarding Exploiting buffer...
Next step towards exploit : finding the return address
Hey friends , I think it's the time to take next step towards exploit after reading our all previous posts . In this tutorial you will learn about :...
Important things to do after installing Kali Linux
There are small set of important softwares that are required after installation of Kali Linux. Linux operating system is not too much user friendly but it is highly flexible...
Complete Guidance to Install Kali linux in Dual Boot Mode without any Problem
Before start Complete Guidance to Install Kali linux in Dual Boot Mode without any Problem remember it's slogan:-
The Quiter you become ,the more you are able to hear
Do you...
Malware Attack on Facebook effect more than 110,000 users
Malware attack on Facebook
On Friday malware attack on Facebook is reported. Malware attack on Facebook infected more than 110,000 users. There are some pornography links on Facebook. When user click...
Mozilla Placing High Bandwidth Tor Middle Relays
Mozilla Placing High Bandwidth Tor Middle Relays
Mozilla Placing High Bandwidth Tor Middle Relays to add more secure anonymity in Firefox. Tor and Mozilla working together to provide a more...
Google reveals three Apple OS X zero-day flaws
Once again Google proved that they have strong security team which can expose not only Microsoft vulnerabilities but Apple OS X can also stand in the same category. Google expose...
How to get into friends whatsapp and send messages
I don't know that how to Express this success !!! Everybody knows that hacking is just a creativity and finding the way to get deeper into the code. So...
Recently Whatsapp Banned users for using Whatsapp Plus Application
OOOOhh cut off with friends due to using watsapp plus :(
i missed my friends , my watsapp plus stop working :`(
...
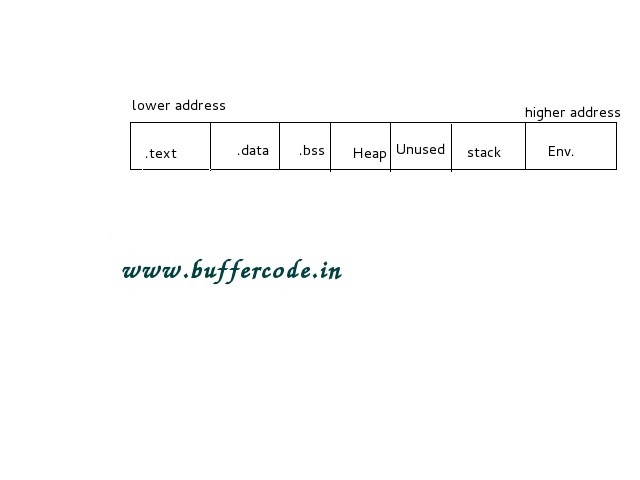
Memory management in C Programming:Computer Memory
Memory management in C is one of the important topic as it's not only about memory management in c but also about Computer Memory Management. In this section you...
Vulnerability in PayPal user authentication system
It's always a matter of attraction when money is in the frame of attack. So It's time to get into the users PayPal account.. Paypal provides online / ebay...
Basic Linux Exploits: Moving towards exploits
Note: Hacking is not a joke so please keep patience and learn it step by step.
If you have read all our previous posts , you are ready to exploits the...
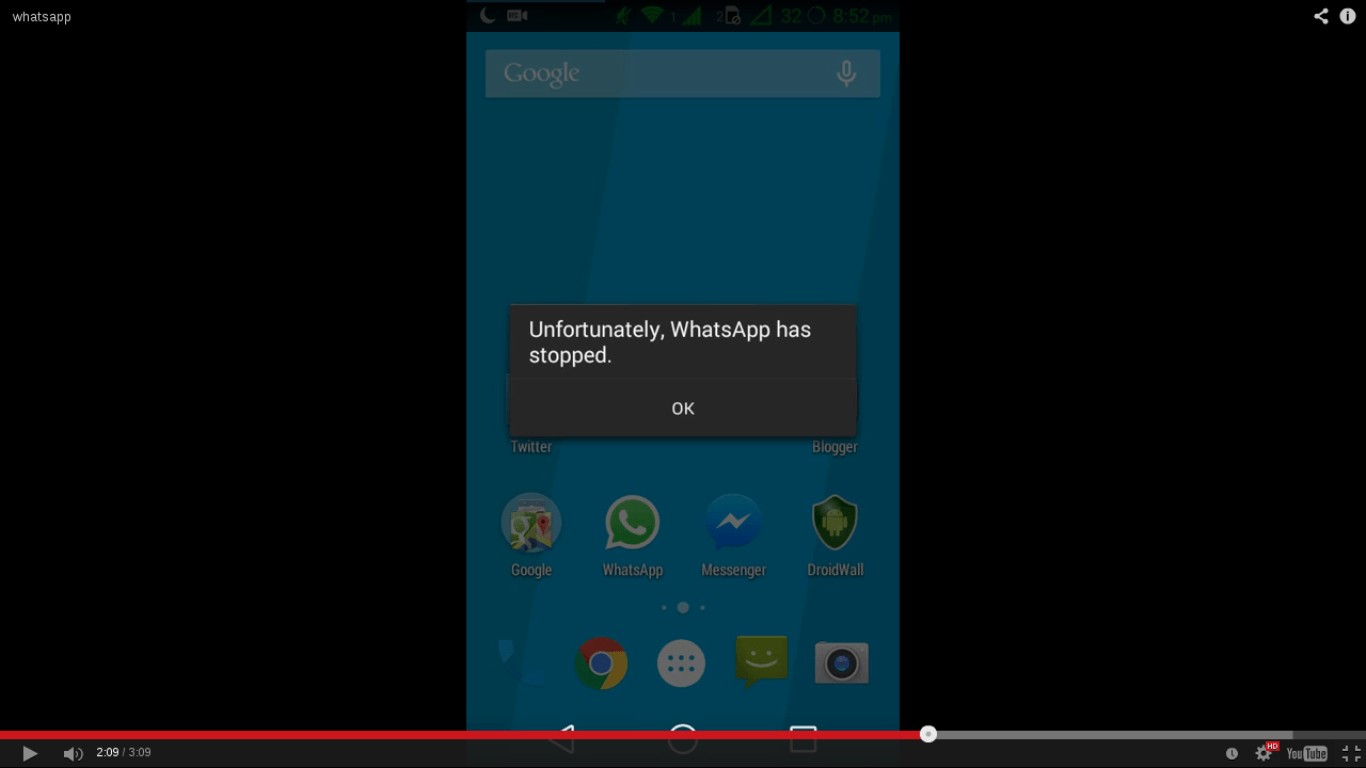
Crash friends whatsapp by sending 200 kb message
To Download Special characters Click Here
This time again!!! Indian teenagers just do the magic ;) They again find a bug in whatsapp which is recently purchased by facebook in...
Basic Linux exploits: Function Calling Procedure
Note: Hacking is not a joke so please keep patience and learn it step by step.
Note: Before reading this post you must read :
Learn hacking...
Basic Exploits : Stack Operations
Note: Hacking is not a joke so please keep patience and learn it step by step.
Stack Operations
First and the most important topic to learn the basics of Exploits is...
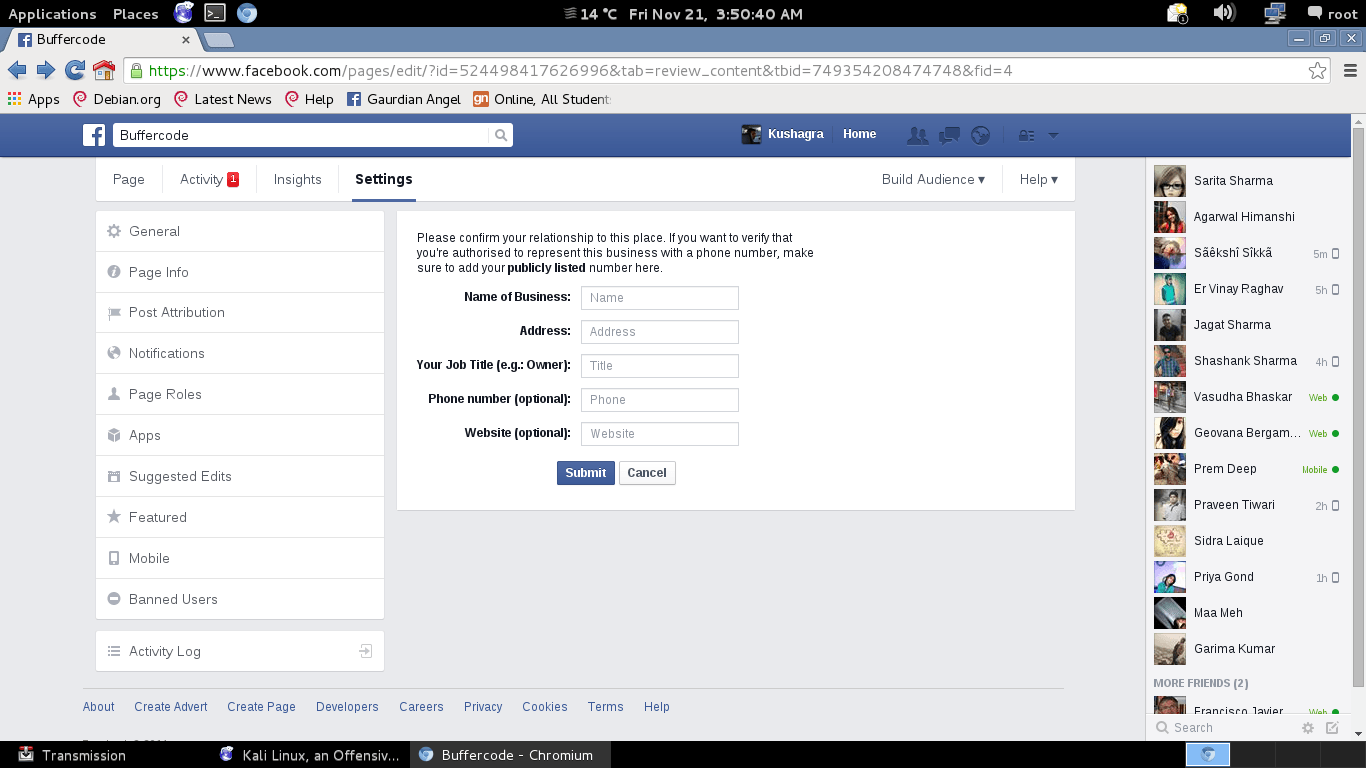
Facebook verification page has bug found by team Buffercode
Note: I already send report for this bug , I hope Team Facebook will change their algorithm for this page.
New Bug has found by team Buffercode in Facebook
It's always...
Now facebook introduced new “Facebook groups app” on 18 November
Facebook groups app for facebook lovers:
Peoples use facebook to keep contact with friends and family who may live far from them or not. To keep in contact with friends...
How to secure your account from phishing attacks on Internet
Note: Instead of using backtrack use Kali Linux | Rebirth of BackTrack, the Penetration Testing
Creating Phishing page to know the safety cautions
on Internet
To know the cautions we must know...
Basic Linux Exploits:Make your Pc more secure
Basic Linux Exploits:Make your Pc more secure and learn the basics of computer world
Why study Exploits?
Before learning exploits ,one should know about vulnerability.What does it means in the world...